I just did a fresh install of FreeBSD 13.1 with ionos.com cloud host. I cannot seem to ssh into the server at all, and it's driving me nuts (I've called ionos support probably 8 times today and they're stumped too). Here's what I have so far...
- I can access my server via KVM console
- Here is my /etc/rc.conf file:
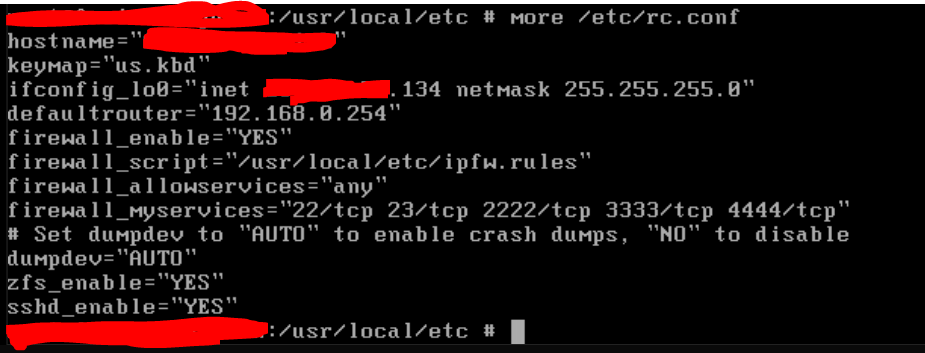
- Here is my /usr/local/etc/ipfw.rules file:
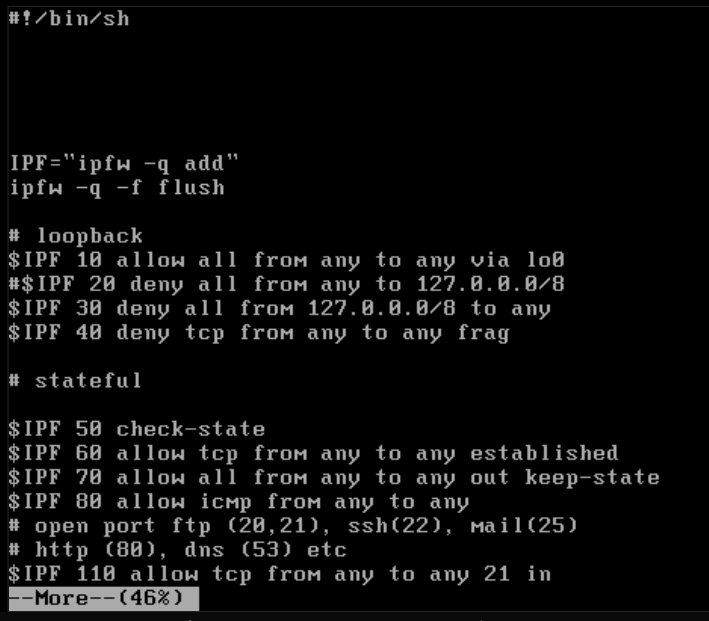
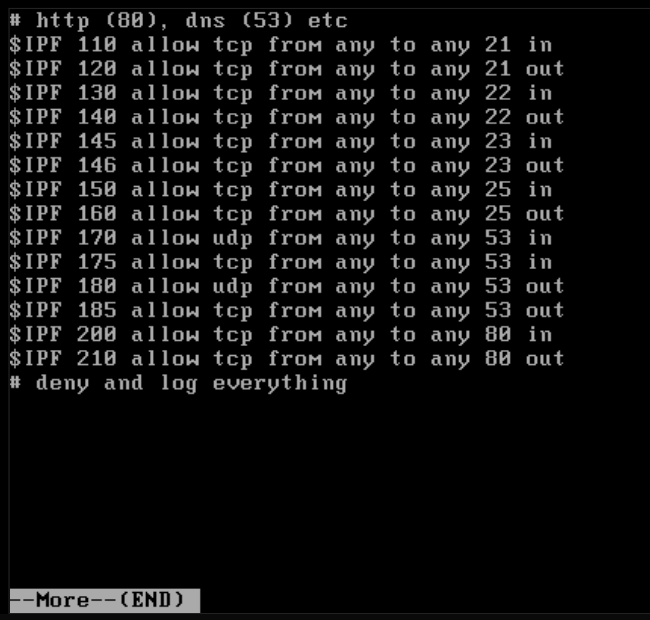
- Here is my ifconfig output:
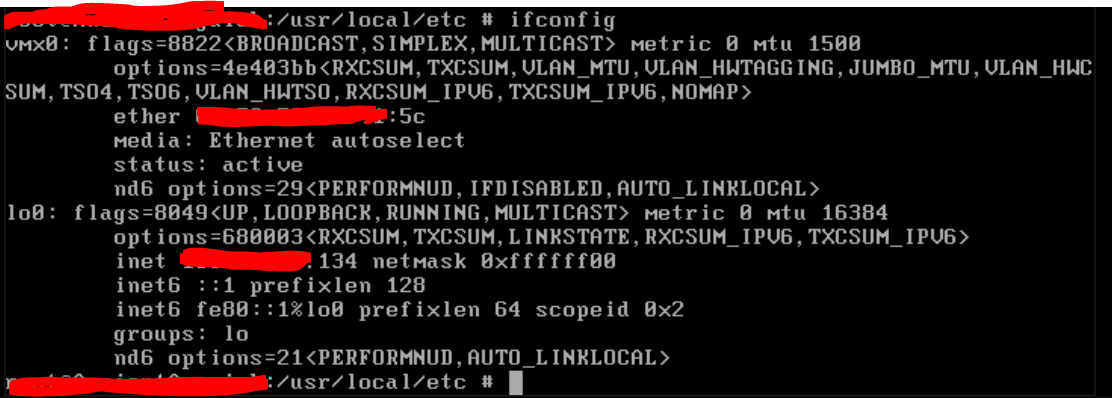
I've confirmed with my host that there are no firewall policies on their end that are blocking connections. I've also confirmed that the support agent is getting blocked, so it's not specific to me. They also booted the machine with a different image to confirm the network connection was fine, so it's "definitely" some sort of configuration setting on my FreeBSD server itself.
Added context: I would consider myself "intermediate" in this space. I've done some rather complex things, imo, but I'm self taught, so there are a LOT of basic things in Linux that are still over my head. Mostly I'm just good a google, but alas my efforts have failed me for the last 10+ hours between yesterday and today.
My goal here is simply to access the machine via putty/ssh client.
Any help here would be very greatly appreciated!
- I can access my server via KVM console
- Here is my /etc/rc.conf file:
- Here is my /usr/local/etc/ipfw.rules file:
- Here is my ifconfig output:
I've confirmed with my host that there are no firewall policies on their end that are blocking connections. I've also confirmed that the support agent is getting blocked, so it's not specific to me. They also booted the machine with a different image to confirm the network connection was fine, so it's "definitely" some sort of configuration setting on my FreeBSD server itself.
Added context: I would consider myself "intermediate" in this space. I've done some rather complex things, imo, but I'm self taught, so there are a LOT of basic things in Linux that are still over my head. Mostly I'm just good a google, but alas my efforts have failed me for the last 10+ hours between yesterday and today.
My goal here is simply to access the machine via putty/ssh client.
Any help here would be very greatly appreciated!

