J
Joe Hewett
Guest
FreeBSD, The FreeBSD Foundation, and The FreeBSD Forums are not associated with the content of this article.
New Threat Intelligence confirms connections underpinning pig butchering and investment scams
Much like companies in the legitimate economy, criminals also specialize: focusing on their core strengths and using third-party Software-as-a-Service platforms and tools to outsource the rest of the business or criminal infrastructure needed. These Crime-as-a-Service providers continue to evolve, from bulletproof hosting to Phishing-as-a-Service (PhaaS).
New threat intelligence from Netcraft has uncovered the connections in the underlying financial infrastructure supporting fraud networks around the globe. This includes insights exposing centralized Mule-as-a-Service (MaaS) providers being used by seemingly unconnected threat actors around the globe to launder their scam proceeds through money mule bank accounts.
Examining the connections between the underlying cyber and financial infrastructure reveals a rich and interconnected network of mule accounts held at local and global banks, phone numbers, crypto addresses, payment app accounts, and email addresses being used to commit fraud. These connections not only give a mechanism to aid in identifying threat actors, but also new opportunities to disrupt crime groups involved in pig butchering, romance scams, and widespread, complex cyber-enabled fraud.
Netcraft’s Conversational Scam Intelligence (CSI) platform brings together Netcraft’s unique threat intelligence and generative AI to engage with threat actors in long-form peer-to-peer conversations at scale. These private conversations can last over a year and span hundreds of messages. Interactions with threat actors also serve as foundational data, used by Netcraft researchers to connect seemingly disparate scams to expose criminal actors around the globe.
Netcraft researchers recently explored the Darcula Phishing-as-a-Service network, and insight suggests that similar providers exist for money mule accounts at banks globally, from the smallest credit unions to the largest banking giants. Definitive evidence has been limited about the inner workings of criminal mule account networks, including the existence of underlying “as a service” groups. Among the earliest and most accessible forms of public evidence are mule recruitment campaigns on social media platforms, which Netcraft researchers have monitored for some time. These campaigns offer the promise of making some fast cash, with little to no effort.

Figure 1 – Social Media ads recruiting potential mules for criminal exploits.
Using the data gathered from real-life scams conducted by Netcraft’s generative AI personas, Netcraft’s research team has mapped the connections in the data linking scams with the ultimate money transfer mechanisms used to cash out. In the following examples we’ve mapped different elements of criminal infrastructure (email addresses, mule account numbers, crypto wallet addresses, phone numbers) uncovered by Netcraft.
These nodes are aligned to the conversation where they were shared. For example, a text message conversation containing a phone number would connect a
 conversation node to
conversation node to
 a phone number node.
a phone number node.
As a simple example, Netcraft classified this inbound, unsolicited email as Advance Fee Fraud:
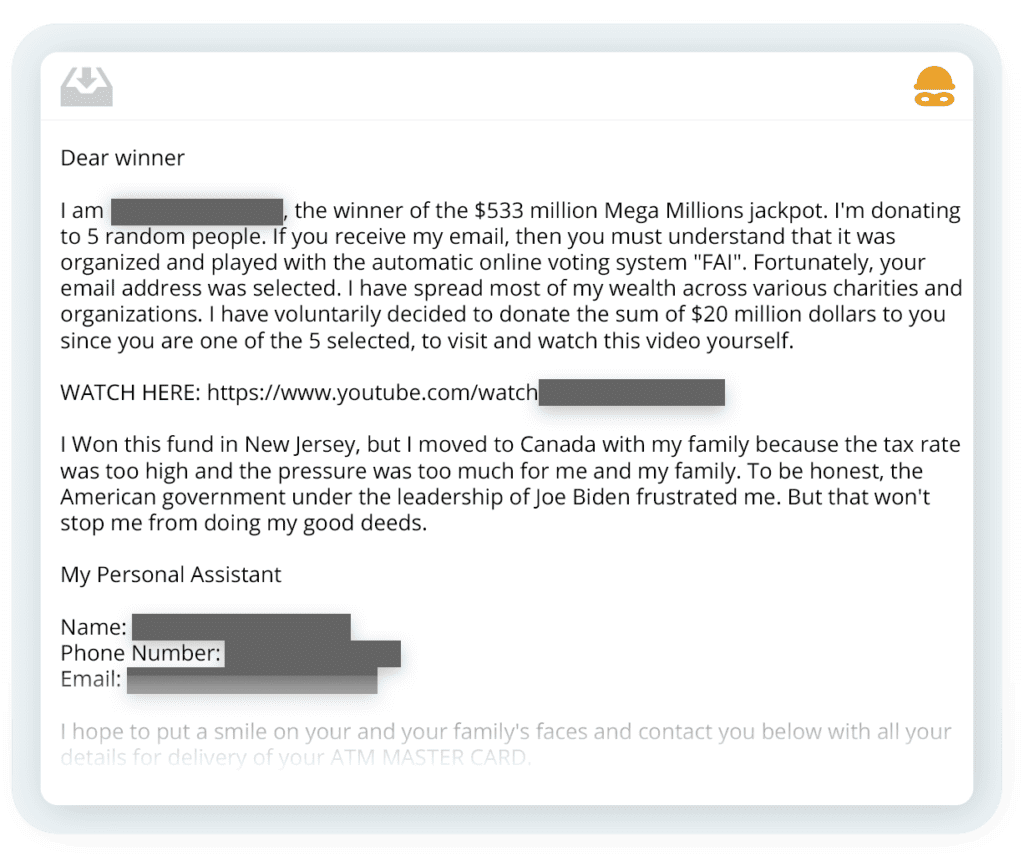
Figure 2 – This email, identified through Netcraft’s threat intelligence, was used to initiate an AI-powered dialogue with the scammer. To protect the integrity of the data, the email has been slightly altered and identifiable information redacted.
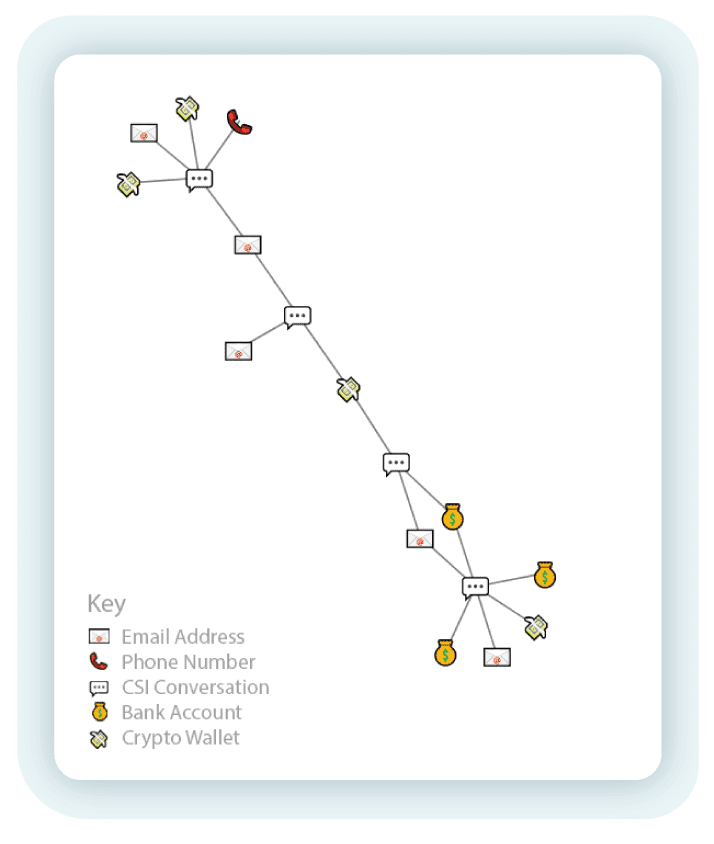
Figure 3 – The email conversation in figure 2 is depicted by “
 ” in the bottom right of the infrastructure network shown here. The conversation exposed the simple but connected infrastructure network visualized above.
” in the bottom right of the infrastructure network shown here. The conversation exposed the simple but connected infrastructure network visualized above.
This simple example consists of 17 messages from the threat actor and 10 replies from Netcraft over the course of approximately one month. In that time we were able to expose the following infrastructure and fraud network connection points:
This simple example demonstrates how Netcraft can effectively map the infrastructure powering threat actor campaigns, providing a much deeper picture of the underlying criminal operation.
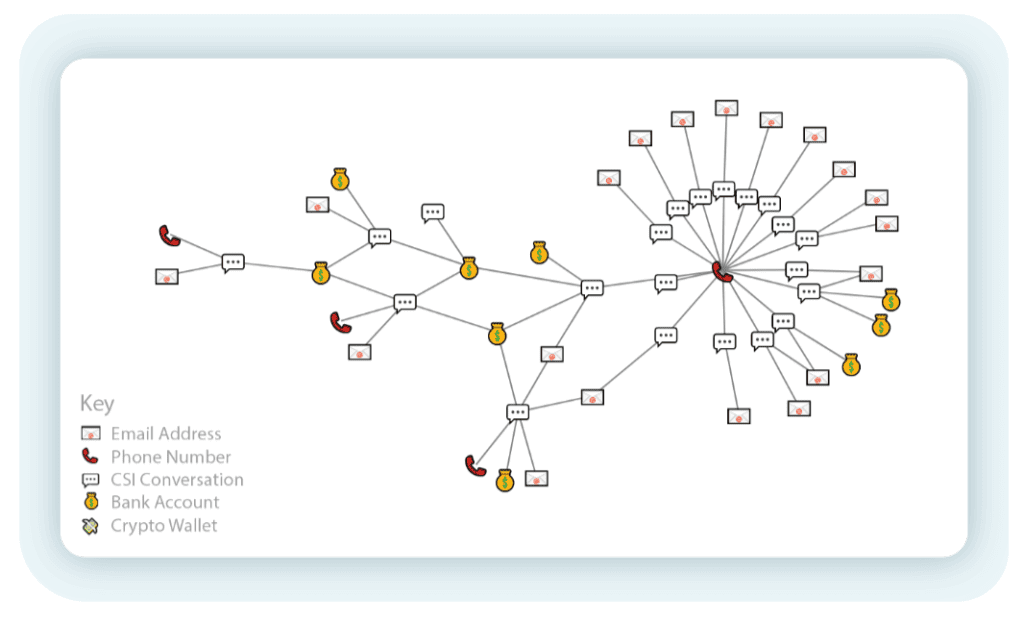
Figure 4 – Multiple conversations can be tied to the same threat actor based on their shared reliance on a single piece of infrastructure (in this case a phone number).
In other cases like the one above, seemingly disconnected conversations can be attributed to the same threat actor (an individual or a wider group). See the following analysis that links these conversations:
In this case, the cluster allows us to conclude that nine mule accounts and 19 email addresses are in use by the same threat actor to defraud the customers of at least two separate financial institutions.
While some infrastructure is spread out with small clusters, this region shows scammer infrastructure that is quite densely connected. Seen here are dozens of bank accounts, emails and phone numbers, likely all being used by the same group of scammers:
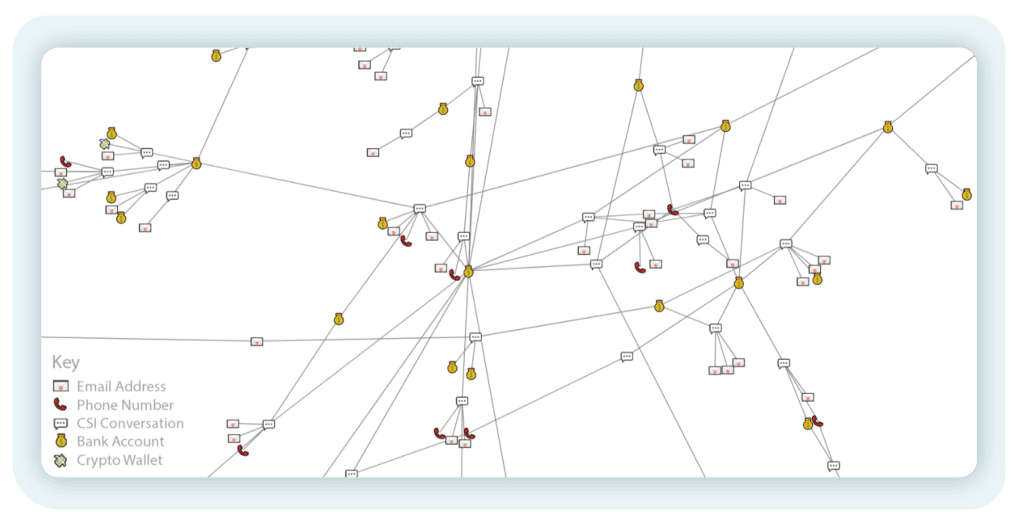
Figure 5 – A subsection of a wide network of highly connected scammer infrastructure.
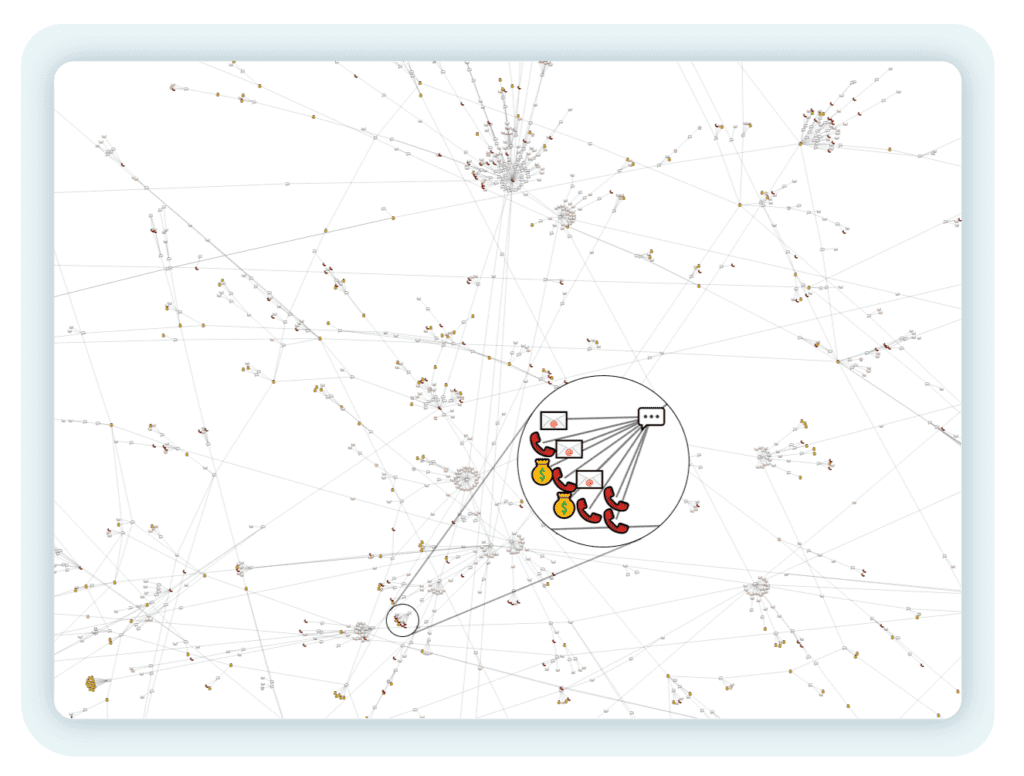
Figure 6 – An even larger network of interconnected scammer infrastructure.
Mapping relationships between scammer infrastructure can uncover weak points in scam campaigns. In figure 6 we see how dozens of investment scam emails and conversations hinge on a single UK-based phone number.
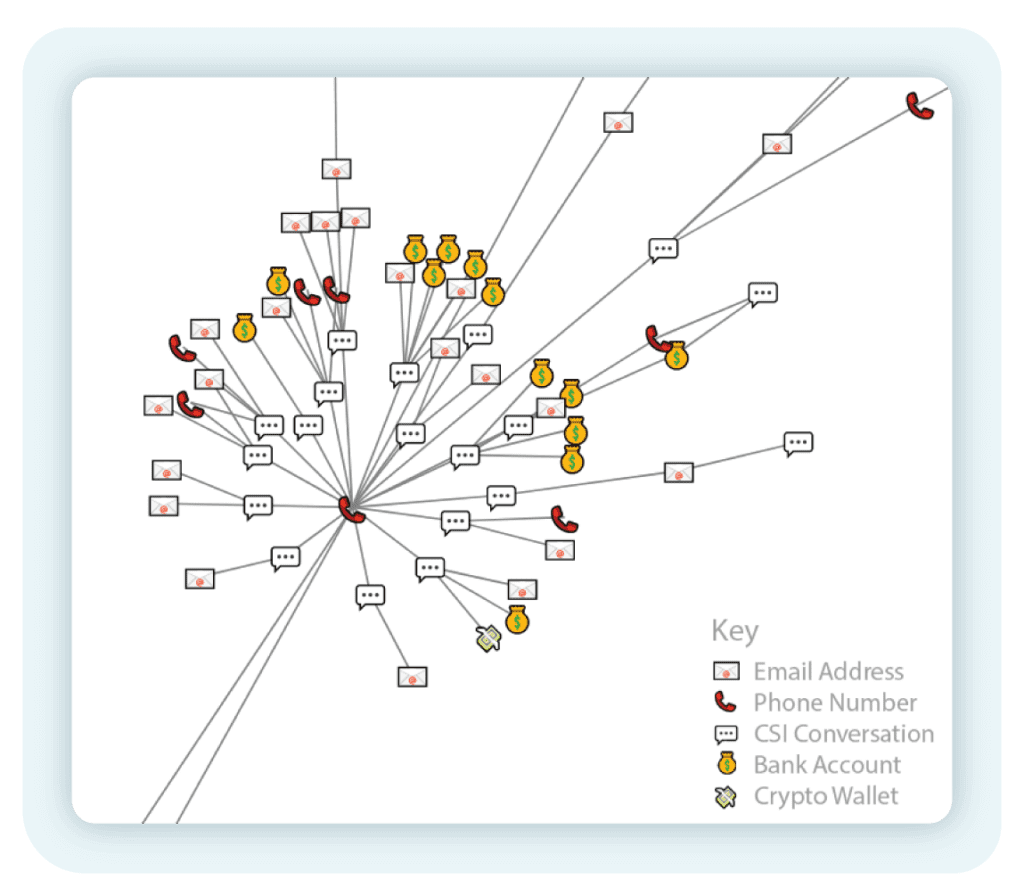
Figure 7 – An investment scam campaign reliant on a single phone number exposing a single point weakness in this threat actor’s infrastructure, which when taken down could cause significant disruption for the criminal.
In this group, we see a bank account referenced by at least 23 different email addresses being used for fraud. This bank account was first seen four months ago and was last seen as recently as four hours before the time of writing. Clusters of this form could indicate a fraud operation which is heavily dependent on a single payment account.
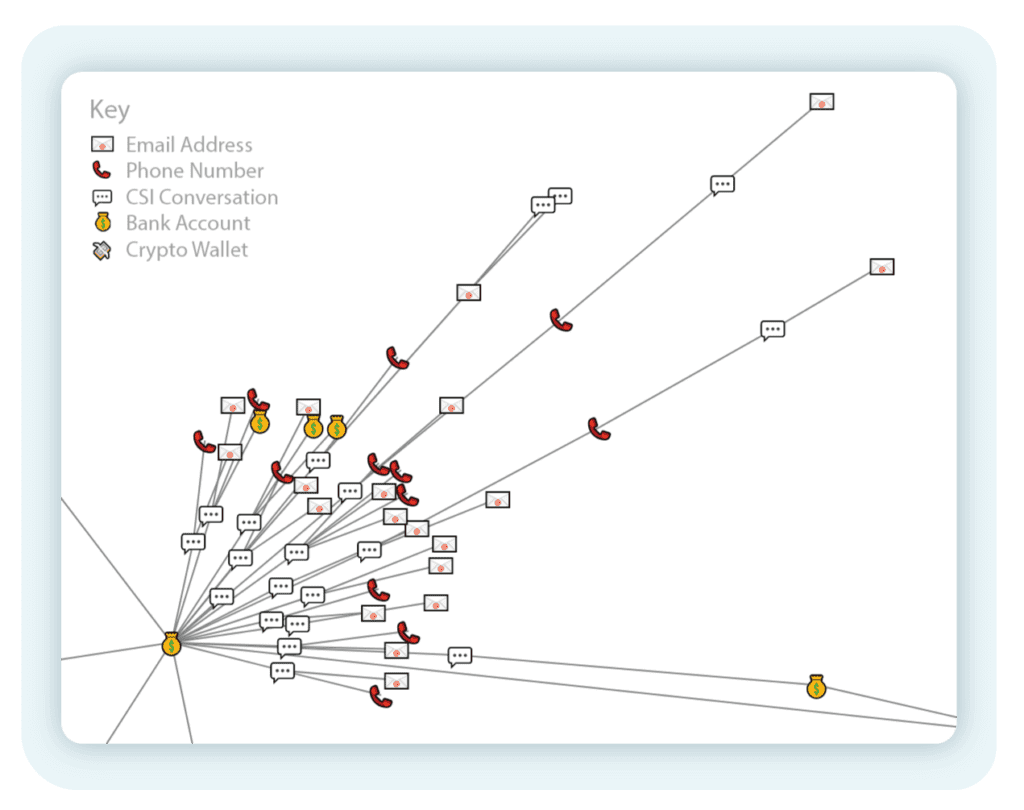
Figure 8 – 23 emails across 23 conversations engaged in by the Conversational Scam Intelligence system that all point back to the same bank account.
Zooming out, we can observe that the two bank accounts we have just analyzed have been referenced in the same conversation:
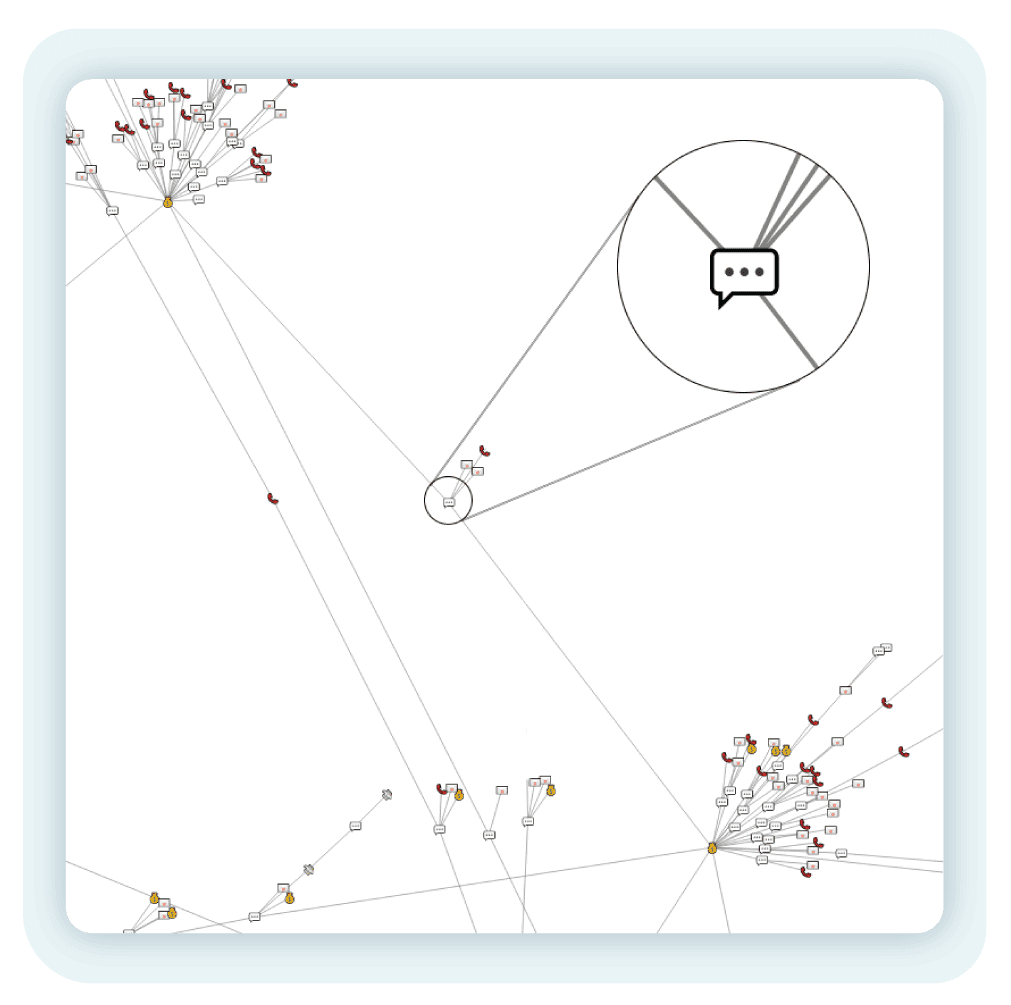
Figure 9 – The two highly-connected bank accounts in the above images are connected by a conversation which references both.
Inspecting that conversation further gives more clues as to the origin of this operation. The following cluster suggests that distinct fraud groups share the same mule accounts:
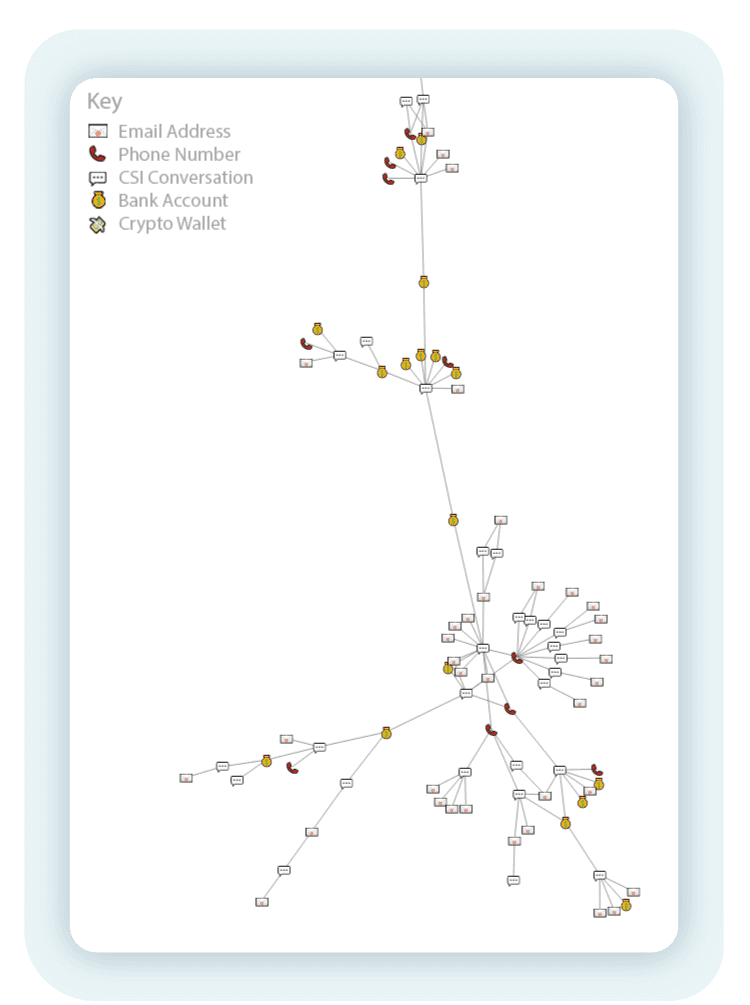
Figure 10 – This network shows seemingly disconnected operations that appear to be sharing mule accounts, indicating that the mules are operated by Mule-as-a-Service providers.
At the top of this section of the network, multiple pieces of information indicate that the fraudsters are operating from Benin, including the use of +229 phone numbers.
However, at the bottom we see a network of related infrastructure that revolves around Spain-based phone numbers, like a +34 Xfera Moviles mobile number, or a different +34 Vozelia Telecom fixed number.
The unifying factor between these seemingly distinct operations is a single Italian mule bank account.
Given that these operations appear independently in two countries separated by thousands of miles, their use of a shared bank account suggests that they are not ultimately in control of the mule.Instead, they are making use of centralized Mule-as-a-Service providers in charge of receiving and sending on defrauded funds.
Losses to investment scams, romance fraud, and pig butchering reached $4.6 billion in the United States – a 38% increase in 2023. These scams are very often conducted in private peer-to-peer conversations and the ability to stop the scam often comes too late.
Studying the connections between threat actors and centralized Mule-as-a-Service providers provide a unique opportunity to both understand and ultimately deeply disrupt criminal payment networks powering scams, pig butchering, cyber-enabled fraud, and more.
By identifying and disrupting weaknesses in financial infrastructure, like those shown here, security leaders are now able to proactively find and interrupt mule account activity, block payments to known mule accounts outside their institution, stop payments to criminal crypto wallets, and deploy countermeasures against the greatest points of vulnerability, thus crippling criminal infrastructure and protecting their clients.
For almost three decades, the Netcraft team has been developing and using innovative, proprietary solutions to expose,disrupt, and eradicate criminal activity. Netcraft’s Conversational Scam Intelligence, recently announced at RSA ‘24, now provides the data and insight needed to expose, map, and disrupt these scams at any scale.
Connect with Netcraft’s expert team to see how we can help you. Request more information on Conversational Scam Intelligence here.
New Threat Intelligence confirms connections underpinning pig butchering and investment scams
Much like companies in the legitimate economy, criminals also specialize: focusing on their core strengths and using third-party Software-as-a-Service platforms and tools to outsource the rest of the business or criminal infrastructure needed. These Crime-as-a-Service providers continue to evolve, from bulletproof hosting to Phishing-as-a-Service (PhaaS).
New threat intelligence from Netcraft has uncovered the connections in the underlying financial infrastructure supporting fraud networks around the globe. This includes insights exposing centralized Mule-as-a-Service (MaaS) providers being used by seemingly unconnected threat actors around the globe to launder their scam proceeds through money mule bank accounts.
Examining the connections between the underlying cyber and financial infrastructure reveals a rich and interconnected network of mule accounts held at local and global banks, phone numbers, crypto addresses, payment app accounts, and email addresses being used to commit fraud. These connections not only give a mechanism to aid in identifying threat actors, but also new opportunities to disrupt crime groups involved in pig butchering, romance scams, and widespread, complex cyber-enabled fraud.
Netcraft’s Conversational Scam Intelligence (CSI) platform brings together Netcraft’s unique threat intelligence and generative AI to engage with threat actors in long-form peer-to-peer conversations at scale. These private conversations can last over a year and span hundreds of messages. Interactions with threat actors also serve as foundational data, used by Netcraft researchers to connect seemingly disparate scams to expose criminal actors around the globe.
Building a MaaS army
Netcraft researchers recently explored the Darcula Phishing-as-a-Service network, and insight suggests that similar providers exist for money mule accounts at banks globally, from the smallest credit unions to the largest banking giants. Definitive evidence has been limited about the inner workings of criminal mule account networks, including the existence of underlying “as a service” groups. Among the earliest and most accessible forms of public evidence are mule recruitment campaigns on social media platforms, which Netcraft researchers have monitored for some time. These campaigns offer the promise of making some fast cash, with little to no effort.

Figure 1 – Social Media ads recruiting potential mules for criminal exploits.
Mapping connections in fraud networks
Using the data gathered from real-life scams conducted by Netcraft’s generative AI personas, Netcraft’s research team has mapped the connections in the data linking scams with the ultimate money transfer mechanisms used to cash out. In the following examples we’ve mapped different elements of criminal infrastructure (email addresses, mule account numbers, crypto wallet addresses, phone numbers) uncovered by Netcraft.
These nodes are aligned to the conversation where they were shared. For example, a text message conversation containing a phone number would connect a


You’re too kind
As a simple example, Netcraft classified this inbound, unsolicited email as Advance Fee Fraud:

Figure 2 – This email, identified through Netcraft’s threat intelligence, was used to initiate an AI-powered dialogue with the scammer. To protect the integrity of the data, the email has been slightly altered and identifiable information redacted.

Figure 3 – The email conversation in figure 2 is depicted by “

This simple example consists of 17 messages from the threat actor and 10 replies from Netcraft over the course of approximately one month. In that time we were able to expose the following infrastructure and fraud network connection points:
- Initial email address as well as a secondary email address being used to accept payments via PayPal
- The payment address was previously mentioned in a separate conversation impersonating a delivery company, allowing Netcraft to connect the two conversations
- This other conversation had already uncovered a Bitcoin wallet which has transacted over 2,000 times on the Bitcoin network, receiving a total of 12 BTC (~$805,000 at the time of writing)
- Connected to this address in a separate conversation was another US-based bank account and another email address
- Both of these had been seen in a conversation connecting the Bitcoin wallet, to a Wells Fargo account and a JPMorgan Chase account
This simple example demonstrates how Netcraft can effectively map the infrastructure powering threat actor campaigns, providing a much deeper picture of the underlying criminal operation.
You’ve got mail

Figure 4 – Multiple conversations can be tied to the same threat actor based on their shared reliance on a single piece of infrastructure (in this case a phone number).
In other cases like the one above, seemingly disconnected conversations can be attributed to the same threat actor (an individual or a wider group). See the following analysis that links these conversations:
- In this cluster, 14 email addresses identified in Netcraft threat intelligence were targeting a Spanish bank. Conversations requested victims call the same phone number, allowing Netcraft to conclude that these emails, despite their varying email addresses, were all the work of one threat actor.
- In a separate conversation, the scammer used the same phone number as used in this campaign. That conversation unearthed three bank accounts, one of which Netcraft had seen before in a previous conversation.
- That previous conversation, in turn, referenced another bank account which Netcraft had previously seen in a conversation associated with a Scottish bank.
In this case, the cluster allows us to conclude that nine mule accounts and 19 email addresses are in use by the same threat actor to defraud the customers of at least two separate financial institutions.
One ring-ring to rule them all
While some infrastructure is spread out with small clusters, this region shows scammer infrastructure that is quite densely connected. Seen here are dozens of bank accounts, emails and phone numbers, likely all being used by the same group of scammers:

Figure 5 – A subsection of a wide network of highly connected scammer infrastructure.

Figure 6 – An even larger network of interconnected scammer infrastructure.
Mapping relationships between scammer infrastructure can uncover weak points in scam campaigns. In figure 6 we see how dozens of investment scam emails and conversations hinge on a single UK-based phone number.

Figure 7 – An investment scam campaign reliant on a single phone number exposing a single point weakness in this threat actor’s infrastructure, which when taken down could cause significant disruption for the criminal.
In this group, we see a bank account referenced by at least 23 different email addresses being used for fraud. This bank account was first seen four months ago and was last seen as recently as four hours before the time of writing. Clusters of this form could indicate a fraud operation which is heavily dependent on a single payment account.

Figure 8 – 23 emails across 23 conversations engaged in by the Conversational Scam Intelligence system that all point back to the same bank account.
Zooming out, we can observe that the two bank accounts we have just analyzed have been referenced in the same conversation:

Figure 9 – The two highly-connected bank accounts in the above images are connected by a conversation which references both.
Inspecting that conversation further gives more clues as to the origin of this operation. The following cluster suggests that distinct fraud groups share the same mule accounts:

Figure 10 – This network shows seemingly disconnected operations that appear to be sharing mule accounts, indicating that the mules are operated by Mule-as-a-Service providers.
At the top of this section of the network, multiple pieces of information indicate that the fraudsters are operating from Benin, including the use of +229 phone numbers.
However, at the bottom we see a network of related infrastructure that revolves around Spain-based phone numbers, like a +34 Xfera Moviles mobile number, or a different +34 Vozelia Telecom fixed number.
The unifying factor between these seemingly distinct operations is a single Italian mule bank account.
Given that these operations appear independently in two countries separated by thousands of miles, their use of a shared bank account suggests that they are not ultimately in control of the mule.Instead, they are making use of centralized Mule-as-a-Service providers in charge of receiving and sending on defrauded funds.
So, what’s next?
Losses to investment scams, romance fraud, and pig butchering reached $4.6 billion in the United States – a 38% increase in 2023. These scams are very often conducted in private peer-to-peer conversations and the ability to stop the scam often comes too late.
Studying the connections between threat actors and centralized Mule-as-a-Service providers provide a unique opportunity to both understand and ultimately deeply disrupt criminal payment networks powering scams, pig butchering, cyber-enabled fraud, and more.
By identifying and disrupting weaknesses in financial infrastructure, like those shown here, security leaders are now able to proactively find and interrupt mule account activity, block payments to known mule accounts outside their institution, stop payments to criminal crypto wallets, and deploy countermeasures against the greatest points of vulnerability, thus crippling criminal infrastructure and protecting their clients.
For almost three decades, the Netcraft team has been developing and using innovative, proprietary solutions to expose,disrupt, and eradicate criminal activity. Netcraft’s Conversational Scam Intelligence, recently announced at RSA ‘24, now provides the data and insight needed to expose, map, and disrupt these scams at any scale.
Connect with Netcraft’s expert team to see how we can help you. Request more information on Conversational Scam Intelligence here.

