How to determine if CPU of a host is capable for SSE,SSE2,SSSE3,SSE4.1 and SSE4.2 ?
In
I did find
while browsing FreeBSD's source but nothing readily accessible besides that.
I also came up with the idea of parsing the
Ideas?
Why I need it? Perhaps image would explain better.
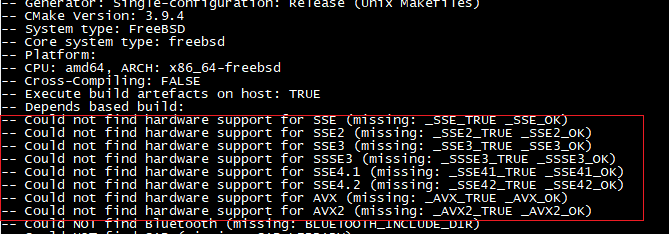
In
cmake. So it should be accessible through shell.I did find
Code:
hw.instruction_sseI also came up with the idea of parsing the
dmesg | grep Features2 but it may not be available with plain user privileges.Ideas?
Why I need it? Perhaps image would explain better.