My company produces an appliance (PHP/Web User Interface) based on FreeBSD (11.1) and recently, the sudo package was updated from 1.8.22 to 1.8.23. We have a couple of restricted shell logins for customer maintenance issues and after the upgrade, one of the restricted commands (which is a shell script with a sudo cat <file>) no longer works (it worked just fine prior to the sudo package update and, if I down-rev the package, it will continue to work). I've attached a screenshot of the console output when trying to execute the command when it fails.
We need to upgrade to FreeBSD12 where we won't be able to down-rev the sudo package (nor would we want to). From some research, we've discovered that in 1.8.23, sudo was re-engineered to use PAM and this, I believe, is where we are having issues. Does anyone have some insight as to how we can get commands like these to work again under the newer versions of sudo?
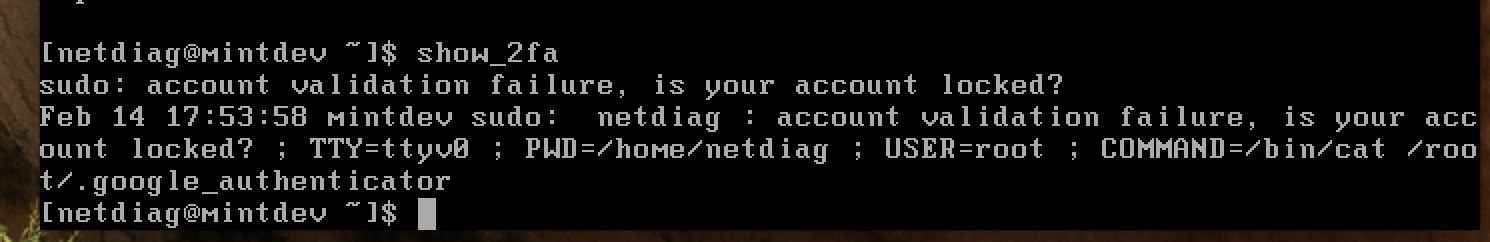
We need to upgrade to FreeBSD12 where we won't be able to down-rev the sudo package (nor would we want to). From some research, we've discovered that in 1.8.23, sudo was re-engineered to use PAM and this, I believe, is where we are having issues. Does anyone have some insight as to how we can get commands like these to work again under the newer versions of sudo?

