Despite widespread concerns over the security of the SHA-1 hash algorithm, the US Department of Defense is still issuing SHA-1 signed certificates, and using them to secure connections to .mil websites.
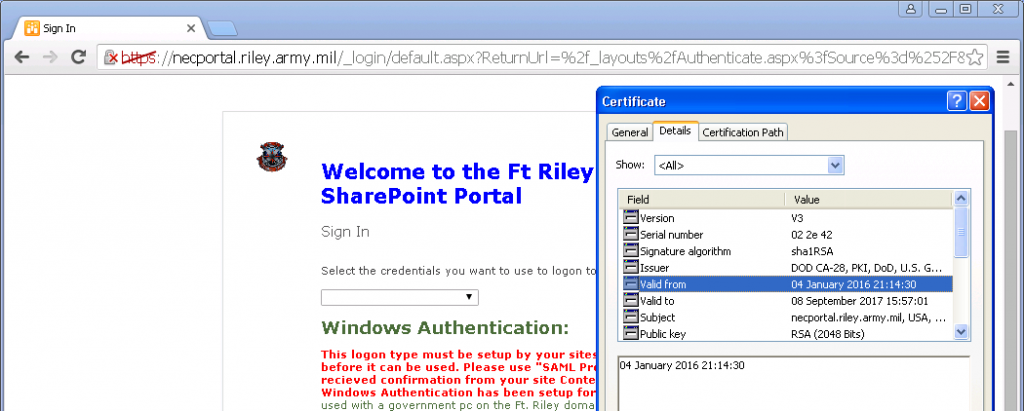
The US DoD issued a SHA-1 signed certificate to necportal.riley.army.mil on 4 January 2016
Since 1 January 2016, the CA/Browser Forum's Baseline Requirements [pdf] have banned the issuance of new SHA-1 certificates. Publicly-trusted certificate authorities are expected to comply with these Baseline Requirements in order to remain trusted by browsers and operating systems.
However, the US DoD is not a publicly-trusted certificate authority per se, and therefore it does not have to abide by the CA/Browser Forum's rules. With the exception of Apple platforms, most browser software does not include the DoD's root certificates by default. This means any secure site that uses a certificate issued by the DoD is unlikely to be trusted by a browser running on Windows or Linux, unless the user has explicitly installed the DoD's root certificates.
Even though the DoD does not have to abide by the CA/Browser Forum's rules, it is arguably a bad idea not to: The SHA-1 algorithm is now thought to be sufficiently weak that a well-funded attacker might be able to find a SHA-1 hash collision and hence impersonate any HTTPS website. It is also particularly surprising to see the DoD still using SHA-1 today when the US National Institute of Standards and Technology banned its use more than two years ago. Since NIST made this decision, the cost projections of finding a SHA-1 hash collision have reduced significantly.
On 4 January 2016, the DoD issued a SHA-1 certificate to necportal.riley.army.mil [site report], which is a SharePoint portal hosted by the United States Army Information Systems Command. It can be accessed remotely by Common Access Card (CAC) holders. The certificate is marked as being valid until 8 September 2017.
The DoD is America's largest government agency, and is tasked with protecting the security of its country, which makes its continued reliance on SHA-1 particularly remarkable. Besides the well known security implications, this reliance could already prove problematic amongst the DoD's millions of employees. For instance, Mozilla Firefox 43 began rejecting all new SHA-1 certificates issued since 1 January 2016. When it encountered one of these certificates, the browser displayed an Untrusted Connection error, although this could be overridden. If DoD employees become accustomed to ignoring such errors, it could become much easier to carry out man-in-the-middle attacks against them.
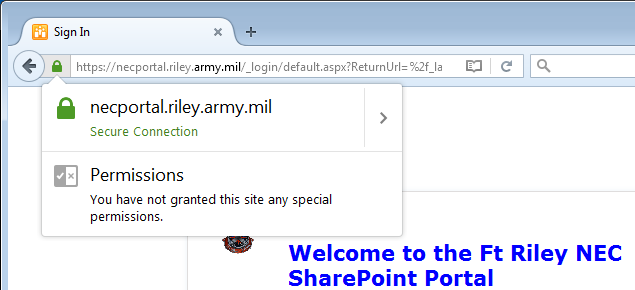
However, the latest version of Firefox no longer rejects SHA-1 certificates issued after 1 January 2016. This change was made to cater for users of certain man-in-the-middle products, which generate freshly issued certificates on the fly. Consequently, users of Firefox 43.0.4 who have installed the appropriate DoD root certificates will currently not receive any errors, or even warnings, when browsing to the site:
Google intends to block all SHA-1 certificates issued from 1 January 2016 with the release of Chrome 48. In the meantime, Chrome 47 affirmatively distrusts the SHA-1 certificate used by necportal.riley.army.mil because it does not expire until 2017.
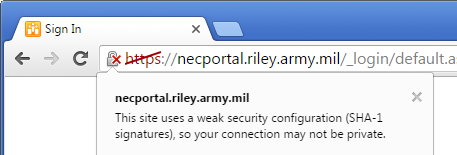
Chrome regards the certificate as affirmatively insecure, even when the appropriate DoD root certificates are installed.
Firefox will ultimately distrust all SHA-1 certificates by 2017, regardless of when they were issued, but Mozilla considered advancing this deadline to as early as 1 July 2016 when the new cost projections were realised.
More than 650,000 SSL certificates in use on the web are still using SHA-1, but this count has been rapidly falling since 2014. Nearly all of these certificates are due to expire by the end of 2016, in accordance with the Baseline Requirements; however, with most browser vendors contemplating an accelerated deprecation timeline, it is likely that many of these certificates will be replaced before the middle of the year.
With the US DoD PKI infrastructure seemingly still reliant on SHA-1, by the end of 2017, the DoD could account for a significant proportion of all SHA-1 certificates that are intended to be used by modern browsers.
Continue reading...

The US DoD issued a SHA-1 signed certificate to necportal.riley.army.mil on 4 January 2016
Since 1 January 2016, the CA/Browser Forum's Baseline Requirements [pdf] have banned the issuance of new SHA-1 certificates. Publicly-trusted certificate authorities are expected to comply with these Baseline Requirements in order to remain trusted by browsers and operating systems.
However, the US DoD is not a publicly-trusted certificate authority per se, and therefore it does not have to abide by the CA/Browser Forum's rules. With the exception of Apple platforms, most browser software does not include the DoD's root certificates by default. This means any secure site that uses a certificate issued by the DoD is unlikely to be trusted by a browser running on Windows or Linux, unless the user has explicitly installed the DoD's root certificates.
Even though the DoD does not have to abide by the CA/Browser Forum's rules, it is arguably a bad idea not to: The SHA-1 algorithm is now thought to be sufficiently weak that a well-funded attacker might be able to find a SHA-1 hash collision and hence impersonate any HTTPS website. It is also particularly surprising to see the DoD still using SHA-1 today when the US National Institute of Standards and Technology banned its use more than two years ago. Since NIST made this decision, the cost projections of finding a SHA-1 hash collision have reduced significantly.
On 4 January 2016, the DoD issued a SHA-1 certificate to necportal.riley.army.mil [site report], which is a SharePoint portal hosted by the United States Army Information Systems Command. It can be accessed remotely by Common Access Card (CAC) holders. The certificate is marked as being valid until 8 September 2017.
The DoD is America's largest government agency, and is tasked with protecting the security of its country, which makes its continued reliance on SHA-1 particularly remarkable. Besides the well known security implications, this reliance could already prove problematic amongst the DoD's millions of employees. For instance, Mozilla Firefox 43 began rejecting all new SHA-1 certificates issued since 1 January 2016. When it encountered one of these certificates, the browser displayed an Untrusted Connection error, although this could be overridden. If DoD employees become accustomed to ignoring such errors, it could become much easier to carry out man-in-the-middle attacks against them.
However, the latest version of Firefox no longer rejects SHA-1 certificates issued after 1 January 2016. This change was made to cater for users of certain man-in-the-middle products, which generate freshly issued certificates on the fly. Consequently, users of Firefox 43.0.4 who have installed the appropriate DoD root certificates will currently not receive any errors, or even warnings, when browsing to the site:

Google intends to block all SHA-1 certificates issued from 1 January 2016 with the release of Chrome 48. In the meantime, Chrome 47 affirmatively distrusts the SHA-1 certificate used by necportal.riley.army.mil because it does not expire until 2017.

Chrome regards the certificate as affirmatively insecure, even when the appropriate DoD root certificates are installed.
Firefox will ultimately distrust all SHA-1 certificates by 2017, regardless of when they were issued, but Mozilla considered advancing this deadline to as early as 1 July 2016 when the new cost projections were realised.
More than 650,000 SSL certificates in use on the web are still using SHA-1, but this count has been rapidly falling since 2014. Nearly all of these certificates are due to expire by the end of 2016, in accordance with the Baseline Requirements; however, with most browser vendors contemplating an accelerated deprecation timeline, it is likely that many of these certificates will be replaced before the middle of the year.
With the US DoD PKI infrastructure seemingly still reliant on SHA-1, by the end of 2017, the DoD could account for a significant proportion of all SHA-1 certificates that are intended to be used by modern browsers.
Continue reading...

