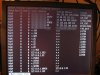
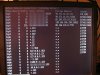
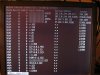
Generally, a 'netstat -an' on our old mail server displays only MY local IP address since I'm usually logged-in remotely to monitor the server. However, in recent weeks, I'm seeing several unknown IP addresses (often in PAIRS, each accessing a different local port) that all literally pop-up at the same time. Most of the time, they're on port 25 (this is a mail server, NOT a web server), but sometimes random ports. See attached screenshots (I've blurred the server's and my local IP for security).
Often, when I blackhole or tcpdrop or pfctl-badhost the last (bottom) IP, they'll all instantly disappear. But, within seconds, a completely new set of IPs pop-up at the same time. Because there're so many of them and they come-and-go so frequently, I'm not sure how to track what each IP is doing on the server?
A 'who' or 'w' indicates that I'm the only user logged-in, so I don't think they're able to log into the server. But it worries me that these IPs are SUDDENLY and constantly appearing, always changing with new ones appearing to spawn as I blackhole or dump them.
Any ideas what's going on? Does this look like a script kiddie or foreign government hackers or something like that? There's got to be a reason they keep coming back, especially as I keep trying to dump them.
Often, when I blackhole or tcpdrop or pfctl-badhost the last (bottom) IP, they'll all instantly disappear. But, within seconds, a completely new set of IPs pop-up at the same time. Because there're so many of them and they come-and-go so frequently, I'm not sure how to track what each IP is doing on the server?
A 'who' or 'w' indicates that I'm the only user logged-in, so I don't think they're able to log into the server. But it worries me that these IPs are SUDDENLY and constantly appearing, always changing with new ones appearing to spawn as I blackhole or dump them.
Any ideas what's going on? Does this look like a script kiddie or foreign government hackers or something like that? There's got to be a reason they keep coming back, especially as I keep trying to dump them.