Cybersecurity giant Comodo can't even keep its own website secure | TechCrunch
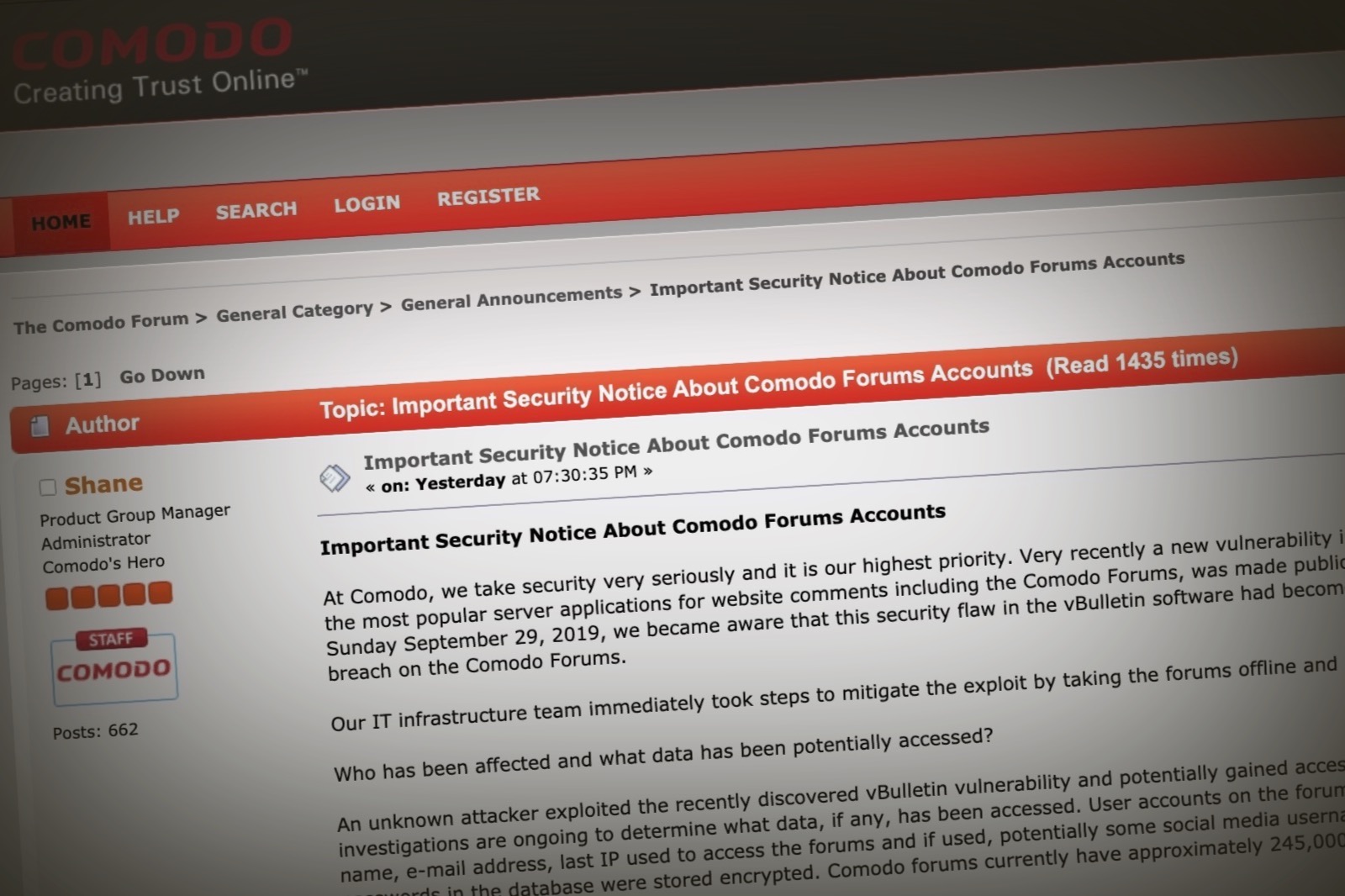
Comodo, which bills itself as a "global leader in cybersecurity solutions," said its forum was hacked. The admission came in no less than a forum post,
"A hacker gained access to internal files and documents owned by security company and former SSL certificate issuer Comodo by using an email address and password mistakenly exposed on the internet. The credentials were found in a public GitHub repository owned by a Comodo software developer ....."
The world is full of dumb-ass professional experts - LOL


