Hi folks!
I would like to make a tunnel between the Cisco router and the FreeBSD host, but I can’t write the rules in ipsec.txt correctly.
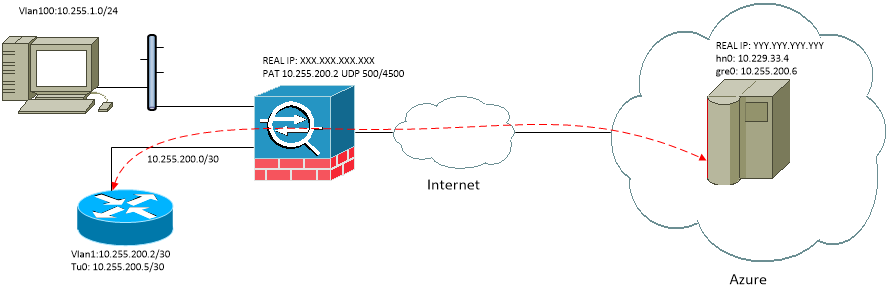
My Cisco router is behind ASA firewall and have PAT rules for ports UDP:500, UDP:4500. I also have another working IPSec VTI tunnels on router.
My router config:
My FreeBSD config (current ipsec.txt content is a cry of despair)
IPSec is work fine, but I can't reach anyone except my internal network:
Why all packets from FreeBSD router in to tunnel?
Control access list on Cisco side of tunnel:
I would like to make a tunnel between the Cisco router and the FreeBSD host, but I can’t write the rules in ipsec.txt correctly.
My Cisco router is behind ASA firewall and have PAT rules for ports UDP:500, UDP:4500. I also have another working IPSec VTI tunnels on router.
My router config:
Code:
crypto keyring MyTo
pre-shared-key address YYY.YYY.YYY.YYY key Megakey
!
crypto isakmp policy 10
encr aes 256
authentication pre-share
group 2
!
crypto isakmp policy 20
encr 3des
authentication pre-share
group 2
crypto isakmp invalid-spi-recovery
crypto isakmp keepalive 120 20 periodic
crypto isakmp nat keepalive 20
crypto isakmp profile MyTo
keyring MyTo
match identity address YYY.YYY.YYY.YYY 255.255.255.255
initiate mode aggressive
!
crypto ipsec transform-set MyNet esp-aes 256 esp-sha-hmac
!
!
crypto ipsec profile MyTo
set transform-set MyNet
set pfs group2
set isakmp-profile MyTo
!
!
interface Tunnel10
description --- To ---
ip address 10.255.200.5 255.255.255.252
tunnel source Vlan1
tunnel mode ipsec ipv4
tunnel destination YYY.YYY.YYY.YYY
tunnel protection ipsec profile MyTo
!
ip route 10.229.33.4 255.255.255.255 10.255.200.6My FreeBSD config (current ipsec.txt content is a cry of despair)
Code:
/usr/local/etc/racoon/racoon.conf:
path pre_shared_key "/usr/local/etc/racoon/key.txt";
log notify;
listen {
isakmp 10.229.33.4 [500];
isakmp_natt 10.229.33.4 [4500];
}
remote XXX.XXX.XXX.XXX {
exchange_mode aggressive,base,main;
nat_traversal on;
my_identifier address 23.100.43.215;
peers_identifier address 10.255.200.2;
lifetime time 86400 sec;
generate_policy on;
dpd_delay 25;
proposal_check obey; # obey, strict, or claim
proposal {
encryption_algorithm aes 256;
authentication_method pre_shared_key;
hash_algorithm sha1;
dh_group 2;
}
}
sainfo anonymous
{
encryption_algorithm aes 256;
authentication_algorithm hmac_sha1;
pfs_group 2;
compression_algorithm deflate;
}
cat /usr/local/etc/racoon/ipsec.conf
spdadd -4 10.229.33.4/32 10.229.33.0/24 any -P out none;
spdadd -4 10.229.33.0/24 10.229.33.4/32 any -P in none;
spdadd -4 10.255.200.6/32 10.255.1.0/24 any -P out ipsec esp/tunnel/10.229.33.4-XXX.XXX.XXX.XXX/unique;
spdadd -4 10.255.1.0/24 10.255.200.6/32 any -P in ipsec esp/tunnel/XXX.XXX.XXX.XXX-10.229.33.4/unique;IPSec is work fine, but I can't reach anyone except my internal network:
Code:
vpn#sh cry isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id status
YYY.YYY.YYY.YYY 10.255.200.2 QM_IDLE 2081 ACTIVE
vpn#ping 10.229.33.4
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.229.33.4, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 208/208/208 ms
vpn#ping 10.255.200.6
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.255.200.6, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 208/208/208 msWhy all packets from FreeBSD router in to tunnel?
Code:
[user@srv ~]$ netstat -arnf inet
Routing tables
Internet:
Destination Gateway Flags Netif Expire
default 10.229.33.1 UGS hn0
10.229.33.0/24 link#2 U hn0
10.229.33.4 link#2 UHS lo0
10.255.0.0/16 10.255.200.5 UGS gre0
10.255.200.5 link#3 UH gre0
10.255.200.6 link#3 UHS lo0
127.0.0.1 link#1 UH lo0
168.63.129.16/32 10.229.33.1 UGS hn0
169.254.169.254/32 10.229.33.1 UGS hn0Control access list on Cisco side of tunnel:
Code:
Sep 19 10:48:39: %SEC-6-IPACCESSLOGNP: list 1 permitted 0 10.229.33.4 -> 114.33.74.20, 1 packet
Sep 19 10:48:41: %SEC-6-IPACCESSLOGNP: list 1 permitted 0 10.229.33.4 -> 76.164.234.122, 1 packet
Sep 19 10:48:42: %SEC-6-IPACCESSLOGNP: list 1 permitted 0 10.229.33.4 -> 220.134.214.57, 1 packet
Sep 19 10:48:44: %SEC-6-IPACCESSLOGNP: list 1 permitted 0 10.229.33.4 -> 118.170.49.247, 1 packet
