Hi!
tail -f /var/log/security
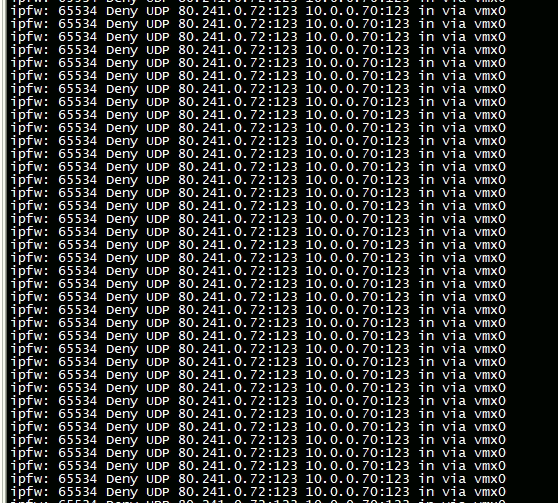
Someone is scanning port 123 through the UDP. But he does this through the global network directly to my local network. How is this possible? How to stop him?
em0 is down
defaultrouter = "10.0.0.1"
This is pfsense local ip.
He is going from another country:
80.241.0.72:123(Kazakhstan) -> pfsense(10.0.0.1) -> 10.0.0.70
tail -f /var/log/security
Code:
em0: flags=8c02<BROADCAST,OACTIVE,SIMPLEX,MULTICAST> metric 0 mtu 1500
options=81009b<RXCSUM,TXCSUM,VLAN_MTU,VLAN_HWTAGGING,VLAN_HWCSUM,VLAN_HWFILTER>
ether xx:xx:xx:xx:xx:xx
inet xxx.xxx.xxx.xxx netmask 0xxxxxxxxx broadcast xxx.xxx.xxx.xxx
media: Ethernet autoselect (1000baseT <full-duplex>)
status: active
nd6 options=29<PERFORMNUD,IFDISABLED,AUTO_LINKLOCAL>
vmx0: flags=8843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST> metric 0 mtu 1500
options=60039b<RXCSUM,TXCSUM,VLAN_MTU,VLAN_HWTAGGING,VLAN_HWCSUM,TSO4,TSO6,RXCSUM_IPV6,TXCSUM_IPV6>
ether xx:xx:xx:xx:xx:xx
inet 10.0.0.70 netmask 0xffffff00 broadcast 10.0.0.255
media: Ethernet autoselect
status: active
nd6 options=29<PERFORMNUD,IFDISABLED,AUTO_LINKLOCAL>
lo0: flags=8049<UP,LOOPBACK,RUNNING,MULTICAST> metric 0 mtu 16384
options=680003<RXCSUM,TXCSUM,LINKSTATE,RXCSUM_IPV6,TXCSUM_IPV6>
inet6 ::1 prefixlen 128
inet6 fe80::1%lo0 prefixlen 64 scopeid 0x3
inet 127.0.0.1 netmask 0xff000000
groups: lo
nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL>Someone is scanning port 123 through the UDP. But he does this through the global network directly to my local network. How is this possible? How to stop him?
em0 is down
defaultrouter = "10.0.0.1"
This is pfsense local ip.
He is going from another country:
80.241.0.72:123(Kazakhstan) -> pfsense(10.0.0.1) -> 10.0.0.70

