Anticipating a surge in phishing attacks over the festive period, the Student Loans Company warned students in Britain to be on the lookout for suspicious emails. Unfortunately, some of its anti-phishing advice could have backfired, potentially increasing the risk of students falling for phishing attacks.
Warning students to be on the lookout for fraudulent emails attempting to impersonate the SLC, it told The Telegraph and Money Saving Expert that any official correspondence would come from the email address notifications@slc.co.uk. However, this advice is rather dangerous because the slc.co.uk domain has not been configured to prevent spoof emails being sent from this address.
In particular, slc.co.uk does not have a Sender Policy Framework record. SPF rules can be used to describe who can send email on its behalf, and the lack of any policy means there are no restrictions on who can send emails appearing to come from notifications@slc.co.uk.
If students infer from the SLC's advice that all emails from notifications@slc.co.uk will be legitimate, then fraudsters will be able to carry out much more convincing phishing attacks simply by spoofing emails from this address.
The domain also lacks a DMARC record, which means the SLC cannot choose what happens to forged emails that appear to come from the slc.co.uk domain. If correctly configured, such emails could not only be blocked by some email providers, but SLC would also be able to view the contents of forged emails and receive statistics to see how many are being sent.
Preventing forged emails is an important part of mitigating phishing attacks, as many attacks are initiated via email. A typical phishing email will play on the victim's sense of urgency — for example, by warning the student that his next payment may be lost or delayed if he does not update his records at the fraudster's "secure" website that masquerades as a real SLC website.
Once the victim has been tricked into visiting the phishing site, he will be prompted to enter a multitude of information which can be used to steal the loan money as soon as it arrives in his bank account. Most student loan phishing sites blocked by Netcraft usually ask for far more information than a conventional online banking phishing attack would do, capturing not just the victim's bank account details and card number, but also details about the student's university course and term time address.
Frozen phish
Despite the SLC warning of an increase in phishing attacks, it is fortunate that the fraudsters instead put an unexpected freeze on their phishing activity over the Christmas holidays. In fact, not a single student loan phishing site has been blocked by Netcraft since before Christmas day.
During 2014, Netcraft blocked more than 180 phishing URLs that impersonated the Student Loans Company or the Student Finance England service (which is run by the SLC), while SLC's fraud team took down around 150 phishing sites. Over the past three years, it claims to have prevented almost £3 million being stolen.
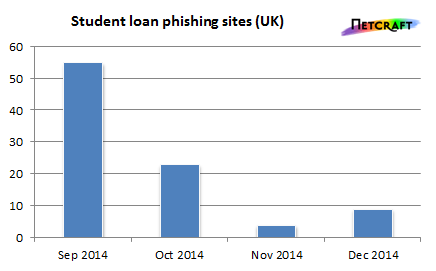
The calm before the storm that didn't happen: Most student loan phishing attacks occurred at the start of the academic year (September), and all of those carried out in December took place before Christmas day. Despite the second loan instalments being sent out this week, no attacks have taken place since.
New students make particularly attractive targets for fraudsters, as many will have no previous experience at managing their own finances. Research by the British Bankers' Association suggests that one in six of those aged 18 to 25 could be vulnerable to money transfer scams; a higher proportion than any other age group.
Student loans in the UK typically consist of a tuition fee loan – which can be up to £9,000 per year and is paid directly to a student's university or college – plus a maintenance loan of up to £7,751, which is paid into the student's own bank account, making the latter component an obvious target for phishing fraudsters.
Organisations concerned about email impersonation attacks can use Netcraft's Fraud Detection service, which processes DMARC (Domain-based Message Authentication, Reporting and Conformance) reports on your behalf. These reports are sent by ISPs and e-mail receivers when they see any emails which claim to be from one of your own domains. A web interface shows the status of all of your own domains, any configuration changes required, and highlights unprotected domains being used by fraudsters attacking your customers. Netcraft can also provide real time alerts of phishing sites targeting your company, and our takedown service can be used to remove phishing sites.
Continue reading...
Warning students to be on the lookout for fraudulent emails attempting to impersonate the SLC, it told The Telegraph and Money Saving Expert that any official correspondence would come from the email address notifications@slc.co.uk. However, this advice is rather dangerous because the slc.co.uk domain has not been configured to prevent spoof emails being sent from this address.
In particular, slc.co.uk does not have a Sender Policy Framework record. SPF rules can be used to describe who can send email on its behalf, and the lack of any policy means there are no restrictions on who can send emails appearing to come from notifications@slc.co.uk.
If students infer from the SLC's advice that all emails from notifications@slc.co.uk will be legitimate, then fraudsters will be able to carry out much more convincing phishing attacks simply by spoofing emails from this address.
The domain also lacks a DMARC record, which means the SLC cannot choose what happens to forged emails that appear to come from the slc.co.uk domain. If correctly configured, such emails could not only be blocked by some email providers, but SLC would also be able to view the contents of forged emails and receive statistics to see how many are being sent.
Preventing forged emails is an important part of mitigating phishing attacks, as many attacks are initiated via email. A typical phishing email will play on the victim's sense of urgency — for example, by warning the student that his next payment may be lost or delayed if he does not update his records at the fraudster's "secure" website that masquerades as a real SLC website.
Once the victim has been tricked into visiting the phishing site, he will be prompted to enter a multitude of information which can be used to steal the loan money as soon as it arrives in his bank account. Most student loan phishing sites blocked by Netcraft usually ask for far more information than a conventional online banking phishing attack would do, capturing not just the victim's bank account details and card number, but also details about the student's university course and term time address.
Frozen phish
Despite the SLC warning of an increase in phishing attacks, it is fortunate that the fraudsters instead put an unexpected freeze on their phishing activity over the Christmas holidays. In fact, not a single student loan phishing site has been blocked by Netcraft since before Christmas day.
During 2014, Netcraft blocked more than 180 phishing URLs that impersonated the Student Loans Company or the Student Finance England service (which is run by the SLC), while SLC's fraud team took down around 150 phishing sites. Over the past three years, it claims to have prevented almost £3 million being stolen.

The calm before the storm that didn't happen: Most student loan phishing attacks occurred at the start of the academic year (September), and all of those carried out in December took place before Christmas day. Despite the second loan instalments being sent out this week, no attacks have taken place since.
New students make particularly attractive targets for fraudsters, as many will have no previous experience at managing their own finances. Research by the British Bankers' Association suggests that one in six of those aged 18 to 25 could be vulnerable to money transfer scams; a higher proportion than any other age group.
Student loans in the UK typically consist of a tuition fee loan – which can be up to £9,000 per year and is paid directly to a student's university or college – plus a maintenance loan of up to £7,751, which is paid into the student's own bank account, making the latter component an obvious target for phishing fraudsters.
Organisations concerned about email impersonation attacks can use Netcraft's Fraud Detection service, which processes DMARC (Domain-based Message Authentication, Reporting and Conformance) reports on your behalf. These reports are sent by ISPs and e-mail receivers when they see any emails which claim to be from one of your own domains. A web interface shows the status of all of your own domains, any configuration changes required, and highlights unprotected domains being used by fraudsters attacking your customers. Netcraft can also provide real time alerts of phishing sites targeting your company, and our takedown service can be used to remove phishing sites.
Continue reading...

