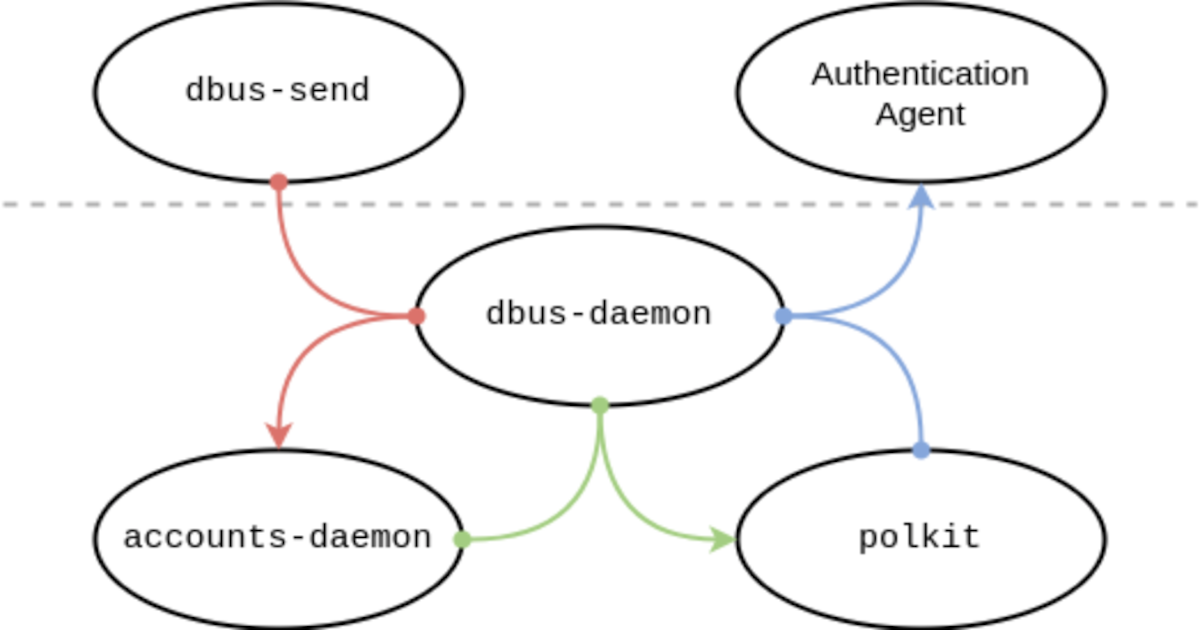
Indeed. Even PCManFM drags it in for something as trivial as the recycle bin functionality. For a light file manager use-case, the author made an error here. For our virtual desktop system I ripped it out and patched in my own solution. Purposely not following the freedesktop specifications.I consider devel/gvfs an annoyance.