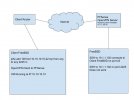
I have a FreeBSD box running a VM, the VM accepts SSH on 10.10.10.10:22.
I have the FreeBSD box setup with a VPN to an OpenVPN server, the IP address the OpenVPN server assigns on my local network is 10.1.1.102.
I can SSH to 10.1.1.102 and connect to the server.
When I add this rule to the server I expect to be able to SSH to the VM hosted on the box but feel like I'm missing something.
with the rule in place, SSH takes a while to time out and without the rule the connection is refused.
If I add this rule I get the expected result of connecting to the FreeBSD box.
I have the FreeBSD box setup with a VPN to an OpenVPN server, the IP address the OpenVPN server assigns on my local network is 10.1.1.102.
I can SSH to 10.1.1.102 and connect to the server.
When I add this rule to the server I expect to be able to SSH to the VM hosted on the box but feel like I'm missing something.
ipfw add 100 fwd 10.10.10.10,22 tcp from any to any 2225 inwith the rule in place, SSH takes a while to time out and without the rule the connection is refused.
If I add this rule I get the expected result of connecting to the FreeBSD box.
ipfw add 100 fwd 127.0.0.1,22 tcp from any to any 2226 in