It seems I have waited too long to upgrade my OS.
The quick question is: Are there pre-written instructions somewhere that address the land between:
A) semi-automated upgrading (per Handbook Ch 26,
... and ...
B) those who build kernels (per Handbook Ch 26.6, which is not where I really want to go, if I can avoid it)?
If so, I haven't been able to find it.
My thinking is, "if I could install FreeBSD the first time by downloading files to a stick and installing (without overtly building a kernel), then 'I would have thought' there is something similar for upgrades where I can download and not build a kernel" (perhaps also from a stick, if necessary).
REWIND...
FreeBSD is a file server that "just works," so it doesn't demand my attention for upgrading the way my kids' Windows PCs do when they're interactive daily or a new game doesn't work, etc. I have plenty to do IRL anyway. So, in the year it took me to prep & sell a house, search & buy a house, move & settle in, my FreeBSD server chugged along without much attention paid to it.
Now I find myself in a place where v12 is in the rear view mirror and 13.2, 13.3 (very recent), and 14.0 are what's available.
And
'I would have thought' (love that thread) since 13.2 is currently a supported release, then
So is "by source" the only real upgrading option here? (besides a complete reinstall, of course)
In any case, while I am technical, I also don't want this task to become anymore more time-consuming than it has to be. I'm perfectly happy with the vanilla kernel. After skimming ch26.6, I'm just afraid all the necessary reading/research and potential pitfalls involved in building a kernel for the first time are going to be time-eaters ... thus, my avoidance. So if I did indeed miss my window for "easy," what's the next easiest path? Or is ch26.6 the only real choice?
Thanks all!
WG
The quick question is: Are there pre-written instructions somewhere that address the land between:
A) semi-automated upgrading (per Handbook Ch 26,
freebsd-update, etc.)... and ...
B) those who build kernels (per Handbook Ch 26.6, which is not where I really want to go, if I can avoid it)?
If so, I haven't been able to find it.
My thinking is, "if I could install FreeBSD the first time by downloading files to a stick and installing (without overtly building a kernel), then 'I would have thought' there is something similar for upgrades where I can download and not build a kernel" (perhaps also from a stick, if necessary).
REWIND...
FreeBSD is a file server that "just works," so it doesn't demand my attention for upgrading the way my kids' Windows PCs do when they're interactive daily or a new game doesn't work, etc. I have plenty to do IRL anyway. So, in the year it took me to prep & sell a house, search & buy a house, move & settle in, my FreeBSD server chugged along without much attention paid to it.
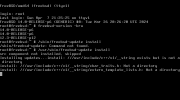
uname -a
FreeBSD xxxx.home 12.2-RELEASE FreeBSD 12.2-RELEASE r366954 GENERIC amd64Now I find myself in a place where v12 is in the rear view mirror and 13.2, 13.3 (very recent), and 14.0 are what's available.
And
freebsd-update -r 13.3-RELEASE upgrade gives me:
Code:
src component not installed, skipped
Looking up update.FreeBSD.org mirrors... 3 mirrors found.
Fetching metadata signature for 12.2-RELEASE from update1.freebsd.org... failed.
Fetching metadata signature for 12.2-RELEASE from update2.freebsd.org... failed.
Fetching metadata signature for 12.2-RELEASE from dualstack.aws.update.freebsd.org... failed.
No mirrors remaining, giving up.
This may be because upgrading from this platform (amd64)
or release (12.2-RELEASE) is unsupported by freebsd-update. Only
platforms with Tier 1 support can be upgraded by freebsd-update.
See https://www.freebsd.org/platforms/index.html for more info.
If unsupported, FreeBSD must be upgraded by source.'I would have thought' (love that thread) since 13.2 is currently a supported release, then
freebsd-upgrade from all 12.x releases would still be supported until one-major-release-up-13 is completely retired. That's what WiiGame-before thought until failing and researching this. WiiGame-after is now thinking that is not the case, for whatever reason.So is "by source" the only real upgrading option here? (besides a complete reinstall, of course)
In any case, while I am technical, I also don't want this task to become anymore more time-consuming than it has to be. I'm perfectly happy with the vanilla kernel. After skimming ch26.6, I'm just afraid all the necessary reading/research and potential pitfalls involved in building a kernel for the first time are going to be time-eaters ... thus, my avoidance. So if I did indeed miss my window for "easy," what's the next easiest path? Or is ch26.6 the only real choice?
Thanks all!
WG