zirias@
Developer
I have a service roughly designed like this:
- a main thread dispatching connections using
- a pool of worker threads doing the actual processing of the requests, the individual processing jobs doing quite some dynamic allocations but of course freeing them again before finishing
The only libs linked are libc, libthr and libz.
Now, I observed the following with
I also did a test without zlib, just to make sure it's not some zlib-internal memory-management. Obviously isn't.
Now my question is: am I chasing some phantom here? Maybe that's just how
Or do I have a leak somewhere that valgrind can't find?
- a main thread dispatching connections using
pselect(), allocating some context and request objects and freeing them again once the response is sent- a pool of worker threads doing the actual processing of the requests, the individual processing jobs doing quite some dynamic allocations but of course freeing them again before finishing
The only libs linked are libc, libthr and libz.
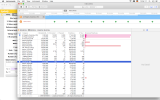
Now, I observed the following with
ps: The RES value increases with every request processed. I used devel/valgrind to debug this, found one little leak indeed, fixed it, but the behavior is still the same, with valgrind reporting no leaks whatsoever.I also did a test without zlib, just to make sure it's not some zlib-internal memory-management. Obviously isn't.
Now my question is: am I chasing some phantom here? Maybe that's just how
malloc() and/or the pager work? Serving you "new" pages cause it's faster and only cleaning up the old ones when really necessary?Or do I have a leak somewhere that valgrind can't find?