1. Background
I'm trying to do the box Overpass3 from tryhackme. The box need me to set up ssh port forwarding for nfs service port 2049, port mapper port 111 and another port 20048.
2. Problem
After setting up the tunnel (command follows next) for port 2049, I didn't catch any TCP traffic in wireshark when issuing the command
3. System setup
To access tryhackme box I have a openvpn running.
No other proxies are running on my system.
Result of ifconfig:
SSH config all set to default.
No firewall involved.
4. Command used
Then try to capture traffic on interface loopback in wireshark.
5. Screenshots
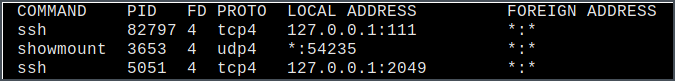
Result of sockstat -l to confirm that the specific port is being listened locally.
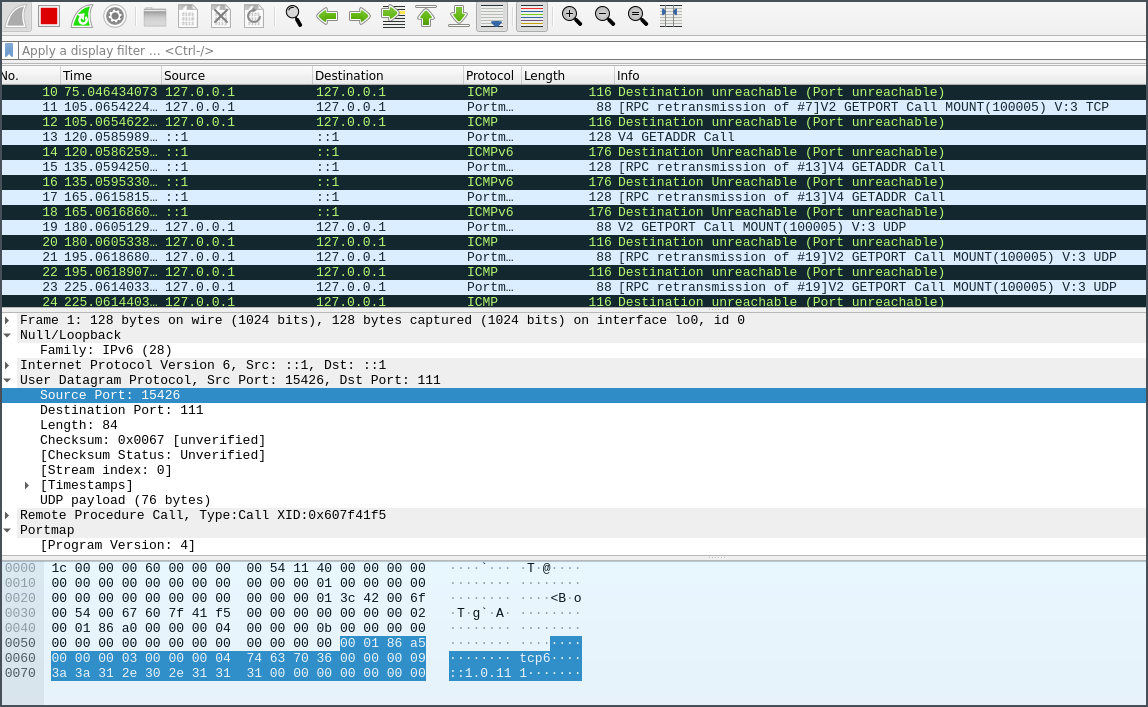
Command showmount -e localhost, only ICMP traffic is captured even the tunnel for port 2049 and 111 are both set.
6. Other test
I've try the same approach on kali linux, it's working fine. But my daily OS is freebsd, just trying to figure out what I did wrong. Need some help here.
Thanks a lot!
I'm trying to do the box Overpass3 from tryhackme. The box need me to set up ssh port forwarding for nfs service port 2049, port mapper port 111 and another port 20048.
2. Problem
After setting up the tunnel (command follows next) for port 2049, I didn't catch any TCP traffic in wireshark when issuing the command
showmount -e localhost (TCP traffic should be captured indicating that port 111 is unreachable and I should proceed settting up the next tunnel for port 111), only ICMP ones. It makes me doubt if the port forwarding is actually working. And, I've tested to set up all three tunnels, and then issue the same showmount command, still only ICMP traffic is captured in wireshark. I don't know what's going wrong here.3. System setup
To access tryhackme box I have a openvpn running.
No other proxies are running on my system.
Result of ifconfig:
Code:
em0: flags=8802<BROADCAST,SIMPLEX,MULTICAST> metric 0 mtu 1500
options=81249b<RXCSUM,TXCSUM,VLAN_MTU,VLAN_HWTAGGING,VLAN_HWCSUM,LRO,WOL_MAGIC,VLAN_HWFILTER>
ether 00:26:2d:f3:db:99
media: Ethernet autoselect
status: no carrier
nd6 options=29<PERFORMNUD,IFDISABLED,AUTO_LINKLOCAL>
lo0: flags=8049<UP,LOOPBACK,RUNNING,MULTICAST> metric 0 mtu 16384
options=680003<RXCSUM,TXCSUM,LINKSTATE,RXCSUM_IPV6,TXCSUM_IPV6>
inet6 ::1 prefixlen 128
inet6 fe80::1%lo0 prefixlen 64 scopeid 0x2
inet 127.0.0.1 netmask 0xff000000
groups: lo
nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL>
wlan0: flags=8843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST> metric 0 mtu 1500
ether 00:24:d7:60:b1:ec
inet 192.168.1.103 netmask 0xffffff00 broadcast 192.168.1.255
groups: wlan
ssid yingyuetp channel 1 (2412 MHz 11g ht/40+) bssid f4:83:cd:34:87:53
regdomain FCC country US authmode WPA2/802.11i privacy ON
deftxkey UNDEF AES-CCM 2:128-bit AES-CCM 3:128-bit txpower 30 bmiss 10
scanvalid 60 protmode CTS ampdulimit 64k ampdudensity 8
-amsdutx amsdurx shortgi -stbc -ldpc -uapsd wme roaming MANUAL
parent interface: iwn0
media: IEEE 802.11 Wireless Ethernet MCS mode 11ng
status: associated
nd6 options=29<PERFORMNUD,IFDISABLED,AUTO_LINKLOCAL>
tun0: flags=8051<UP,POINTOPOINT,RUNNING,MULTICAST> metric 0 mtu 1500
options=80000<LINKSTATE>
inet6 fe80::226:2dff:fef3:db99%tun0 prefixlen 64 scopeid 0x4
inet 10.9.166.189 --> 10.9.0.1 netmask 0xffff0000
groups: tun
nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL>
Opened by PID 84381SSH config all set to default.
No firewall involved.
4. Command used
ssh -N -L 2049:127.0.0.1:2049 -i priv_key user@box-ip sudo ssh -N -L 111:127.0.0.1:111 -i priv_key user@box-ip showmount -e localhostThen try to capture traffic on interface loopback in wireshark.
5. Screenshots
Result of sockstat -l to confirm that the specific port is being listened locally.
Command showmount -e localhost, only ICMP traffic is captured even the tunnel for port 2049 and 111 are both set.
6. Other test
I've try the same approach on kali linux, it's working fine. But my daily OS is freebsd, just trying to figure out what I did wrong. Need some help here.
Thanks a lot!

