Netcraft has found that Halifax has been left vulnerable to convincing impersonation attacks for five years. The operator of a website promoting Spanish hotels is able to send and receive emails on the official Halifax online banking domain, and get legitimate security certificates issued for the same domain.
Halifax Online
Halifax operates its online banking service on a separate domain (halifax-online.co.uk) to its main website (halifax.co.uk).
The entry point to Halifax's banking service is via www.halifax-online.co.uk. Visitors to the site without the www. prefix are presented with a browser error.

halifax-online.co.uk
The mail server configuration of halifax-online.co.uk domain is configured in such a way that makes it open to attack.
MX records
A Mail Exchanger (MX) record publishes the location where email should be sent to for addresses on that domain. For example, Netcraft’s own MX records point to mail.netcraft.com. Any system wanting to send email to info@netcraft.com would look up the MX record for netcraft.com, and see they need to forward the email to mail.netcraft.com.
It is common for many domain name owners to delegate its mail processing to a third-party service; Microsoft and Google are notable providers. In the case of halifax-online.co.uk, the MX records point to mail.btwebworld.com.
BT WebWorld
BT WebWorld was a B2B web host and email service offered by BT. BT WebWorld launched in October 1996 and was discontinued in 2013/2014. During its heyday, BT WebWorld was a popular hosting provider used by many British SMEs and large organisations.
The domain name, btwebworld.com, continued to belong to BT until 2015, at which time the domain registration lapsed. It was then registered by an unaffiliated party on 22nd November 2015, and presently redirects to a hotel-themed website. Some of the original BT WebWorld website content has been copied on to this website. This is likely an attempt by the operator of the website to appear more genuine to search providers, in the hopes of increasing visibility in search results.
Metadata for the IP Address used by btwebworld.com indicates the server is located in Dominica. However, tracing the IP Address shows the server is probably located on the east coast of America. The stated location of the IP Address may have been chosen in an attempt to place the website outside the jurisdiction of certain law enforcement agencies.
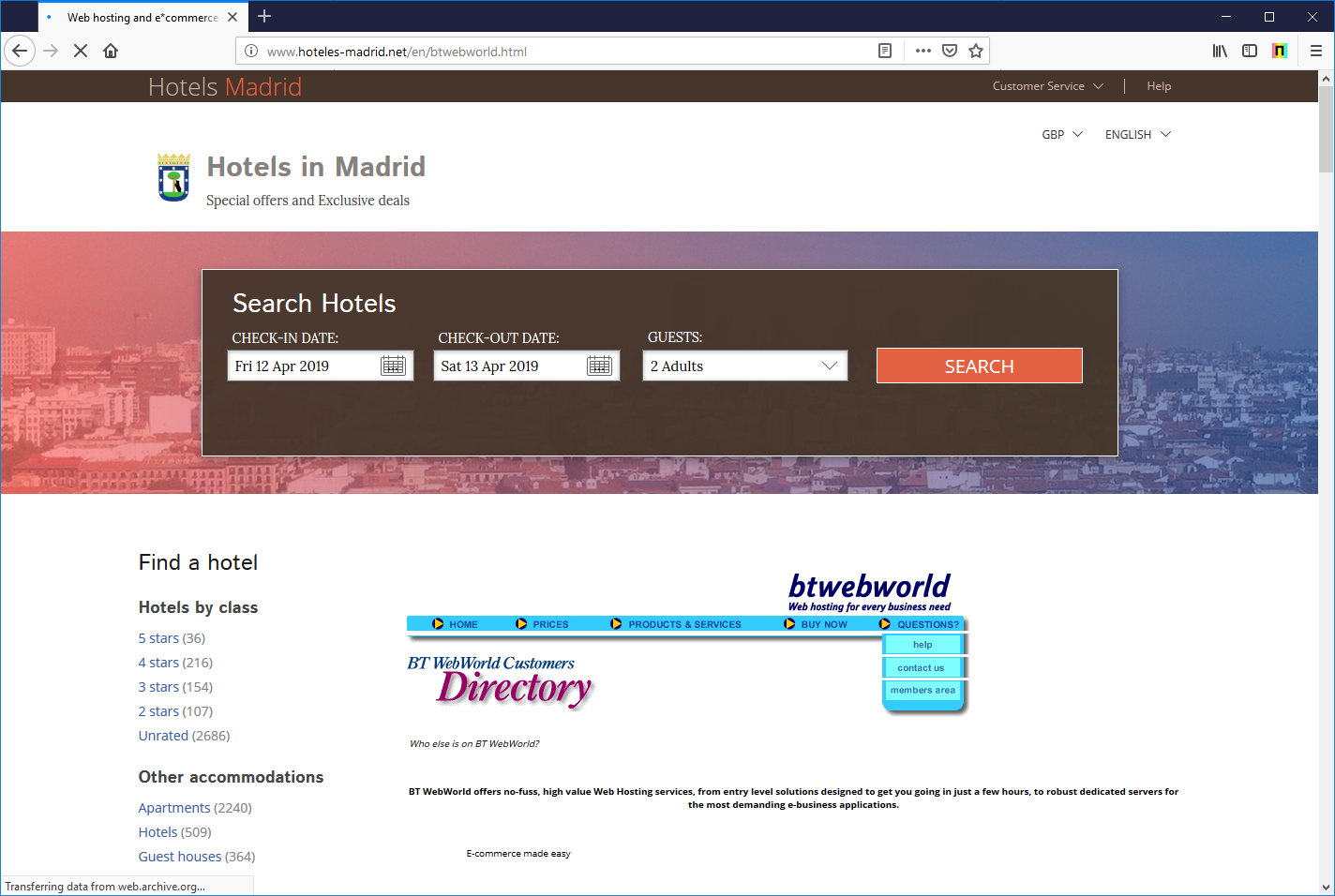
Screenshot of btwebworld.com
Why is this a concern?
Any Halifax customer aware of the halifax-online.co.uk website would unlikely be concerned if they received an email appearing to be from halifax-online.co.uk, and could be tricked into sending sensitive information to email accounts on the same domain.
Inconsistent configuration of Halifax’s SPF record increases the chance that fraudulent emails purporting to be from halifax-online.co.uk do not get sent to the ‘spam’ folder, and Halifax would not be alerted to spoofed emails.
Being able to receive email at @halifax-online.co.uk addresses also allows the domain owner to request TLS certificates for the official Halifax online banking domain. This would allow a fraudster to create convincing impersonations of the Halifax website.
SPF
Sender Policy Framework (SPF) is a mechanism that allows a domain name owner to assert control over which servers are permitted to send email from that domain.
An SPF record includes a list of IP Addresses that are allowed to send email for the domain, and an instruction informing email servers how to process email they receive which does not originate from one of the allowed IP Addresses. When a mail server receives an email, the mail server may perform a lookup of the SPF record for the associated domain to determine whether the email is genuine.
A misconfigured SPF record can be advantageous to fraudsters. Email that is permitted by an SPF record is more likely to land in the user’s inbox. Email not permitted is more likely to land in the ‘spam’ folder, or not even get delivered.
The SPF record for halifax-online.co.uk instructs mail servers to only allow email from IP Addresses in its MX record, which in this case is btwebworld.com.
The owner of btwebworld.com — or any sites that share the same email server — would be able to successfully send email from @halifax-online.co.uk addresses, even to email servers which perform checks on SPF records.
TLS Certificates
In order to obtain a certificate issued for a website and appear ‘secure’ the owner of that website needs to prove to a Certificate Authority that they have control over the website. One common method is to prove that you can receive emails sent to a special email address on the domain.
Certificate Transparency (CT) is an initiative where Certificate Authorities publish certificates they issue. This allows unauthorised certificates to be identified. The authorised party could then request the certificate be revoked — although most browsers do not check if certificates have been revoked. It could also request the unauthorised website be taken offline. Providing evidence that the certificate has been included in a CT log is only a requirement for the Chrome browser and recent versions of iOS.
This kind of attack could be partially mitigated through the use of Certificate Authority Authorization (CAA) records. These records allow the domain owner to list the set of Certificate Authorities that are permitted to issue certificates for sites on that domain. There is no CAA record on halifax-online.co.uk.
The end result is that it would be possible for the owner of btwebworld.com to request — and be issued with — a valid certificate for the official Halifax online banking website. The owner could request the certificate from a Certificate Authority that does not require certificates they issue to be logged, reducing the chance of discovery, and would, at least for a significant proportion of web users, appear in the web browser as ‘secure’.
Combined with another attack, such as man-in-the-middle, it would be trivial for a fraudster to create a highly convincing impersonation designed to capture banking credentials of Halifax customers.
Who else is affected?
Netcraft found 131 other domains that still point its MX records at btwebworld.com, including three other Halifax domains, the primary domain of BT’s own BT Wholesale division, 13 domains owned by investment bank Rothschild & Co, a domain for UK insurance company esure, a sub-domain of the NHS, and a domain belonging to soft-drinks company Robinsons.
Netcraft has also found that www.e-commerce.bt.com and www.btbroadband.com both resolve to the same IP Address as btwebworld.com. The owner of this IP Address would be able to set up a phishing attack against BT under an official BT domain.
Remediations
Halifax can make simple changes to their DNS in order to protect itself and its customers from impersonation attacks:
Netcraft has found 171 phishing attacks impersonating Halifax over the past 12 months.
Netcraft offers a range of services to protect organisations against cybercrime, including monitoring of DNS for look-a-like domains, SPF record auditing, and processing DMARC email reports.
Continue reading...
Halifax Online
Halifax operates its online banking service on a separate domain (halifax-online.co.uk) to its main website (halifax.co.uk).
The entry point to Halifax's banking service is via www.halifax-online.co.uk. Visitors to the site without the www. prefix are presented with a browser error.

halifax-online.co.uk
The mail server configuration of halifax-online.co.uk domain is configured in such a way that makes it open to attack.
MX records
A Mail Exchanger (MX) record publishes the location where email should be sent to for addresses on that domain. For example, Netcraft’s own MX records point to mail.netcraft.com. Any system wanting to send email to info@netcraft.com would look up the MX record for netcraft.com, and see they need to forward the email to mail.netcraft.com.
It is common for many domain name owners to delegate its mail processing to a third-party service; Microsoft and Google are notable providers. In the case of halifax-online.co.uk, the MX records point to mail.btwebworld.com.
BT WebWorld
BT WebWorld was a B2B web host and email service offered by BT. BT WebWorld launched in October 1996 and was discontinued in 2013/2014. During its heyday, BT WebWorld was a popular hosting provider used by many British SMEs and large organisations.
The domain name, btwebworld.com, continued to belong to BT until 2015, at which time the domain registration lapsed. It was then registered by an unaffiliated party on 22nd November 2015, and presently redirects to a hotel-themed website. Some of the original BT WebWorld website content has been copied on to this website. This is likely an attempt by the operator of the website to appear more genuine to search providers, in the hopes of increasing visibility in search results.
Metadata for the IP Address used by btwebworld.com indicates the server is located in Dominica. However, tracing the IP Address shows the server is probably located on the east coast of America. The stated location of the IP Address may have been chosen in an attempt to place the website outside the jurisdiction of certain law enforcement agencies.

Screenshot of btwebworld.com
Why is this a concern?
Any Halifax customer aware of the halifax-online.co.uk website would unlikely be concerned if they received an email appearing to be from halifax-online.co.uk, and could be tricked into sending sensitive information to email accounts on the same domain.
Inconsistent configuration of Halifax’s SPF record increases the chance that fraudulent emails purporting to be from halifax-online.co.uk do not get sent to the ‘spam’ folder, and Halifax would not be alerted to spoofed emails.
Being able to receive email at @halifax-online.co.uk addresses also allows the domain owner to request TLS certificates for the official Halifax online banking domain. This would allow a fraudster to create convincing impersonations of the Halifax website.
SPF
Sender Policy Framework (SPF) is a mechanism that allows a domain name owner to assert control over which servers are permitted to send email from that domain.
An SPF record includes a list of IP Addresses that are allowed to send email for the domain, and an instruction informing email servers how to process email they receive which does not originate from one of the allowed IP Addresses. When a mail server receives an email, the mail server may perform a lookup of the SPF record for the associated domain to determine whether the email is genuine.
A misconfigured SPF record can be advantageous to fraudsters. Email that is permitted by an SPF record is more likely to land in the user’s inbox. Email not permitted is more likely to land in the ‘spam’ folder, or not even get delivered.
The SPF record for halifax-online.co.uk instructs mail servers to only allow email from IP Addresses in its MX record, which in this case is btwebworld.com.
The owner of btwebworld.com — or any sites that share the same email server — would be able to successfully send email from @halifax-online.co.uk addresses, even to email servers which perform checks on SPF records.
TLS Certificates
In order to obtain a certificate issued for a website and appear ‘secure’ the owner of that website needs to prove to a Certificate Authority that they have control over the website. One common method is to prove that you can receive emails sent to a special email address on the domain.
Certificate Transparency (CT) is an initiative where Certificate Authorities publish certificates they issue. This allows unauthorised certificates to be identified. The authorised party could then request the certificate be revoked — although most browsers do not check if certificates have been revoked. It could also request the unauthorised website be taken offline. Providing evidence that the certificate has been included in a CT log is only a requirement for the Chrome browser and recent versions of iOS.
This kind of attack could be partially mitigated through the use of Certificate Authority Authorization (CAA) records. These records allow the domain owner to list the set of Certificate Authorities that are permitted to issue certificates for sites on that domain. There is no CAA record on halifax-online.co.uk.
The end result is that it would be possible for the owner of btwebworld.com to request — and be issued with — a valid certificate for the official Halifax online banking website. The owner could request the certificate from a Certificate Authority that does not require certificates they issue to be logged, reducing the chance of discovery, and would, at least for a significant proportion of web users, appear in the web browser as ‘secure’.
Combined with another attack, such as man-in-the-middle, it would be trivial for a fraudster to create a highly convincing impersonation designed to capture banking credentials of Halifax customers.
Who else is affected?
Netcraft found 131 other domains that still point its MX records at btwebworld.com, including three other Halifax domains, the primary domain of BT’s own BT Wholesale division, 13 domains owned by investment bank Rothschild & Co, a domain for UK insurance company esure, a sub-domain of the NHS, and a domain belonging to soft-drinks company Robinsons.
Netcraft has also found that www.e-commerce.bt.com and www.btbroadband.com both resolve to the same IP Address as btwebworld.com. The owner of this IP Address would be able to set up a phishing attack against BT under an official BT domain.
Remediations
Halifax can make simple changes to their DNS in order to protect itself and its customers from impersonation attacks:
- redirect halifax-online.co.uk to www.halifax-online.co.uk to prevent visitors attempting to try alternative combinations that might lead them to fraud;
- update or remove MX records to prevent email being delivered to a non-affiliated website;
- update SPF records to deny to prevent any email being sent from halifax-online.co.uk addresses;
- add CAA records to ensure only Halifax’s chosen Certificate Authorities are permitted to issue certificates for its domains.
Netcraft has found 171 phishing attacks impersonating Halifax over the past 12 months.
Netcraft offers a range of services to protect organisations against cybercrime, including monitoring of DNS for look-a-like domains, SPF record auditing, and processing DMARC email reports.
Continue reading...
