Thousands of phishing sites have been finding homes in special hidden directories on compromised web servers.
In the past month alone, over 400 new phishing sites were found hosted within directories named /.well-known/; but rather than being created by fraudsters, these special directories are already present on millions of websites.

A Microsoft Excel Online phishing site hosted in the /.well-known/ directory on a compromised web server. The phishing site piggybacks on the trust instilled by the compromised site's existing SSL certificate, which has not been revoked.
The /.well-known/ directory acts as a URI path prefix for "well-known locations", as defined by IETF RFC 5785, and provides a way for both humans and automated processes to discover a website's policies and other information.
One of the most common legitimate uses of the /.well-known/ directory is to prove control over a domain. When a secure website uses the Automatic Certificate Management Environment (ACME) protocol to manage its SSL certificate, the issuer will verify ownership by checking for a unique token in /.well-known/acme-challenge/ or /.well-known/pki-validation/. Consequently, most of the phishing attacks that make use of the /.well-known/ directory have been deployed on sites that support HTTPS, using certificates issued by ACME-driven certificate authorities like Let's Encrypt and cPanel.
Due to the success of Let's Encrypt and ACME, millions of websites now have a /.well-known/ directory in their web root, although many website administrators may be oblivious to its presence – particularly if they did not create the directory themselves. The directory can also easily be overlooked, as a bare ls command will treat files or directories that start with a "." as hidden. These factors make /.well-known/ an ideal place to smuggle phish onto a compromised web server.
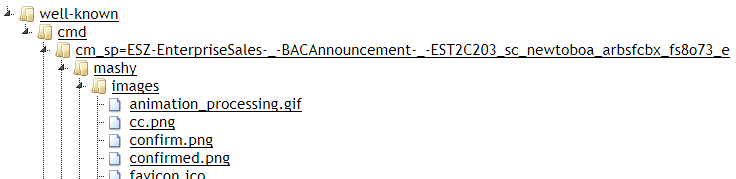
Around 3% of these phishing sites are mistakenly deployed in a /well-known/ directory, without a leading "." character. This mistake could stem from file system name limitations if the phishing kit was created on a Windows computer. This screenshot shows a Bank of America phishing kit that would be installed in a /well-known/ directory when unzipped.
Shared hosting platforms are particularly vulnerable to misuse if the file system permissions on the /.well-known/ directories are overly permissive, allowing one website to place content on another customer's website. Some of the individual servers involved in these attacks were hosting "well-known" phishing sites for multiple hostnames, which lends weight to this hypothesis.
Other well-known URIs
In addition to pki-validation and acme-challenge, there are 30 other widely recognised well-known URI suffixes defined by the IETF, W3C and others. For example, the EFF came up with the dnt-policy.txt suffix, which allows websites to announce their compliance with user opt-outs from tracking. The EFF's own Do Not Track Compliance Policy can be viewed at https://www.eff.org/.well-known/dnt-policy.txt.
Where multiple resources may be required, the well-known URI suffix is a directory rather than a file. For example, the IETF's Enrollment over Secure Transport RFC defines a set of resources that can be found under the /.well-known/est/ path.
Despite there being several other well-known URI directory suffixes, only pki-validation and acme-challenge have been used to host recent phishing sites. In fact, more than half of the phishing sites found under the /.well-known/ directory were planted within the subdirectories created by ACME clients (i.e. /.well-known/pki-validation/ and /.well-known/acme-challenge/), possibly making them even less likely to be noticed by the website administrators.
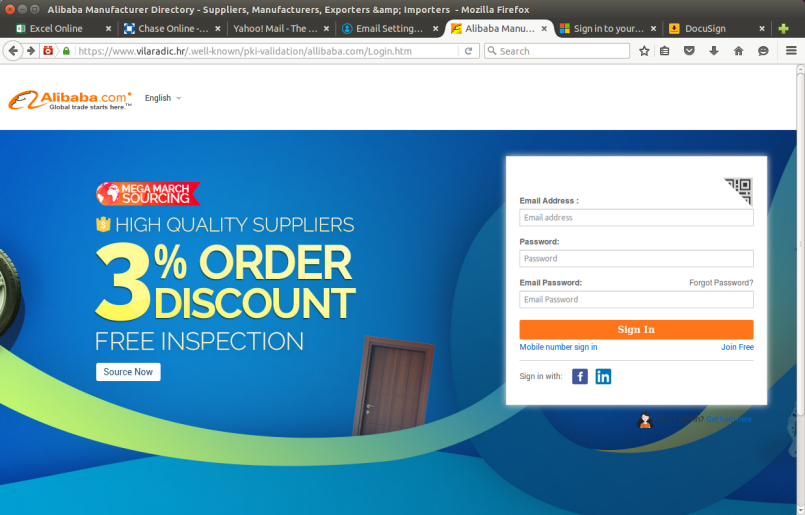
An Alibaba phishing site. More than half of all "well-known" phishing sites are installed in the directories used by ACME clients, although this does not necessarily mean the ACME clients are to blame.
The possible route of compromise is not always apparent in the aforementioned cases, but if there are any glaring security misconfigurations, a proposed new well-known URI suffix, security.txt, could come in handy. By placing contact details and disclosure policies in /.well-known/security.txt, website administrators can make it safer and easier for security researchers to reach out and report any problems they find.
Continue reading...
In the past month alone, over 400 new phishing sites were found hosted within directories named /.well-known/; but rather than being created by fraudsters, these special directories are already present on millions of websites.

A Microsoft Excel Online phishing site hosted in the /.well-known/ directory on a compromised web server. The phishing site piggybacks on the trust instilled by the compromised site's existing SSL certificate, which has not been revoked.
The /.well-known/ directory acts as a URI path prefix for "well-known locations", as defined by IETF RFC 5785, and provides a way for both humans and automated processes to discover a website's policies and other information.
One of the most common legitimate uses of the /.well-known/ directory is to prove control over a domain. When a secure website uses the Automatic Certificate Management Environment (ACME) protocol to manage its SSL certificate, the issuer will verify ownership by checking for a unique token in /.well-known/acme-challenge/ or /.well-known/pki-validation/. Consequently, most of the phishing attacks that make use of the /.well-known/ directory have been deployed on sites that support HTTPS, using certificates issued by ACME-driven certificate authorities like Let's Encrypt and cPanel.
Due to the success of Let's Encrypt and ACME, millions of websites now have a /.well-known/ directory in their web root, although many website administrators may be oblivious to its presence – particularly if they did not create the directory themselves. The directory can also easily be overlooked, as a bare ls command will treat files or directories that start with a "." as hidden. These factors make /.well-known/ an ideal place to smuggle phish onto a compromised web server.

Around 3% of these phishing sites are mistakenly deployed in a /well-known/ directory, without a leading "." character. This mistake could stem from file system name limitations if the phishing kit was created on a Windows computer. This screenshot shows a Bank of America phishing kit that would be installed in a /well-known/ directory when unzipped.
Shared hosting platforms are particularly vulnerable to misuse if the file system permissions on the /.well-known/ directories are overly permissive, allowing one website to place content on another customer's website. Some of the individual servers involved in these attacks were hosting "well-known" phishing sites for multiple hostnames, which lends weight to this hypothesis.
Other well-known URIs
In addition to pki-validation and acme-challenge, there are 30 other widely recognised well-known URI suffixes defined by the IETF, W3C and others. For example, the EFF came up with the dnt-policy.txt suffix, which allows websites to announce their compliance with user opt-outs from tracking. The EFF's own Do Not Track Compliance Policy can be viewed at https://www.eff.org/.well-known/dnt-policy.txt.
Where multiple resources may be required, the well-known URI suffix is a directory rather than a file. For example, the IETF's Enrollment over Secure Transport RFC defines a set of resources that can be found under the /.well-known/est/ path.
Despite there being several other well-known URI directory suffixes, only pki-validation and acme-challenge have been used to host recent phishing sites. In fact, more than half of the phishing sites found under the /.well-known/ directory were planted within the subdirectories created by ACME clients (i.e. /.well-known/pki-validation/ and /.well-known/acme-challenge/), possibly making them even less likely to be noticed by the website administrators.

An Alibaba phishing site. More than half of all "well-known" phishing sites are installed in the directories used by ACME clients, although this does not necessarily mean the ACME clients are to blame.
The possible route of compromise is not always apparent in the aforementioned cases, but if there are any glaring security misconfigurations, a proposed new well-known URI suffix, security.txt, could come in handy. By placing contact details and disclosure policies in /.well-known/security.txt, website administrators can make it safer and easier for security researchers to reach out and report any problems they find.
Continue reading...

