D
Deleted member 55181
Guest
http://www.q3k.org/slides-recon-2018.pdf
https://translate.google.com/translate?sl=pl&tl=en&js=y&prev=_t&hl=pl&ie=UTF-8&u=https://zaufanatrzeciastrona.pl/post/jak-dwoch-naszych-rodakow-uparlo-sie-by-odblokowac-bios-laptopa/&edit-text=&act=url
This is one of the best stories we have ever heard. It includes hardware hacking, reverse engineering, cryptography and the admirable stubbornness of two men who wanted to unlock the Toshiba laptop. And it took them only three years.
https://translate.google.com/translate?sl=pl&tl=en&js=y&prev=_t&hl=pl&ie=UTF-8&u=https://zaufanatrzeciastrona.pl/post/jak-dwoch-naszych-rodakow-uparlo-sie-by-odblokowac-bios-laptopa/&edit-text=&act=url
This is one of the best stories we have ever heard. It includes hardware hacking, reverse engineering, cryptography and the admirable stubbornness of two men who wanted to unlock the Toshiba laptop. And it took them only three years.
For the first time, we had the pleasure to hear the story almost a year ago at the Security PWNing 2017 conference. However, the subject was so complex that with the publication of the article we were waiting for the publication of the presentation, to verify that we all remembered everything. The recording is now available, so it's time to describe this unusual journey of two fanatics.
The origins of history
If you have 50 minutes, it's worth to watch the original recording. Unfortunately, the voice path at least partly does not come from speaker microphones, which is not the easiest thing to do. But, as the Chinese say, better rice than than - the recording below, and under it a version for people who do not have 50 minutes free or suffer, listening to the rumble of a poor recording. We have suffered for you.
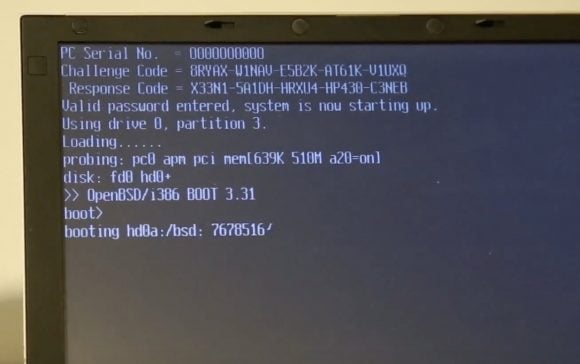
The protagonists of history are Michał "Redford" Kowalczyk, Sergiusz "q3k" Bazański and Toshiba Portégé R100 laptop. Someone asked someone to ask for a password reset on a laptop. This seemingly easy task, however, turned out to be quite complicated. It was a password at the BIOS level, which was not called for any popular trick type, batteries and other hardware tricks. The Internet, however, hinted that pressing the combination Ctrl + Tab Ctrl + Enter calls the service technician, which allows you to bypass the password. On the screen, however, there is a question in the form of "Challenge Code", which must be answered by giving the "Response Code". It sounds like a hacker job. The owner of the laptop at this stage resigned, but Sergiusz was just starting to spin, so he got three identical blocked laptops and Michał's cooperation with Allegro and they got to work.
They decided to start by accessing the BIOS code. They could not get it from the operating system memory of the locked computer. You could also dump the contents of the bones after desoldering - but why bother to have BIOS updates on the network? Michał therefore downloaded the appropriate files from the manufacturer and analyzed them. He identified the file containing the BIOS code, but it contained compressed data in an unknown format. He could have analyzed the code of the updating program, but this one was created in 16-bit architecture, which is not very pleasant to analyze. However, he managed to find a newer 32-bit updater - and this he could easily cope with. Michał wrote a short program that uses the functions of the found updater and unpacked the BIOS update file that interests them.
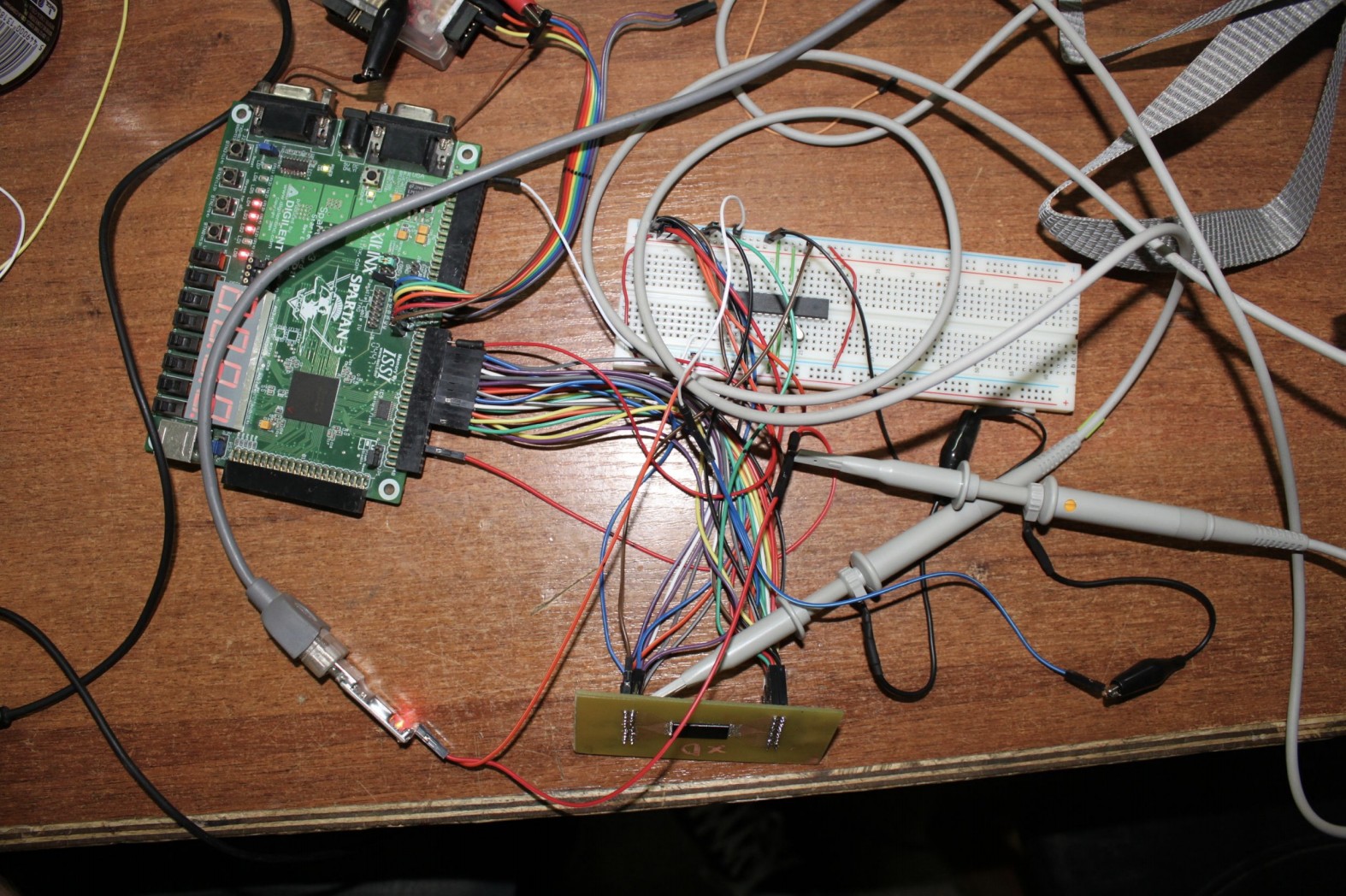
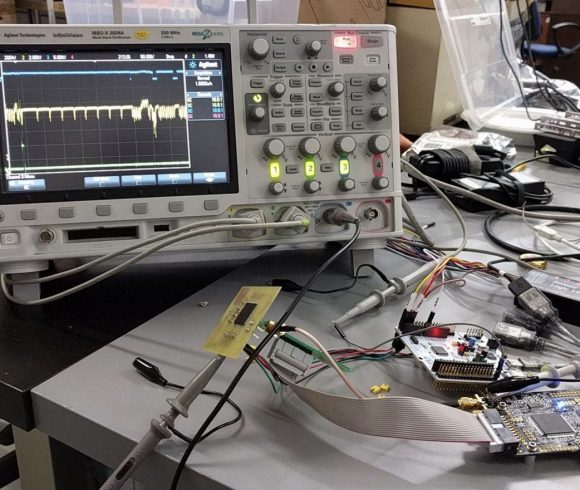
When Michał was struggling with the update file, Sergius was involved in dropping the content of flash bones. The history of how the plate was prepared, etched, the chip was soldered, soldered and connected to the fans of such combinations. It looked like this:

Dumping was burdened for many reasons with errors, which is why it was carried out several dozen times and the correct values for each byte were determined by selecting the ones that occurred most frequently.
Interestingly, the work on unpacking the update and dropping the bone content ended on the same day, so the researchers could compare the results of their work and it turned out that only one byte in the dumped memory was wrong.
Time for analysis
So we have a file with a size of about 500 KB, in which you need to find the right piece of code responsible for calculating the correct answer code for the system question. Michał dealt with the problem. We will not take you here on a trip, which was defeated by Michał, because it's too complicated for us (greetings to the readers of the third volume of textbooks from Intel) - we are willing to send you back to about 2:30 pm in the film . You will learn by the way what happens when you start the processor.
After completing all the necessary magical procedures, Michał located a piece of code displaying a question about the BIOS unblocking code. It turned out, however, that all the elements of the password entry process went to one function, which sends them to certain ports and receives them from them. Further analysis showed that these ports are responsible for communication with another integrated circuit, which is probably responsible for checking the correctness of the password or response in the challenge-response scheme. This other arrangement turned out to be a keyboard controller, also performing several other functions. So it was there that you had to look for the code responsible for unlocking your laptop.
The second layout
Unfortunately, we could not find the right software updates for this model. Fortunately, however, there were updates for the layout of a very similar computer model, the Toshiba Portégé S100. It turned out, however, that the update code is loaded directly into the keyboard controller, which unpacks it itself without first unpacking it in the operating system. Thanks to this, the packaging / encryption algorithm never has to leave the updated bone. Statistical tests of the code showed that the code is rather encrypted than compressed. A task for Sergius.
Sergiusz again had to prepare the appropriate tile, desolder the original system, solder and dump its contents. However, dumping has been very difficult for many reasons . The explanation is long, but the conclusion was one - without knowledge of the secret key, it would be impossible to drop the contents of the bone. Sergius, therefore, began to look for a different path.

After several attempts at known attacks, he noticed that it was possible to guess the key. Well, if he tested all possible combinations of the first key byte, then at one of them the system responded by 3 microseconds longer. This helped, in many attempts, to determine the content of the entire key, byte by byte. With the key they could dump the layout code. Among other things, they found the code to check the key byte by byte, which after the first discrepancy ended checking, which caused a difference in response time used in the attack.
The analysis of the code was not easy again - but we would leave the explanation of its complexity to Michał , because no one will do it better. When Michał reached the code responsible for verifying the correctness of the password, he was a little scared, because this call was again in another system. Fortunately, this layout turned out to be just an EPROM that stored the user password MD5 hashes. However, this was not the main goal of the study - the need to desolder the circuit board makes the attack on the password is not practical. The goal was to be able to unlock any laptop, i.e. analysis of the challenge-response code.
The code turned out to be non-trivial, but it can be analyzed. There were some random data, some related to the hardware, XOR and a dedicated 64-bit block cipher using keys permanently stored in the software. Our heroes rewrote the code in Python and obtained in this way the ability to generate the correct codes in the challenge-response pattern, which they showed live during the presentation.

Applause was fully deserved.
However, this was not enough for Michał and Sergiusz - because they left an un-encrypted keyboard controller update along the way. The system used symmetric cryptography, so having its keys could gain access to the code. So they downloaded software updates for newer laptop models and realized that the algorithms and keys had remained unchanged for at least 14 years. Why change the code that works? In this way, Michał and Sergius could unlock any of Toshiba's latest laptops and create malicious software for the keyboard controller layout, for example by placing a backdoor that was unnoticeable to the user.
The whole operation took Michał and Sergiusz three years - although, as they admitted, the majority of that time constituted Michael's expectation until Sergey desoldered what was needed. Toshiba promised software update that removes the ability to break BIOS security and attack the keyboard controller. Michał and Sergiusz deserve applause and praise - it's worth going to conferences for such presentations. Here you will find their slides in the English version . Please, do more! And the opportunity soon - because the next PWNing edition is November 19-20, 2018 .
==================================================
OTHERS:

