zirias@
Developer
I'm using net/freeradius3 to provide authentication with PEAP for wifi clients. Previously, I used certificates issued by my own local CA. This worked well when installing the CA certificate on the clients (including my android phone). They were issued for the name of my local domain, let's say
Now, a persisting problem was that the older android phone of my wife would never accept the certificate. I read about the risks of using certificates issued by a public CA (which would be someone managing to get a "fake" certificate for my domain name somehow and use it to setup a fake AP stealing user credentials, well…) and decided that risk was small enough, so I now tried to use a "letsencrypt" certificate on the radiusd instead.
Unfortunately, the problem got worse: My own phone won't accept that certificate either. So far I tried a certificate issued for
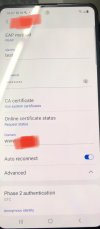
The first thing I don't understand is: how does a client know which name to expect? In the APs, you only configure the IP-Address(!) of the radius server, and give it a "radius profile name" (which I set to
home.mydomain.invalid, although the radiusd is running on a host inside that domain, e.g. auth.home.mydomain.invalid.Now, a persisting problem was that the older android phone of my wife would never accept the certificate. I read about the risks of using certificates issued by a public CA (which would be someone managing to get a "fake" certificate for my domain name somehow and use it to setup a fake AP stealing user credentials, well…) and decided that risk was small enough, so I now tried to use a "letsencrypt" certificate on the radiusd instead.
Unfortunately, the problem got worse: My own phone won't accept that certificate either. So far I tried a certificate issued for
home.mydomain.invalid as well as one issued for both auth.home.mydomain.invalid and home.mydomain.invalid.The first thing I don't understand is: how does a client know which name to expect? In the APs, you only configure the IP-Address(!) of the radius server, and give it a "radius profile name" (which I set to
home.mydomain.invalid). And then, could there be other things "wrong" with the certificate so clients trying to authenticate with PEAP would reject it?