Security holes in Brazilian government websites are still rife, with no fewer than eight different gov.br sites being compromised within the past week to host phishing attacks and hacking scripts. The situation does not seem to have improved much since two years ago, when we noticed a similar spate of phishing sites and malware hosted on gov.br domains, with evidence of some sites suffering repeated security compromises.
In one of this week's attacks, a gov.br domain was compromised to such an extent that the fraudsters were able to set up their own custom hostname, which was also configured to use HTTPS. The website, at account-verification-redirect-center.[redacted].gov.br, was then used to host a PayPal phishing site, which is still present at the time of writing.
Despite its rather dubious hostname, Let's Encrypt automatically issued an SSL certificate to account-verification-redirect-center.[redacted].gov.br earlier this week. Such foreseeable misuse evidently still does not prevent certificates being issued to phishing sites; but worse still, the fraudulent certificate has not yet been revoked.
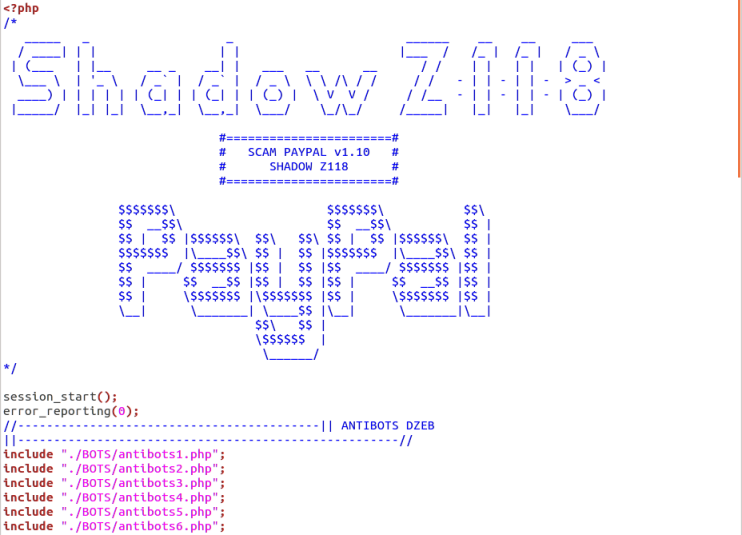
The PayPal phishing site makes use of a ready-made phishing kit provided by SHADOW Z118. It includes several comprehensive "antibots" PHP scripts to avoid detection by search engines and enforcement agencies.
To make matters worse, Netcraft found PHP shells on a few of the recently compromised gov.br sites. These backdoors provide fraudsters with almost complete access to the compromised web servers and make it easy for malware and phishing content to be uploaded at any time.
If the PHP shells are not removed, additional phishing sites are likely to appear on the affected sites, or they could even become infested with other PHP shells that will make the clean-up job much harder: If just one shell is overlooked, it can be used to replace all phishing content, malware and backdoors that the web server administrators had already deleted.
PayPal is still the most commonly targeted organisation in the latest attacks hosted by the Brazilian government, but other targets include Microsoft, Naver, Dropbox and the online dating site Match.com.
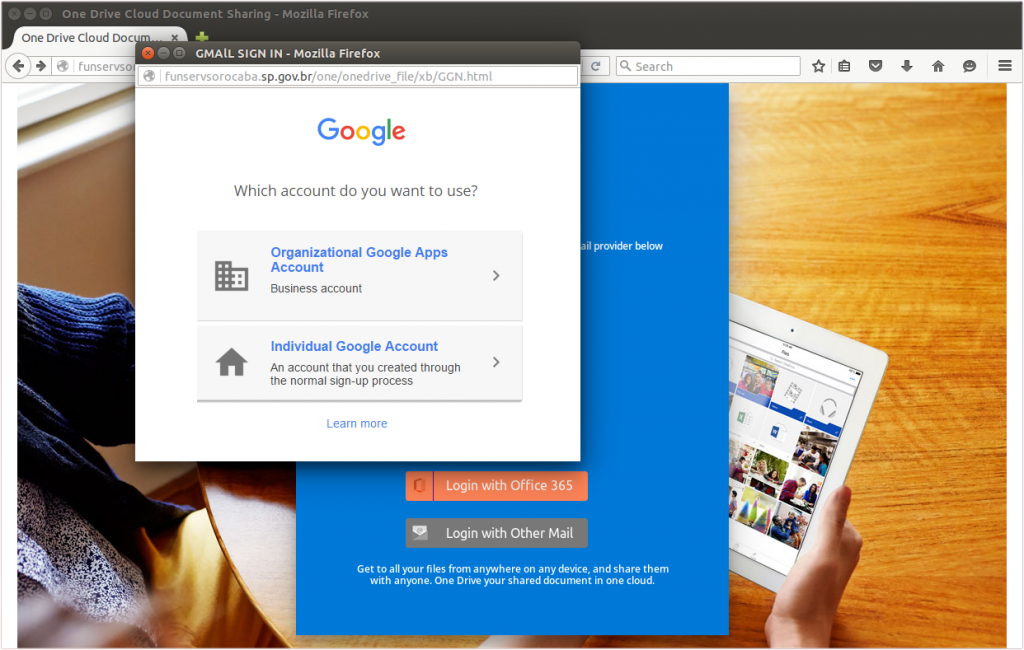
This OneDrive phishing site can steal Google, Outlook, AOL, Yahoo, Office 365, and other email credentials. A second form steals the victim's phone number and backup email address.
Some of the phishing sites impersonate Microsoft's OneDrive service, using it as a convenient excuse to target Google, Outlook, AOL, Yahoo and other types of accounts from just a single attack. This particular attack could be rather harmful to businesses, as it gives victims the opportunity to log in with an Organizational Google Apps Account, which could result in the fraudster gaining access to sensitive company secrets.
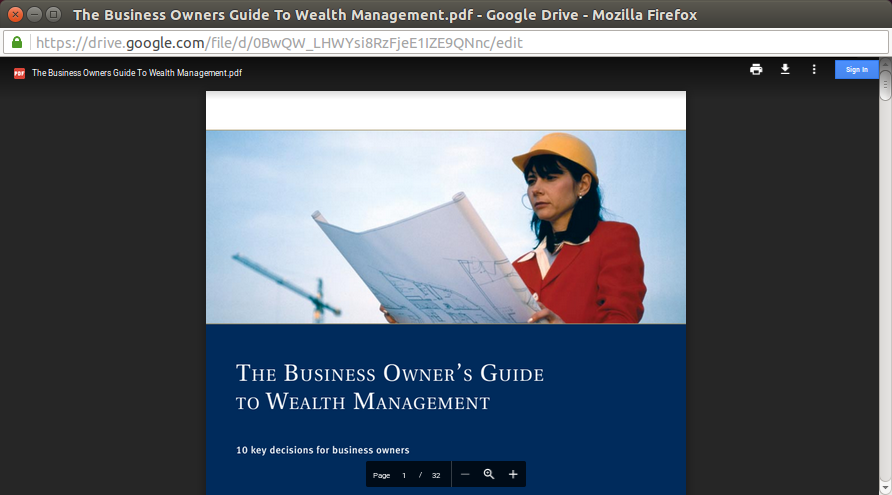
Ironically, after the victim has been phished, he will be redirected to a PDF file on Google Drive entitled "The Business Owner's Guide to Wealth Management".
All of the aforementioned phishing attacks were added to Netcraft's Phishing Site Feed, which is used by major web browsers and many leading anti-virus, content-filtering and web hosting companies.
Continue reading...
In one of this week's attacks, a gov.br domain was compromised to such an extent that the fraudsters were able to set up their own custom hostname, which was also configured to use HTTPS. The website, at account-verification-redirect-center.[redacted].gov.br, was then used to host a PayPal phishing site, which is still present at the time of writing.
Despite its rather dubious hostname, Let's Encrypt automatically issued an SSL certificate to account-verification-redirect-center.[redacted].gov.br earlier this week. Such foreseeable misuse evidently still does not prevent certificates being issued to phishing sites; but worse still, the fraudulent certificate has not yet been revoked.

The PayPal phishing site makes use of a ready-made phishing kit provided by SHADOW Z118. It includes several comprehensive "antibots" PHP scripts to avoid detection by search engines and enforcement agencies.
To make matters worse, Netcraft found PHP shells on a few of the recently compromised gov.br sites. These backdoors provide fraudsters with almost complete access to the compromised web servers and make it easy for malware and phishing content to be uploaded at any time.
If the PHP shells are not removed, additional phishing sites are likely to appear on the affected sites, or they could even become infested with other PHP shells that will make the clean-up job much harder: If just one shell is overlooked, it can be used to replace all phishing content, malware and backdoors that the web server administrators had already deleted.
PayPal is still the most commonly targeted organisation in the latest attacks hosted by the Brazilian government, but other targets include Microsoft, Naver, Dropbox and the online dating site Match.com.

This OneDrive phishing site can steal Google, Outlook, AOL, Yahoo, Office 365, and other email credentials. A second form steals the victim's phone number and backup email address.
Some of the phishing sites impersonate Microsoft's OneDrive service, using it as a convenient excuse to target Google, Outlook, AOL, Yahoo and other types of accounts from just a single attack. This particular attack could be rather harmful to businesses, as it gives victims the opportunity to log in with an Organizational Google Apps Account, which could result in the fraudster gaining access to sensitive company secrets.

Ironically, after the victim has been phished, he will be redirected to a PDF file on Google Drive entitled "The Business Owner's Guide to Wealth Management".
All of the aforementioned phishing attacks were added to Netcraft's Phishing Site Feed, which is used by major web browsers and many leading anti-virus, content-filtering and web hosting companies.
Continue reading...
