Certificate Authorities are still issuing tens of thousands of certificates for domain names obviously intended for use in phishing and fraud. Fraudsters are mostly using just two CAs — Let's Encrypt and Comodo domain-validated certificates accounted for 96% of phishing sites with a valid TLS certificate found in the first quarter of 2017.
Netcraft has blocked phishing attacks on more than 47,500 sites with a valid TLS certificate between 1st January and 31st March 2017. On 19,700 of these, Netcraft blocked the whole site rather than a specific subdirectory. 61% of the sites that were entirely blocked were using certificates issued by Let's Encrypt, and 36% by Comodo.
While some CAs, browser vendors, and commentators have argued that fraud prevention is not and should not be the role of certificate authorities, the scale of foreseeable misuse that can be combated automatically warrants further consideration of this policy. Without change, issuance of certificates for sites such as login-appleid.com-direct-apple.com and dropbox.com.login.verify.danaharperandfriends.com that are obviously intended for misuse will continue unabated.
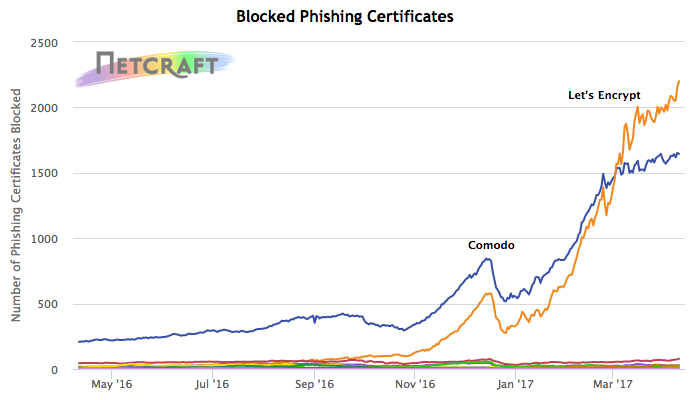
Certificates issued by publicly-trusted CAs that have been used on phishing sites. An interactive, updating version of this graph can be found on Netcraft's Phishiest Certificate Authorities page.
Mozilla Firefox's telemetry reports that approximately 55% of all page loads are over HTTPS. The movement to a secure web is crucial to defend against the risks posed by unencrypted traffic, and easy access to trusted certificates is a key factor in the recent growth. However, this easy access also offers opportunities for fraudsters to capitalise on the perception of HTTPS as trustworthy as demonstrated by the number of certificates issued for clearly deceptive domain names.
Looking at a small sample of these blocked phishing sites with valid TLS certificates that have high Deceptive Domain Scores:
Hostname Certificate Authority Target Deceptive Domain Score
login-appleid.com-direct-apple.com Let's Encrypt Apple
9.25
payepal.com-signin-country-localed.access-logons.com Let's Encrypt PayPal
9.13
www.ll-airbnb.com Symantec Airbnb
8.99
chaseonline.chase.com.bajpayee.com Comodo Chase
10.00
payqal.limited GoDaddy PayPal
9.13
lost-apple.ru GlobalSign Apple
9.30
servicesonline-americanexpress.com Let's Encrypt American Express
7.99
dropbox.com.login.verify.danaharperandfriends.com Comodo Dropbox
9.70
update.wellsfargo.com.casaecologica.cl Let's Encrypt Wells Fargo
10.00
bankofamerica.com.online.do.dbraunss.org Comodo Bank of America
9.40
labanque-postalegroupe.com Let's Encrypt La Banque Postale
7.10
usaa.com.983746.imexcomed.com.bo Let's Encrypt USAA
10.00
In each of these examples above — and in the other statistics referenced above — the certificate authority had sight of the whole hostname that was blocked. These examples did not rely on wildcard certificates to carry out their deception. In particular, some of these examples (such as update.wellsfargo.com.casaecologica.cl) demonstrate that the certificate authority was better placed to prevent misuse than the domain registrar (who would have seen casaecologica.cl upon registration).
Let's Encrypt and Comodo are attractive to fraudsters as both offer automated, domain-validated certificates at no cost to end users. Let's Encrypt's ACME protocol allows for free automated issuance, while Comodo offers no-cost certificates via its trial certificates, cPanel AutoSSL, and its Cloudflare partnership.
While Let's Encrypt's policy on phishing and malware is to check the Safe Browsing API, this does not provide effective pre-issuance blocking. It does not match the reality of automated certificate deployment, where the certificate is likely to be issued and installed before the phishing content has been uploaded, detected, and blocked. Let's Encrypt also has a limited list of domain names for which they block issuance which has triggered forum posts by users unable to obtain a certificate for the blocked name. All of the Let's Encrypt certificates that Netcraft found on phishing sites were issued despite the Safe Browsing check and the additional name-based blocking.
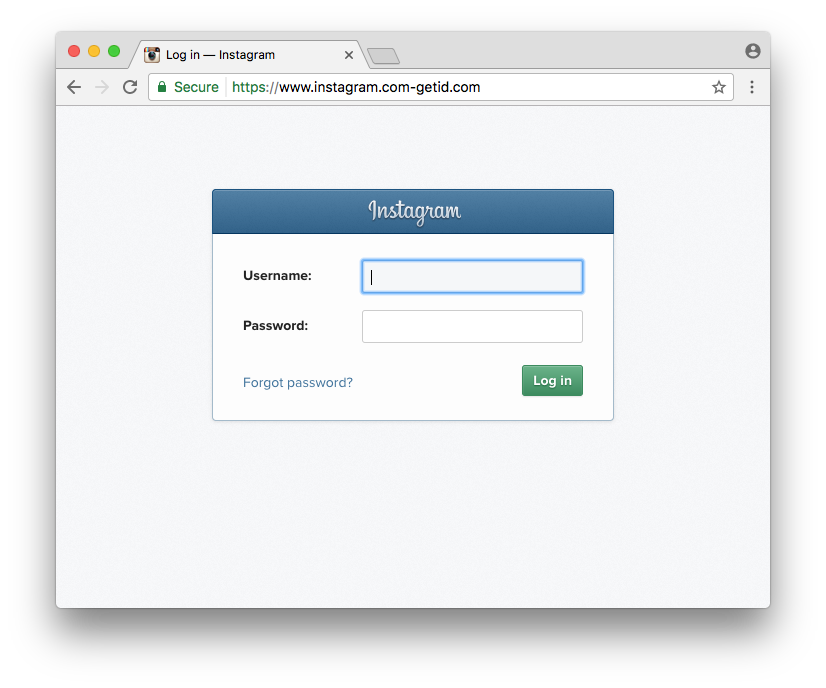
Phishing site on https://www.instagram.com-getid.com (Deceptive Domain Score is 9.46).
The use of TLS by these phishing sites is particularly dangerous, as websites that use TLS are marketed as being trustworthy and operated by legitimate organisations. Consumers have been trained to look for padlocks, security indicators, and https:// in the address bar in their browser before submitting sensitive information, such as passwords and credit card numbers, to websites.
However, a displayed padlock or "Secure" indicator alone does not imply that a site using TLS can be trusted, or is operated by a legitimate organisation. The distinction between the connection being "Secure" and the safety of providing sensitive information to the HTTPS site may be challenging to interpret for those unfamiliar with the technical underpinnings of TLS.
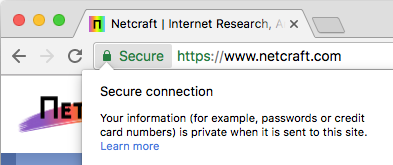
"Secure" vs. "Private" in Google Chrome.
Demonstrating the difficulty of explaining this technical distinction, Google Chrome indicates that an HTTPS connection is using a valid TLS certificate by displaying the word "Secure" in the address bar. While the word "secure" refers to the encrypted connection's protection against eavesdroppers, this is explained in the drop-down with the word "private". The distinction between these two words is subtle, yet potentially significant for user understanding. However, it is important to note that Google has been at the forefront of research into how security indicators are perceived by internet users at large.
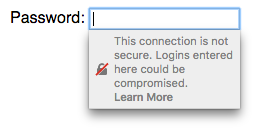
Mozilla Firefox's warning when selecting a password form field on a non-secure HTTP site.
Both Google Chrome and Mozilla Firefox have made recent changes to the display of password input forms on non-TLS sites — non-secure forms now trigger in-context warnings. These warnings are likely to increase the prevalence of TLS on phishing sites, with fraudsters deploying TLS to both gain the positive "Secure" indicator, and now to avoid negative indicators when collecting passwords.
Deceptive Domain Score service
Netcraft's Deceptive Domain Score service provides an automated mechanism for evaluating whether a given hostname or domain name is likely to be used to fraudulently impersonate an organisation. Crucially, this can be evaluated before issuing a certificate. Of these 19,700 hostnames with valid TLS certificates where Netcraft blocked the entire site, 72.5% scored more than 5.0 and 49% more than 7.0 (on a scale from 0.0 to 10.0).
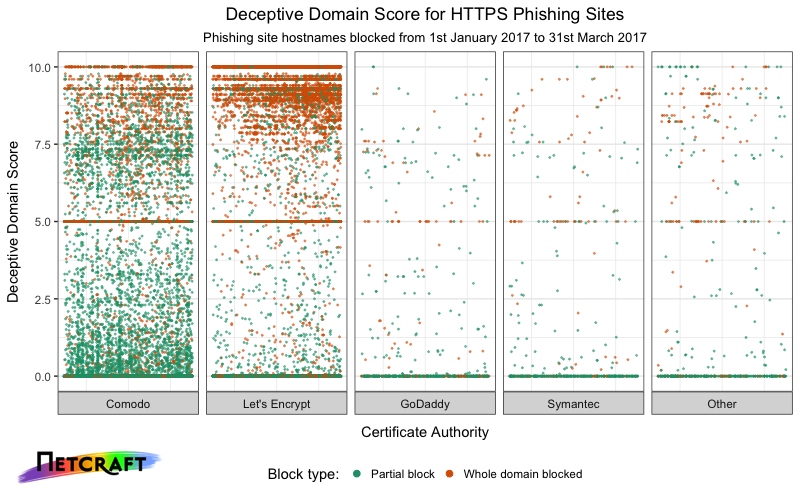
Distribution of Deceptive Domain Score across blocked phishing sites with valid TLS certificates.
For comparison, a random sample of 10,000 hostnames taken from domain-validated certificates issued in February 2017 as found in Netcraft's April 2017 SSL survey, had an average score of 0.72, with 7% having a score over 5.0, and 4.4% a score over 7.0.
More information on Netcraft's Deceptive Domain Score service can be found on Netcraft's website.
Continue reading...
Netcraft has blocked phishing attacks on more than 47,500 sites with a valid TLS certificate between 1st January and 31st March 2017. On 19,700 of these, Netcraft blocked the whole site rather than a specific subdirectory. 61% of the sites that were entirely blocked were using certificates issued by Let's Encrypt, and 36% by Comodo.
While some CAs, browser vendors, and commentators have argued that fraud prevention is not and should not be the role of certificate authorities, the scale of foreseeable misuse that can be combated automatically warrants further consideration of this policy. Without change, issuance of certificates for sites such as login-appleid.com-direct-apple.com and dropbox.com.login.verify.danaharperandfriends.com that are obviously intended for misuse will continue unabated.

Certificates issued by publicly-trusted CAs that have been used on phishing sites. An interactive, updating version of this graph can be found on Netcraft's Phishiest Certificate Authorities page.
Mozilla Firefox's telemetry reports that approximately 55% of all page loads are over HTTPS. The movement to a secure web is crucial to defend against the risks posed by unencrypted traffic, and easy access to trusted certificates is a key factor in the recent growth. However, this easy access also offers opportunities for fraudsters to capitalise on the perception of HTTPS as trustworthy as demonstrated by the number of certificates issued for clearly deceptive domain names.
Looking at a small sample of these blocked phishing sites with valid TLS certificates that have high Deceptive Domain Scores:
Hostname Certificate Authority Target Deceptive Domain Score
login-appleid.com-direct-apple.com Let's Encrypt Apple
9.25
payepal.com-signin-country-localed.access-logons.com Let's Encrypt PayPal
9.13
www.ll-airbnb.com Symantec Airbnb
8.99
chaseonline.chase.com.bajpayee.com Comodo Chase
10.00
payqal.limited GoDaddy PayPal
9.13
lost-apple.ru GlobalSign Apple
9.30
servicesonline-americanexpress.com Let's Encrypt American Express
7.99
dropbox.com.login.verify.danaharperandfriends.com Comodo Dropbox
9.70
update.wellsfargo.com.casaecologica.cl Let's Encrypt Wells Fargo
10.00
bankofamerica.com.online.do.dbraunss.org Comodo Bank of America
9.40
labanque-postalegroupe.com Let's Encrypt La Banque Postale
7.10
usaa.com.983746.imexcomed.com.bo Let's Encrypt USAA
10.00
In each of these examples above — and in the other statistics referenced above — the certificate authority had sight of the whole hostname that was blocked. These examples did not rely on wildcard certificates to carry out their deception. In particular, some of these examples (such as update.wellsfargo.com.casaecologica.cl) demonstrate that the certificate authority was better placed to prevent misuse than the domain registrar (who would have seen casaecologica.cl upon registration).
Let's Encrypt and Comodo are attractive to fraudsters as both offer automated, domain-validated certificates at no cost to end users. Let's Encrypt's ACME protocol allows for free automated issuance, while Comodo offers no-cost certificates via its trial certificates, cPanel AutoSSL, and its Cloudflare partnership.
While Let's Encrypt's policy on phishing and malware is to check the Safe Browsing API, this does not provide effective pre-issuance blocking. It does not match the reality of automated certificate deployment, where the certificate is likely to be issued and installed before the phishing content has been uploaded, detected, and blocked. Let's Encrypt also has a limited list of domain names for which they block issuance which has triggered forum posts by users unable to obtain a certificate for the blocked name. All of the Let's Encrypt certificates that Netcraft found on phishing sites were issued despite the Safe Browsing check and the additional name-based blocking.

Phishing site on https://www.instagram.com-getid.com (Deceptive Domain Score is 9.46).
The use of TLS by these phishing sites is particularly dangerous, as websites that use TLS are marketed as being trustworthy and operated by legitimate organisations. Consumers have been trained to look for padlocks, security indicators, and https:// in the address bar in their browser before submitting sensitive information, such as passwords and credit card numbers, to websites.
However, a displayed padlock or "Secure" indicator alone does not imply that a site using TLS can be trusted, or is operated by a legitimate organisation. The distinction between the connection being "Secure" and the safety of providing sensitive information to the HTTPS site may be challenging to interpret for those unfamiliar with the technical underpinnings of TLS.

"Secure" vs. "Private" in Google Chrome.
Demonstrating the difficulty of explaining this technical distinction, Google Chrome indicates that an HTTPS connection is using a valid TLS certificate by displaying the word "Secure" in the address bar. While the word "secure" refers to the encrypted connection's protection against eavesdroppers, this is explained in the drop-down with the word "private". The distinction between these two words is subtle, yet potentially significant for user understanding. However, it is important to note that Google has been at the forefront of research into how security indicators are perceived by internet users at large.

Mozilla Firefox's warning when selecting a password form field on a non-secure HTTP site.
Both Google Chrome and Mozilla Firefox have made recent changes to the display of password input forms on non-TLS sites — non-secure forms now trigger in-context warnings. These warnings are likely to increase the prevalence of TLS on phishing sites, with fraudsters deploying TLS to both gain the positive "Secure" indicator, and now to avoid negative indicators when collecting passwords.
Deceptive Domain Score service
Netcraft's Deceptive Domain Score service provides an automated mechanism for evaluating whether a given hostname or domain name is likely to be used to fraudulently impersonate an organisation. Crucially, this can be evaluated before issuing a certificate. Of these 19,700 hostnames with valid TLS certificates where Netcraft blocked the entire site, 72.5% scored more than 5.0 and 49% more than 7.0 (on a scale from 0.0 to 10.0).

Distribution of Deceptive Domain Score across blocked phishing sites with valid TLS certificates.
For comparison, a random sample of 10,000 hostnames taken from domain-validated certificates issued in February 2017 as found in Netcraft's April 2017 SSL survey, had an average score of 0.72, with 7% having a score over 5.0, and 4.4% a score over 7.0.
More information on Netcraft's Deceptive Domain Score service can be found on Netcraft's website.
Continue reading...

