Hi.
First post here.
Seeing strange things on FreeBSD/PF that puzzles us. We cant get pfSense developers in on this so elevating things to FreeBSD forums.
This is tested on current and all earlier versions of pfSense, m0n0wall and the current forked version of pfSense (OPNsense).
We have tested bare metal, hypervisor (ESXi 4.1, 5.0, 5.5 and 6.0). All showing the same behaviour.
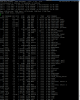
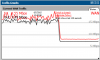
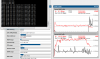
After the initial flooding of packets, then the traffic drops overall and the firewall begins to route packets again. There is no change in the flooding, but until the traffic drop, one core sees 100% and suddenly drops and then packets begin to flow again.
Thread on pfSense forums is here, https://forum.pfsense.org/index.php?topic=91856.0, but it's long and for some quite boring.
Pictures are attached.




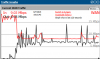
Load on the hypervisor

The drop in load is when the drop in traffic occurs and it begins to route packets.
Any suggestions to why this is happening?
We have tested igb, em and vmxnet2 and 3 adapters. The best is em driver by far.
First post here.
Seeing strange things on FreeBSD/PF that puzzles us. We cant get pfSense developers in on this so elevating things to FreeBSD forums.
This is tested on current and all earlier versions of pfSense, m0n0wall and the current forked version of pfSense (OPNsense).
We have tested bare metal, hypervisor (ESXi 4.1, 5.0, 5.5 and 6.0). All showing the same behaviour.
After the initial flooding of packets, then the traffic drops overall and the firewall begins to route packets again. There is no change in the flooding, but until the traffic drop, one core sees 100% and suddenly drops and then packets begin to flow again.
Thread on pfSense forums is here, https://forum.pfsense.org/index.php?topic=91856.0, but it's long and for some quite boring.
Pictures are attached.
Load on the hypervisor
The drop in load is when the drop in traffic occurs and it begins to route packets.
Any suggestions to why this is happening?
We have tested igb, em and vmxnet2 and 3 adapters. The best is em driver by far.