Hi all.
In hetzner they say I should allow the follow rule in their firewall.
But when I activated the FreeBSD 12 has no internet access.
All other os like CentOS, windows works okey the problem is only with FreeBSD.
In my system I don't run ipfw and I don't understand why the problem exists.
If I deactivate Hetzner firewall everything looks okey.
With firewall enabled I can not even ping 8.8.8.8.
I understand must be something with kernel port range but I don't know where to configure it.
Also it is strange that even Midnight Commander doesn't start like he is trying to get a webpage or communicate with a port to outside.
Thank You.
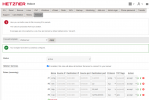
In hetzner they say I should allow the follow rule in their firewall.
- Name: TCP_Out
- Source IP: 0.0.0.0/0
- Destination IP: 0.0.0.0/0
- Destination port: 32768-65535
- Protocol: tcp
- TCP flags: ack
- Action: accept
But when I activated the FreeBSD 12 has no internet access.
All other os like CentOS, windows works okey the problem is only with FreeBSD.
In my system I don't run ipfw and I don't understand why the problem exists.
If I deactivate Hetzner firewall everything looks okey.
With firewall enabled I can not even ping 8.8.8.8.
I understand must be something with kernel port range but I don't know where to configure it.
Also it is strange that even Midnight Commander doesn't start like he is trying to get a webpage or communicate with a port to outside.
Thank You.