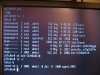
My apologies in advance if some of these questions seem obvious, but I've been out of the BSD loop for many years and have been tasked with dealing with two old FreeBSD servers. Yes, I'm aware they're quite out-of-date, but they've been running without issue for many years (if it ain't broke...) and I don't have the time, knowledge or testicular fortitude to muck with proper upgrades considering the likelihood that I'd be causing problems where none currently exist simply to implement "best practices". That said...attached are screenshots of the /tmp contents of our email (pitcher) and web server (huntington), running BSD 4.11 and 6.3, respectively. In that context, I have a few questions:
1) Can someone point me to a man page or FAQ or describe what the various directories and files are in these /tmp directories; and, more importantly, whether they're innocuous, evidence of security issues and/or if they can be deleted without affecting anything? That is, unless needed for operation, I'd like to know which may be safely deleted.
2) What are the agent.xxx files in the ssh-* directories in /tmp, and can I delete them?
3) Both servers' /tmp directories contain the same four .*-unix directories, which appear to be empty. One of which, .X11-unix, appears to reference X Windows, which is NOT installed on either server. Are these referencing something other than X Windows?
4) Who is user "1004", or how do I find out?
1) Can someone point me to a man page or FAQ or describe what the various directories and files are in these /tmp directories; and, more importantly, whether they're innocuous, evidence of security issues and/or if they can be deleted without affecting anything? That is, unless needed for operation, I'd like to know which may be safely deleted.
2) What are the agent.xxx files in the ssh-* directories in /tmp, and can I delete them?
3) Both servers' /tmp directories contain the same four .*-unix directories, which appear to be empty. One of which, .X11-unix, appears to reference X Windows, which is NOT installed on either server. Are these referencing something other than X Windows?
4) Who is user "1004", or how do I find out?