Hi, i have trouble with Ipsec & pf enc0 nat problem . I show you my problematic scenerio below any help would be appreciated at this point
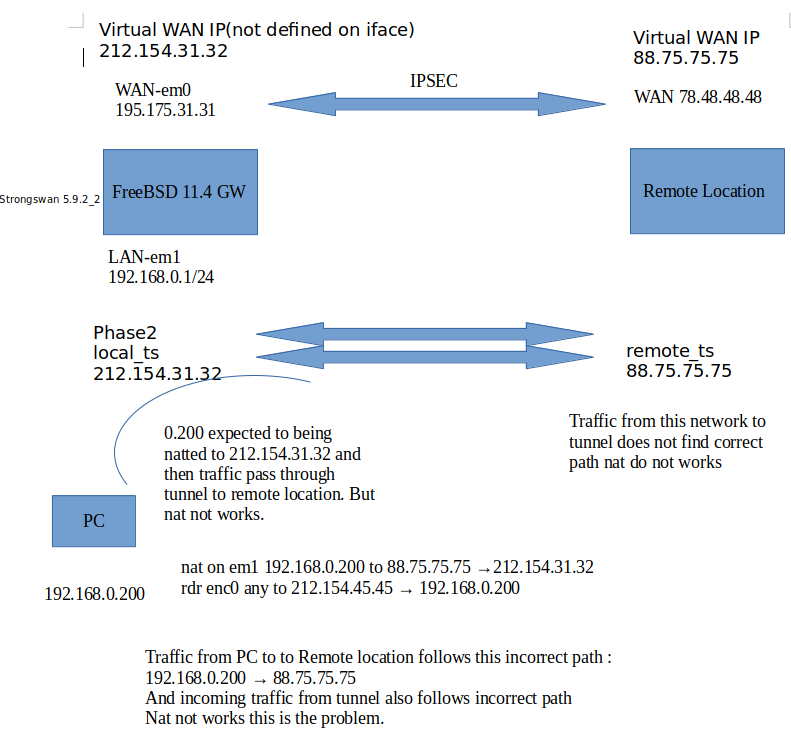
STRONGSWAN CONFIGURATION
STRONGSWAN CONFIGURATION
Code:
alfa7000 {
fragmentation = yes
unique = replace
version = 1
aggressive = no
proposals = 3des-sha1-modp1024
dpd_delay = 10s
dpd_timeout = 60s
reauth_time = 3240s
over_time = 360s
rand_time = 360s
encap = no
mobike = no
remote_addrs = 78.48.48.48
local {
id =
auth = psk
}
remote {
id = 78.48.48.48
auth = psk
}
children {
alfa7001 {
dpd_action = trap
mode = tunnel
policies = yes
life_time = 3600s
rekey_time = 3240s
rand_time = 360s
start_action = trap
local_ts = 212.154.31.32/32
remote_ts = 88.75.75.75/32
esp_proposals = 3des-sha1-modp1024
}
}
}
}
secrets {
ike-0 {
secret = 0sMTIzNDU2WHg=
id-0 = %any
id-1 = 78.48.48.48
}
}

