Suggestion: Configure two different routing tables with setfib(1)
I know from your other posts you had been trying to avoid using multiple routing tables, but in this case it sounds like it might be a good option.
setfib(1) allows you to have multiple routing tables and you can specify which one you want to use for each jail (see also the man page for
setfib(2) to configure options in your kernel or
/boot/loader.conf).
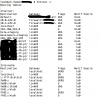
Your production jails and staging systems (in which I'm including your host system, which you said also has an IP on the 192.168.123.0/24 network) have different routing requirements. The default route for your production systems needs to be via your public gateway, whereas the default route for your staging systems needs to be via the pfSense box, which can then handle NAT routing to the Internet.
The ezjail configuration file has a configuration option for specifying which routing table to use (
jail_${jail_name}_fib if I remember correctly), which is equivalent to setting the
exec.fib parameter in
jail.conf(5) for a non-ezjail jail.
Option involving no static routes
With the default gateway of your staging systems being the pfSense box, I don't believe you would need static routes on either your staging systems or the pfSense box. The pfSense box has addresses on the 10.0.123.0/24 network (for your VPN) and also the 192.168.123.0/24 network (for your staging systems), so the pfSense's routing tables will be automatically populated to route traffic between these two networks. Anything else would be routed out via NAT to the public Internet. I'll caveat this by saying that I don't use pfSense so I'm not sure what special configuration (if any) it requires.
With the default gateway of your production jails being your public gateway, these can respond appropriately to incoming requests without issue via this default route. For remote access from your VPN, you could connect via
ssh(1) to your host system (on the 192.168.123.0/24 network) then attach to your jails with
ezjail-admin console <jailname> or with
jexec(8). This wouldn't require any static routes.
Option to allow direct SSH connections to production jails from the VPN
If you wanted to connect with
ssh(1) directly to your production jails via the VPN, a reasonable option would be to assign them an address on an interface connected to the 192.168.123.0/24 network as well as their public IP. In my opinion it would be better to run your SSH servers listening only on the private addresses so they can be accessed via the VPN but not from the public Internet. You would then need to configure a static route so that the production jails route traffic for the 10.0.123.0/24 network (for VPN connections) via the pfSense box.
Does that make sense? I hope I've understood your network and requirements correctly
 Edit: Various typo corrections
Edit: Various typo corrections