Below is the UI for the router we use for in-housing hosting.
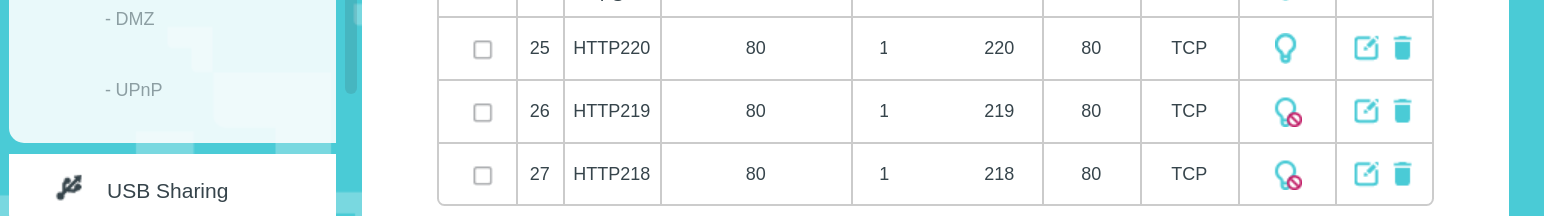
We have multiple web services running on multiple servers and the PF & Haproxy have been well-configured to redirect packets to the appropriate servers.
Before now, the router has been behaving well. By behaving well, I mean all the HTTPXXX entries [in the above image] were in the "on" status and all services were running. Out of the blue, the whole network went down. We fiddled with PF rules for a week. Part of it has to do with us trying additional features to ALTQ, such as FIBs and miniupnpd. And now that everything is up and running again, the router is now acting up.
According to the above diagram, only websites using the IP address with the last octet 220 are reachable. The 443 port nat forwarding is also set for that IP address [though not shown above]. As at now, we can only choose one at a time - disable 220 and enable 219, etc. As I said before, they were all enabled at one time. The router also gives other troubles, such as disabling all and never able to enable any or add new entries for that port. Of course, this would happen to any port number with multiple IP addresses.
What are our options?
1) PFSense mini-itx: If we place the router in a bridge mode, can we use any mini-itx running PFSense to connect to our NBN/VDSL or do we have to look for a hardware with such feature. In this case, PPPoE authentication will be handed over to the device connected to the router. Any recommendation for PFSense hardware?
2) Run other web services at other port numbers: We are worried that some services will require further tweaking; not only the Apache/HAproxy/NGINX would need to be tweeked. We tried Domain forwarding on our DNS settings but would not work.
3) Bundle PFSense to a decommisioned laptop; attach an additional NIC (external) to the laptop, set up router in the bridge mode and PFSense; and finally connect the laptop to another router {for wifi and wired connections} via the external NIC.
4)......
On the other hand, we are also now running a DHCP server in one of the FreeBSD jails via a dedicated interface (ix0). While it allocates IP addresses, the gateway with host [on another interface -igb0] do not provide Internet connection to the DHCP clients. PF keeps blocking incoming packet no matter what changes we made. We tried "route-to" based on a few examples [1, 2] on the Internet but no luck. We tried if we could route packets via the host interface (igb0) and another interface in it (ix1) that is connected to the router using the router's DHCP but no luck too.
References:
1) https://www.openbsd.org/faq/pf/pools.html#outgoing
2) https://calomel.org/pf_config.html [Example: Two external ISP connections using route-to and round-robin]
We have multiple web services running on multiple servers and the PF & Haproxy have been well-configured to redirect packets to the appropriate servers.
Before now, the router has been behaving well. By behaving well, I mean all the HTTPXXX entries [in the above image] were in the "on" status and all services were running. Out of the blue, the whole network went down. We fiddled with PF rules for a week. Part of it has to do with us trying additional features to ALTQ, such as FIBs and miniupnpd. And now that everything is up and running again, the router is now acting up.
According to the above diagram, only websites using the IP address with the last octet 220 are reachable. The 443 port nat forwarding is also set for that IP address [though not shown above]. As at now, we can only choose one at a time - disable 220 and enable 219, etc. As I said before, they were all enabled at one time. The router also gives other troubles, such as disabling all and never able to enable any or add new entries for that port. Of course, this would happen to any port number with multiple IP addresses.
What are our options?
1) PFSense mini-itx: If we place the router in a bridge mode, can we use any mini-itx running PFSense to connect to our NBN/VDSL or do we have to look for a hardware with such feature. In this case, PPPoE authentication will be handed over to the device connected to the router. Any recommendation for PFSense hardware?
2) Run other web services at other port numbers: We are worried that some services will require further tweaking; not only the Apache/HAproxy/NGINX would need to be tweeked. We tried Domain forwarding on our DNS settings but would not work.
3) Bundle PFSense to a decommisioned laptop; attach an additional NIC (external) to the laptop, set up router in the bridge mode and PFSense; and finally connect the laptop to another router {for wifi and wired connections} via the external NIC.
4)......
On the other hand, we are also now running a DHCP server in one of the FreeBSD jails via a dedicated interface (ix0). While it allocates IP addresses, the gateway with host [on another interface -igb0] do not provide Internet connection to the DHCP clients. PF keeps blocking incoming packet no matter what changes we made. We tried "route-to" based on a few examples [1, 2] on the Internet but no luck. We tried if we could route packets via the host interface (igb0) and another interface in it (ix1) that is connected to the router using the router's DHCP but no luck too.
References:
1) https://www.openbsd.org/faq/pf/pools.html#outgoing
2) https://calomel.org/pf_config.html [Example: Two external ISP connections using route-to and round-robin]

