Web shells are an overlooked aspect of cyber crime and do not attract the level of attention of either phishing or malware. Nevertheless, Netcraft found more than 6,000 web shells during April 2017, which works out at around 1 new shell installation every 5 minutes. When web shells first appeared, the limit of their functionality was to transfer files and execute arbitrary shell commands. However, the best engineered web shells now provide well presented, sophisticated toolkits for diverse crimes, with facilities for password cracking, privilege elevation, network reconnaissance, phishing, spamming and DDoS, not solely available through a web based user interface but also accepting commands as part of a botnet.
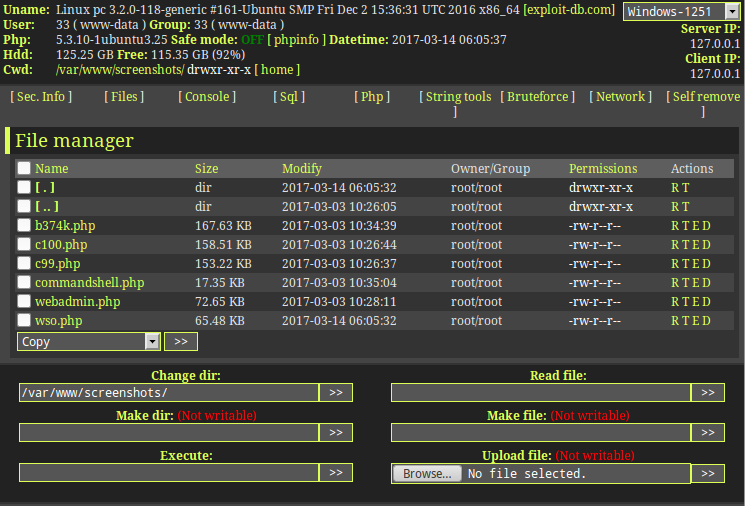
An example of the hugely popular and feature-rich WSO (Web Shell by Orb) shell.
A number of shells offer the creation of a botnet in as little as a click, launching standalone processes that either connect to a command and control server or listen for commands over an insecure TCP connection. Some allow performing port scans to find potentially exploitable services. Others enable fraudsters to schedule denial of service attacks. There are shells dedicated to sending bulk spam emails, testing stolen credentials against popular websites (such as PayPal or Amazon), cracking passwords, and automatically defacing websites. With such a wide array of powerful features, it is unsurprising how popular web shells are with cyber criminals.
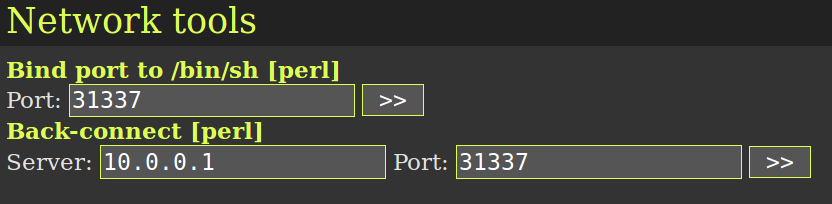
WSO offers both bind shell and back connect options. Selecting one of these options will launch a standalone process that will connect to or listen for a connection from a remote command and control server - an easy method for the creation of a botnet.
The prevalence of these backdoors allows easy—and potentially persistent—access to thousands of compromised machines. If the web shell is missed during the webmaster's cleanup after an attack, removing the original phishing or malware content will be in vain, as the fraudster can use the web shell to upload new malicious material, or re-purpose the machine as an accessory to alternative forms of cyber crime.
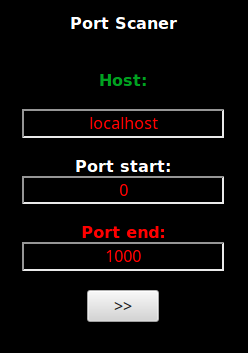
This shell allows a fraudster to port scan arbitrary hosts anonymously.
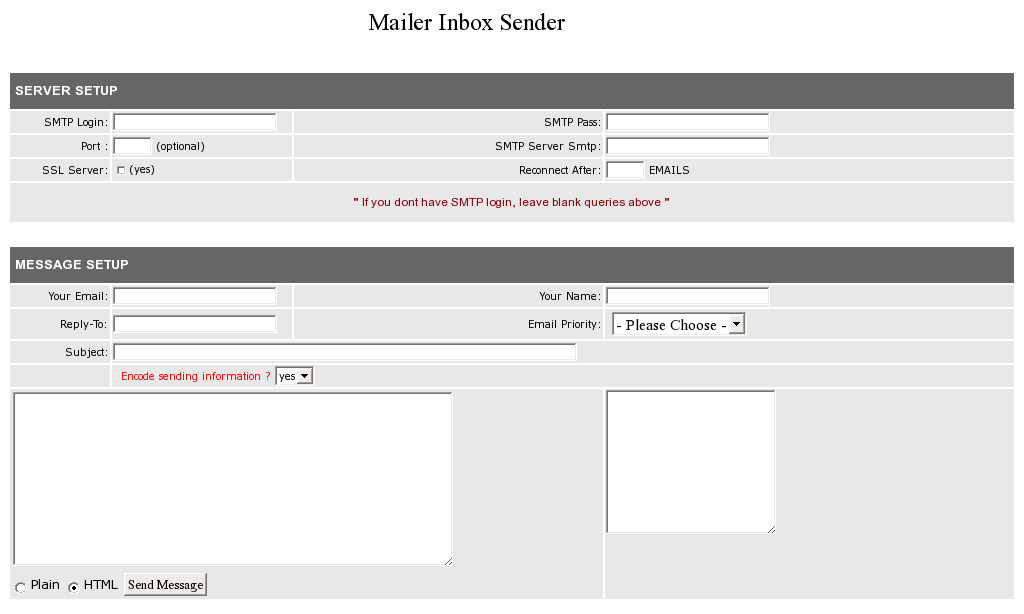
A web shell dedicated to sending spam emails in bulk.
Shell Detection Statistics
Phishing sites and web shells often go hand-in-hand. During April 2017, we detected that approximately 10% of IP addresses hosting phishing attacks were also home to web shells. This pairing is unsurprising, as many web shells give fraudsters an easy to use, all-in-one solution to deploy and spread their attacks. Some brands commonly targeted by phishing sites have significantly higher exposure to web shells than average, such as:
OrganisationPhishing Sites
with Web Shells
SunTrust Bank
The variation in web shell usage according to the targeted organisation highlights the diversity of fraudsters and their preferred targets and methods. Netcraft has seen a number of web shells bundled as part of phishing kits, meaning that certain phishing campaigns will automatically include a web shell hidden alongside the phishing content. These organisations with the highest exposure to web shells should be particularly worried, as any anti-phishing efforts could be rendered ineffectual by persistent reinfections enabled by web shells.
Geographically, the number of web shells tends to follow the size of the web hosting market in any given country. Looking at all the web shells found by Netcraft in April, 49% of infected servers were located in the USA, putting it firmly into first place. Trailing behind at a distant second is Germany, responsible for just under 5% of affected IP addresses.
Website owners should be wary of using hosting companies with web shell infestations on their networks. With web shells being used to send spam and participate in DoS attacks, service quality can be affected as shared infrastructure has to handle the additional load. Compromised servers distributing malware and spam can lead to IP addresses being blacklisted, preventing legitimate emails from being delivered even after the malicious activity has been stopped. Netcraft looked at the hosting companies most responsible for hosting web shells, by counting the number of unique IP addresses with at least one web shell detection in April as a percentage of the total infected IP addresses seen – the top 10 are listed in the table below:
RankHosting CompanyProportion of All
Web Shell IPs
The criminal must defend his web shell against both the webmaster and other fraudsters seeking to usurp his position on the compromised machine. To this end, many shells offer password protection. Passwords are usually hardcoded within the script, and are used without an accompanying username or email identifier.
The reality of this threat is evident when considering the existence of web shells offering ‘shell finders’ – these perform automated scans of websites, probing a long list of potential web shell file paths. The list of paths covers common shell names and directories, as well as paths used by commonly exploited web applications and plugins. Some shells perform this scan against a remote host, while others augment a search of the local filesystem with an overwrite option – allowing a fraudster to lock out others by overwriting their shells with a copy of their own.
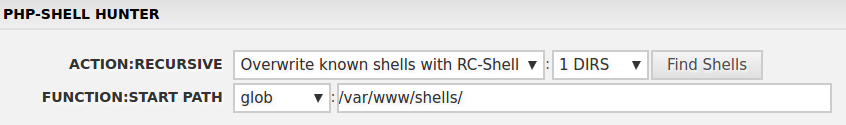
The R57 Shell offers tools to probe the compromised server for other web shell installations, with the option to remove or overwrite them.
Unbeknownst to some fraudsters, these web shells sometimes contain backdoors of their own. Some allow bypass of access controls on the web interface, regardless of changes to the password. Others will automatically attempt to "phone home", notifying the original shell authors of new installations which are then absorbed into larger bot nets. With the trend of remixing (or “recoding”) and rebranding web shells, there are many opportunities for web shell authors to introduce their own backdoors into entire families of related scripts.
Avoiding Detection
Web shell authors try a variety of tricks to avoid detection by other fraudsters, the webmaster himself, and by security companies like Netcraft. A particularly common ploy is that of fake error pages, used by some variants of the C99 web shell. These shells attempt to recreate the default Apache error pages, usually 404 Not Found or 403 Forbidden.
When viewed in a web browser, these fake pages can easily be mistaken for legitimate error messages. However, when compared side-by-side, discrepancies can be found by looking for incorrect or omitted version numbers, hostnames, URLs, and HTML titles. These fake error pages also contain hidden password fields, which provide access to the web shell: some variants simply set the background and border colours to match the page background, while others add JavaScript that reveals the password form when the port number is clicked.

Some shells disguise themselves as default Apache error pages. In this example, there is a password input centered on the page, made invisible by CSS. Typing characters into the input reveals its location.
Another notable method for avoiding detection is prefixing the web shell scripts with small excerpts of image file headers – most commonly those from the GIF89a specification. When processed by the PHP interpreter, these bytes are ignored and passed through to the web browser, displaying the text “GIF89a”. Automated tools such as the open-source utility file use these magic bytes as a fingerprint to identify the file type, mistaking the malicious PHP script for an image.
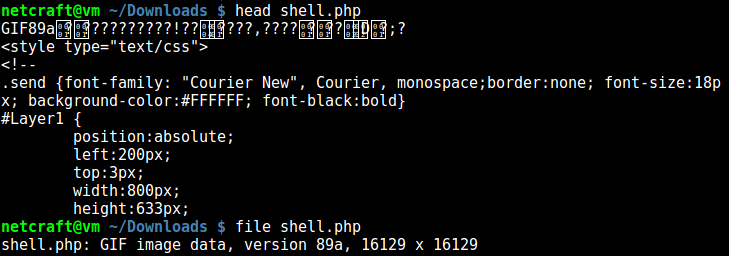
The source code of this web shell is prefixed with GIF image file headers, to mask its identity. The file utility mistakenly identifies the script as a GIF image. With purported dimensions of 16,129 by 16,129 pixels, this image would require 250GB of memory to open!
Fraudsters also attempt to disguise web shell scripts in directory listings by using filenames that could easily be mistaken for legitimate files. For example, Netcraft found a large number of shells masquerading as a WordPress configuration file, wp-config.php. Some shells use this filename verbatim, whilst others will make minor alterations (e.g. wp-configs.php) and hide themselves amongst legitimate WordPress files. By naming shells in this way, it is easy for webmasters to miss these files when examining their servers after compromise.
These countermeasures could mean that phishing or malware attacks may soon resurface, thus it is vital that organisations looking to remove such fraudulent content also seek to remove the web shells that enable it, and fix whatever vulnerabilities allowed the shells to be there in the first place.
How to Protect Yourself?
The onus is on hosting providers, system administrators, and webmasters to ensure that their servers are secured against vulnerabilities that may allow attackers to upload shells to their systems. They should also be on the lookout for unexpected modifications to their web root, paying close attention to popular software packages such as WordPress , where shell scripts are easily disguised amongst benign files.
Hosting providers can receive an alerting service from Netcraft which will notify them whenever phishing, malware, or web shells are detected on their infrastructure. Organisations targeted by high volume phishing administered via web shells may trial Netcraft's Countermeasures service.
Continue reading...

An example of the hugely popular and feature-rich WSO (Web Shell by Orb) shell.
A number of shells offer the creation of a botnet in as little as a click, launching standalone processes that either connect to a command and control server or listen for commands over an insecure TCP connection. Some allow performing port scans to find potentially exploitable services. Others enable fraudsters to schedule denial of service attacks. There are shells dedicated to sending bulk spam emails, testing stolen credentials against popular websites (such as PayPal or Amazon), cracking passwords, and automatically defacing websites. With such a wide array of powerful features, it is unsurprising how popular web shells are with cyber criminals.

WSO offers both bind shell and back connect options. Selecting one of these options will launch a standalone process that will connect to or listen for a connection from a remote command and control server - an easy method for the creation of a botnet.
The prevalence of these backdoors allows easy—and potentially persistent—access to thousands of compromised machines. If the web shell is missed during the webmaster's cleanup after an attack, removing the original phishing or malware content will be in vain, as the fraudster can use the web shell to upload new malicious material, or re-purpose the machine as an accessory to alternative forms of cyber crime.

This shell allows a fraudster to port scan arbitrary hosts anonymously.

A web shell dedicated to sending spam emails in bulk.
Shell Detection Statistics
Phishing sites and web shells often go hand-in-hand. During April 2017, we detected that approximately 10% of IP addresses hosting phishing attacks were also home to web shells. This pairing is unsurprising, as many web shells give fraudsters an easy to use, all-in-one solution to deploy and spread their attacks. Some brands commonly targeted by phishing sites have significantly higher exposure to web shells than average, such as:
OrganisationPhishing Sites
with Web Shells
SunTrust Bank
41%
OurTime39%
Navy Federal Credit Union38%
USAA35%
NetEase33%
Alibaba31%
DHL31%
Bank of America30%
British Telecom30%
NatWest30%
Capital One29%
Bank of Montreal28%
Wells Fargo27%
Yahoo25%
Chase Bank25%
Average (Large Brands)18%
The variation in web shell usage according to the targeted organisation highlights the diversity of fraudsters and their preferred targets and methods. Netcraft has seen a number of web shells bundled as part of phishing kits, meaning that certain phishing campaigns will automatically include a web shell hidden alongside the phishing content. These organisations with the highest exposure to web shells should be particularly worried, as any anti-phishing efforts could be rendered ineffectual by persistent reinfections enabled by web shells.
Geographically, the number of web shells tends to follow the size of the web hosting market in any given country. Looking at all the web shells found by Netcraft in April, 49% of infected servers were located in the USA, putting it firmly into first place. Trailing behind at a distant second is Germany, responsible for just under 5% of affected IP addresses.
Website owners should be wary of using hosting companies with web shell infestations on their networks. With web shells being used to send spam and participate in DoS attacks, service quality can be affected as shared infrastructure has to handle the additional load. Compromised servers distributing malware and spam can lead to IP addresses being blacklisted, preventing legitimate emails from being delivered even after the malicious activity has been stopped. Netcraft looked at the hosting companies most responsible for hosting web shells, by counting the number of unique IP addresses with at least one web shell detection in April as a percentage of the total infected IP addresses seen – the top 10 are listed in the table below:
RankHosting CompanyProportion of All
Web Shell IPs
1
Endurance International Group6.50%
2
GoDaddy2
6.09%
3
OVH3
3.96%
4
Hostinger4
3.12%
5
Hetzner Online5
2.09%
6
Amazon6
1.86%
7
Athenix7
1.52%
8
DigitalOcean8
1.37%
9
InMotion Hosting9
1.33%
10=
Host Europe Group10=
1.18%
10=
LiquidWeb10=
1.18%
Protecting Shells The criminal must defend his web shell against both the webmaster and other fraudsters seeking to usurp his position on the compromised machine. To this end, many shells offer password protection. Passwords are usually hardcoded within the script, and are used without an accompanying username or email identifier.
The reality of this threat is evident when considering the existence of web shells offering ‘shell finders’ – these perform automated scans of websites, probing a long list of potential web shell file paths. The list of paths covers common shell names and directories, as well as paths used by commonly exploited web applications and plugins. Some shells perform this scan against a remote host, while others augment a search of the local filesystem with an overwrite option – allowing a fraudster to lock out others by overwriting their shells with a copy of their own.

The R57 Shell offers tools to probe the compromised server for other web shell installations, with the option to remove or overwrite them.
Unbeknownst to some fraudsters, these web shells sometimes contain backdoors of their own. Some allow bypass of access controls on the web interface, regardless of changes to the password. Others will automatically attempt to "phone home", notifying the original shell authors of new installations which are then absorbed into larger bot nets. With the trend of remixing (or “recoding”) and rebranding web shells, there are many opportunities for web shell authors to introduce their own backdoors into entire families of related scripts.
Avoiding Detection
Web shell authors try a variety of tricks to avoid detection by other fraudsters, the webmaster himself, and by security companies like Netcraft. A particularly common ploy is that of fake error pages, used by some variants of the C99 web shell. These shells attempt to recreate the default Apache error pages, usually 404 Not Found or 403 Forbidden.
When viewed in a web browser, these fake pages can easily be mistaken for legitimate error messages. However, when compared side-by-side, discrepancies can be found by looking for incorrect or omitted version numbers, hostnames, URLs, and HTML titles. These fake error pages also contain hidden password fields, which provide access to the web shell: some variants simply set the background and border colours to match the page background, while others add JavaScript that reveals the password form when the port number is clicked.

Some shells disguise themselves as default Apache error pages. In this example, there is a password input centered on the page, made invisible by CSS. Typing characters into the input reveals its location.
Another notable method for avoiding detection is prefixing the web shell scripts with small excerpts of image file headers – most commonly those from the GIF89a specification. When processed by the PHP interpreter, these bytes are ignored and passed through to the web browser, displaying the text “GIF89a”. Automated tools such as the open-source utility file use these magic bytes as a fingerprint to identify the file type, mistaking the malicious PHP script for an image.

The source code of this web shell is prefixed with GIF image file headers, to mask its identity. The file utility mistakenly identifies the script as a GIF image. With purported dimensions of 16,129 by 16,129 pixels, this image would require 250GB of memory to open!
Fraudsters also attempt to disguise web shell scripts in directory listings by using filenames that could easily be mistaken for legitimate files. For example, Netcraft found a large number of shells masquerading as a WordPress configuration file, wp-config.php. Some shells use this filename verbatim, whilst others will make minor alterations (e.g. wp-configs.php) and hide themselves amongst legitimate WordPress files. By naming shells in this way, it is easy for webmasters to miss these files when examining their servers after compromise.
These countermeasures could mean that phishing or malware attacks may soon resurface, thus it is vital that organisations looking to remove such fraudulent content also seek to remove the web shells that enable it, and fix whatever vulnerabilities allowed the shells to be there in the first place.
How to Protect Yourself?
The onus is on hosting providers, system administrators, and webmasters to ensure that their servers are secured against vulnerabilities that may allow attackers to upload shells to their systems. They should also be on the lookout for unexpected modifications to their web root, paying close attention to popular software packages such as WordPress , where shell scripts are easily disguised amongst benign files.
Hosting providers can receive an alerting service from Netcraft which will notify them whenever phishing, malware, or web shells are detected on their infrastructure. Organisations targeted by high volume phishing administered via web shells may trial Netcraft's Countermeasures service.
Continue reading...

