This topic provides a solution on how to make own Proxy serwer, on a FreeBSD operating system, using Stunnel validated with public-key cryptography between Stunnel server and Stunnel client, for use by a web browser. The primary benefit is that, unlike other VPN, the client does not require administrator privileges for working. This type of network can be with entry, for example, at airports or in an Internet cafe, or anywhere where firewalls and security policies filter traffic. The service used to create the SOCKS5 proxy is net/3proxy, also known as threeproxy. The program used to tunnel the traffic is security/stunnel. security/OpenSSL was used to generate the keys. The principle of operation is based on encrypting the traffic between the client and the stunnel server, then the decrypted traffic locally on the FreeBSD server "falls" into the 3proxy and flies further into the world. SSL encryption (especially on port 443) prevents automatic firewall traffic blocking.
1. Installs needed packages from ports.
2. After installing the packages, go to their configuration.
The stunnel configuration file is located in:
Whereas 3proxy is located in:
3. Let's start with Stunnel Server.
The configuration of this program should include:
4. Generating self-signed certificates using OpenSSL.
Navigating to /usr/local/etc/stunnel/ folder.
Once there, should to start generating certificates. To do this, first generate a private key with name privatekey.pem.
Generating a certificate based on a private key. Fields for entering information such as country code, city, company, etc. will be displayed. For home/private use, is possible to leave the default by clicking enter:
Self-signed certificate (creating a server-signed certificate):
ls -l shows several files. It's not hard to see that the privatekey.pem and publickey.pem files are used by the stunnel server config file and the path to them was given earlier.
5. Setting 3proxy to work with password authorization. This password will then be necessary for operation. Will be needed to enter it into web browser. The password is set because the stunnel server listens globally and there would be the possibility of unauthorized common proxy access.
6. Starting services.
Enable stunnel and 3proxy with commands:
It should run without errors. Can also add entries to /etc/rc.conf here using
The operation of the services can be checked with stem commands.
Or using the sockstat command as shown in the example:
Since when enabled, stunnel works but becomes unresponsive to system commands, so to change the settings, first disable stunnel with
7. Client configuration, in the Windows example.
First, download it from somewhere, e.g. from the official stunnel website for the operating system you are using. Installing stunnel from an .exe file to some folder, or installing stunnel at home and transferring it to target computer usfing flash drive or network drive/CD-ROM etc. During the installation, the program will open a cmd console to generate keys using OpenSSL, which will not be used anyway, so we use the default settings by clicking enter.
In the folder C:\Users\yourusername\Desktop\stunnel\config there is a configuration file called stunnel.conf. Delete it or rename it to, for example, stunnel.conf.bac
Create a new configuration file called stunnel.conf About the content:
Static can be obtained from ISP (Internet Software Proider).
Run the program using tstunnel.exe C:\Users\yourusername\Desktop\stunnel\bin\tstunnel.exe. The connection between the tunnels has been established on port 443 and encrypted.
7. Configure FireFox using a browser add-on called FoxyProxy because FoxyProxy allows to enter the proxy server password that was defined at the beginning.
Install FoxyProxy standard from the FireFox store.

 addons.mozilla.org
addons.mozilla.org
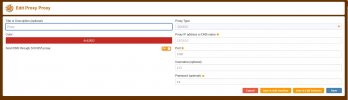
Then in the FoxyProxy menu, is nessesery to press Add button and Add proxy:
And press Save. Just like in the picture.
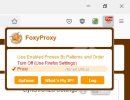
8. In the add-on options in the new tab, is needed to enable the previously defined proxy for all addresses.
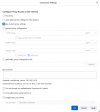
9. In the connection option in FireFox main settings, it should be set to "Use system proxy settings" As can be seen, the network connection settings inside FireFox do not give the option to enter a password.
10. At this point Tunnel SSL is properly configured and working.
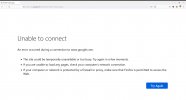
11. However, if an incorrect login or password is entered in FoxyProxy, will get a message behind "Unable to connect".
1. Installs needed packages from ports.
Code:
root@router:~ # pkg install openssl
root@router:~ # pkg install 3proxy
root@router:~ # pkg install stunnel2. After installing the packages, go to their configuration.
The stunnel configuration file is located in:
Code:
/usr/local/etc/stunnel/stunnel.confWhereas 3proxy is located in:
Code:
/usr/local/etc/3proxy.cfg3. Let's start with Stunnel Server.
The configuration of this program should include:
ee /usr/local/etc/stunnel/stunnel.conf
Code:
# Global options
# debug = 7
# output = /var/log/stunnel.log
# Service options
[Server]
accept = 443
connect = 127.0.0.1:8282
cert = /usr/local/etc/stunnel/publickey.pem
key = /usr/local/etc/stunnel/privatekey.pem debug = 7 - It accepts arguments from 0 to 7, where 7 is the highest level of log detail. output = /var/log/stunnel.log - Log file. Logs are no longer needed so they are bound. accept = 443 - Listening for incoming connections from outside on port 443. connect = 127.0.0.1:8282 - Connecting via localhost to the 3proxy server, on port 8282 where the proxy server will be listening. cert = /usr/local/etc/stunnel/publickey.pem - Location of the public key. key = /usr/local/etc/stunnel/privatekey.pem - Location of the private key.4. Generating self-signed certificates using OpenSSL.
Navigating to /usr/local/etc/stunnel/ folder.
Code:
cd /usr/local/etc/stunnel/Once there, should to start generating certificates. To do this, first generate a private key with name privatekey.pem.
Code:
root@router:/usr/local/etc/stunnel # openssl genpkey -algorithm RSA -out privatekey.pemGenerating a certificate based on a private key. Fields for entering information such as country code, city, company, etc. will be displayed. For home/private use, is possible to leave the default by clicking enter:
Code:
root@router:/usr/local/etc/stunnel # openssl req -new -key privatekey.pem -out certificate.pemSelf-signed certificate (creating a server-signed certificate):
Code:
root@router:/usr/local/etc/stunnel # openssl x509 -req -in certificate.pem -signkey privatekey.pem -out publickey.pemls -l shows several files. It's not hard to see that the privatekey.pem and publickey.pem files are used by the stunnel server config file and the path to them was given earlier.
Code:
root@router:/usr/local/etc/stunnel # ls -l
-rw-r--r-- 1 root wheel 956 Jun 22 08:28 certificate.pem
drwxrwxrwx 2 root wheel 512 Jun 19 15:06 conf.d
-rw------- 1 root wheel 1704 Jun 22 08:24 privatekey.pem
-rw-r--r-- 1 root wheel 1123 Jun 22 08:32 publickey.pem
-rwxrwxrwx 1 root wheel 224 Jun 22 07:10 stunnel.conf
-rwxrwxrwx 1 root wheel 4633 Mar 7 10:10 stunnel.conf-sample5. Setting 3proxy to work with password authorization. This password will then be necessary for operation. Will be needed to enter it into web browser. The password is set because the stunnel server listens globally and there would be the possibility of unauthorized common proxy access.
ee /usr/local/etc/3proxy.cfg
Code:
daemon
nserver 208.67.222.222
auth strong
users 123:CL:45
socks -i127.0.0.1 -p8282 daemon - This line enables the daemon mode for 3proxy. Run it as a background service. nserver 208.67.222.222 - Defines the DNS server address that will be used by 3proxy to resolve domain names. auth strong - Strong authentication for users. Means that 3proxy will require users to authenticate themselves before granting access to the proxy service. users 123:CL:45 - defines users and their authentication credentials. In this case, a user named "123" with a password of "45" is defined. socks -i127.0.0.1 -p8282 - This line defines the SOCKS service on port 8282 listening locally.6. Starting services.
Enable stunnel and 3proxy with commands:
Code:
root@router:/usr/local/etc/stunnel # service stunnel onestart
root@router:/usr/local/etc/stunnel # service 3proxy onestartIt should run without errors. Can also add entries to /etc/rc.conf here using
sysrc stunnel_enable="YES" and sysrc threeproxy_enable="YES" , which causes the services to start when the system boot.The operation of the services can be checked with stem commands.
Code:
root@router:/usr/local/etc/stunnel # service 3proxy status
Code:
root@router:/usr/local/etc/stunnel # sockstat -l -4 | grep 8282
root 3proxy 52745 4 tcp4 127.0.0.1:8282 *:*
root@router:/usr/local/etc/stunnel # sockstat -l -4 | grep 443
root stunnel 1468 10 tcp4 *:443 *:*Since when enabled, stunnel works but becomes unresponsive to system commands, so to change the settings, first disable stunnel with
pkill stunnel (So that there is nothing in the sockstat command on port 443) And then enable it with #service stunnel start.7. Client configuration, in the Windows example.
First, download it from somewhere, e.g. from the official stunnel website for the operating system you are using. Installing stunnel from an .exe file to some folder, or installing stunnel at home and transferring it to target computer usfing flash drive or network drive/CD-ROM etc. During the installation, the program will open a cmd console to generate keys using OpenSSL, which will not be used anyway, so we use the default settings by clicking enter.
In the folder C:\Users\yourusername\Desktop\stunnel\config there is a configuration file called stunnel.conf. Delete it or rename it to, for example, stunnel.conf.bac
Create a new configuration file called stunnel.conf About the content:
Code:
client = yes
[client]
accept = 127.0.0.1:1080
connect = IPofSERVERPROXY:443 client = yes - Set to run as a client accept = 127.0.0.1:1080 - Stunnel address and port. The port to which traffic from FireFox will be redirected. connect = IPofSERVERPROXY:443 - The external IP address of the stunnel server. It can be checked in the command line by:
Code:
root@router:/usr/local/etc/stunnel # wget -qO - ifconfig.me ; echo
XXX.XXX.XXX.XXX
root@router:/usr/local/etc/stunnel # curl -s ifconfig.me ; echo
XXX.XXX.XXX.XXXRun the program using tstunnel.exe C:\Users\yourusername\Desktop\stunnel\bin\tstunnel.exe. The connection between the tunnels has been established on port 443 and encrypted.
7. Configure FireFox using a browser add-on called FoxyProxy because FoxyProxy allows to enter the proxy server password that was defined at the beginning.
Install FoxyProxy standard from the FireFox store.

FoxyProxy Standard – Get this Extension for 🦊 Firefox (en-US)
Download FoxyProxy Standard for Firefox. FoxyProxy is an open-source, advanced proxy management tool that completely replaces Firefox's limited proxying capabilities. No paid accounts are necessary; bring your own proxies or buy from any vendor. The original proxy tool, since 2006.
Then in the FoxyProxy menu, is nessesery to press Add button and Add proxy:
Proxy Type - SOCKS5 Proxy IP address or DNS name - 127.0.0.1 Port - 1080 Username - 123 Password - 45 Send DNS through SOCKS5 proxy - OnAnd press Save. Just like in the picture.

8. In the add-on options in the new tab, is needed to enable the previously defined proxy for all addresses.

9. In the connection option in FireFox main settings, it should be set to "Use system proxy settings" As can be seen, the network connection settings inside FireFox do not give the option to enter a password.

10. At this point Tunnel SSL is properly configured and working.
11. However, if an incorrect login or password is entered in FoxyProxy, will get a message behind "Unable to connect".


