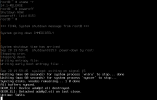
Apologies if the title was vague, I'll try my best to explain. I'm new to the UNIX booting process and the components of such systems at this level.
Resources I'm using:
I get stuck after this every time because almost every guide now tells me to edit /etc/fstab and /boot/loader.conf, both of which are on the ISO (which is read-only, as the error that I get rightly says). I tried copying over loader.conf to /mnt/boot but that doesn't seem to do anything.
What do I do now? I feel like I'm missing some fundamental knowledge of the FreeBSD booting process which is the reason I'm stuck here. I would like to stick with the more traditional
Could someone also answer a question of mine while they're at it? From what I understand, the UEFI of the motherboard (or in this case, whatever my virtualization solution uses) looks for a FAT32 formatted GPT partition with a certain label (
Thanks!
Resources I'm using:
- https://forums.freebsd.org/threads/...stallation-how-to-with-video-if-needed.83934/
- https://www.c0ffee.net/blog/freebsd-full-disk-encryption-uefi
- https://forums.freebsd.org/threads/...oot-with-encrypted-zfs-root-using-geli.51393/
- View: https://www.youtube.com/watch?v=s1WvmIW_b8o
- https://docs.freebsd.org/en/books/handbook/bsdinstall/#bsdinstall-part-manual
- https://docs.freebsd.org/en/books/handbook/boot/#boot-introduction
sh:
# Clean up if any partitions exist
gpart destroy -F ada0
gpart create -s GPT ada0
# Add EFI partition
gpart add -t efi -a 4K -s 100M -l EFI ada0
newfs_msdos -L EFI ada0p1
# ADD UFS boot partition
gpart add -t freebsd-ufs -a 4K -s 512M -l UFSBOOT ada0
newfs -L UFSBOOT ada0p2
# Create GELI-encrypted rootfs with just password
gpart add -t freebsd-ufs -a 4K -l ROOTFS ada0
geli init -b -e AES-XTS -l 256 /dev/ada0p3
geli attach /dev/ada0p3
newfs -L ROOTFS /dev/ada0p3.eli
# Mount partitions
mount -t ufs /dev/ada0p3.eli /mnt
mkdir -p /mnt/boot/
mount -t ufs /dev/ada0p2 /mnt/boot
mkdir -p /mnt/boot/efi
mount -t msdosfs /dev/ada0p1 /mnt/boot/efi
mkdir -p /mntboot/efi/EFI/BOOT
cp /boot/loader.efi /mnt/EFI/BOOT/BOOTX64.EFI
cp -r /boot/* /mnt/boot/
cd /mnt
tar xvJf /usr/freebsd-dist/base.txz
tar xvJf /usr/freebsd-dist/kernel.txz
tar xvJf /usr/freebsd-dist/src.txz
# Create fstab entries to mount both rootfs and boot partition
rm /tmp/bsdinstall_etc/fstab
echo "/dev/ada0p3.eli / ufs rw,ealgo=AES-XTS,len=256 0 0" >> /tmp/bsdinstall_etc/fstab
echo "/dev/ada0p2 /boot ufs rw 1 1" >> /tmp/bsdinstall_etc/fstabI get stuck after this every time because almost every guide now tells me to edit /etc/fstab and /boot/loader.conf, both of which are on the ISO (which is read-only, as the error that I get rightly says). I tried copying over loader.conf to /mnt/boot but that doesn't seem to do anything.
What do I do now? I feel like I'm missing some fundamental knowledge of the FreeBSD booting process which is the reason I'm stuck here. I would like to stick with the more traditional
/boot and / and use UFS, but other than that I don't have many preferences.Could someone also answer a question of mine while they're at it? From what I understand, the UEFI of the motherboard (or in this case, whatever my virtualization solution uses) looks for a FAT32 formatted GPT partition with a certain label (
/dev/ada0p1 in my case). Once it does find it, does it then start looking for a loader.conf? And how would it find this file if the partition isn't even mounted on to /boot yet? And that isn't possible unless the "root" partition is also mounted (unless I missed something). I am really confused now Thanks!