Alliteration aside, Netcraft has found and blocked the first phishing site to be hosted on the homepage of a .fish generic top-level domain (gTLD).
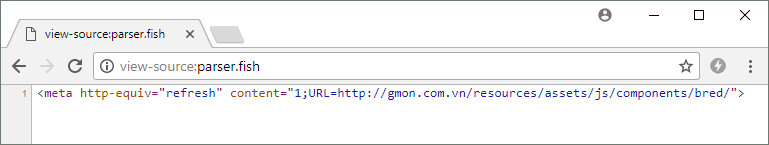
Ripe for crappie puns: A single roe of malicious phishing content hosted on a .fish website.
While a few phishing sites have been found using the .fish and .fishing gTLDs before, parser.fish became the first to host malicious phishing content directly on its homepage. Fraudsters lured unsuspecting suckers to the fishy site, where a cheeky 99-char meta redirect sent them off to a separate phishing site hosted in Vietnam. This then attempted to steal online banking credentials by impersonating the French banking cooperative, BRED.
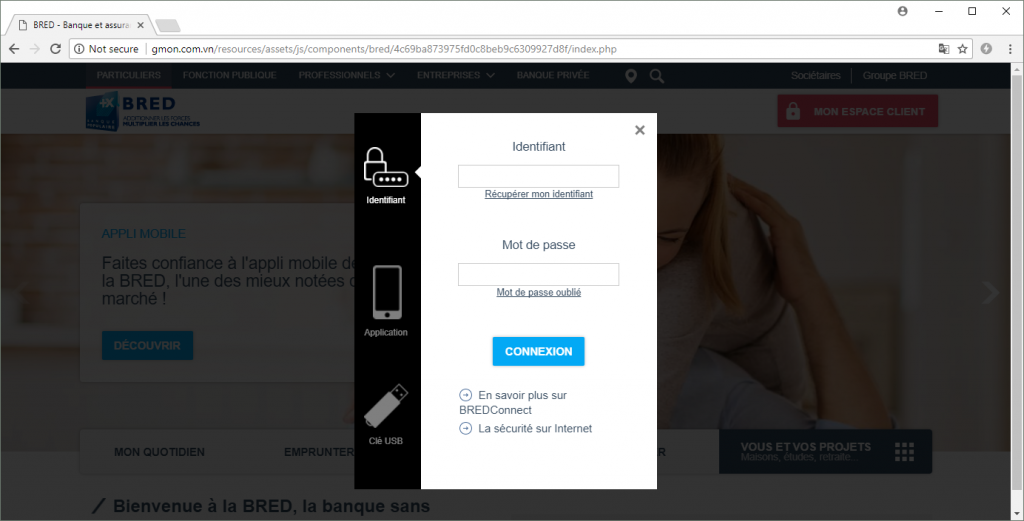
You didn't need to be a brain sturgeon to mullet over and decide this site smelt a bit fishy.
This is not the first time a fishy top-level domain has been used in a phishing attack, although it is pretty rare. Since the .fish and .fishing gTLDs were delegated to the internet back in 2014, there has been barely a whiff of phishing activity on them. In fact, there hasn't been much legitimate activity, either – Netcraft's top million websites contain only one .fish domain and just a sole .fishing domain, and the entire 1.8 billion site survey contains fewer than 6,000 websites that use a .fish or .fishing domain.
A week before blocking this attack, the parser.fish domain was also home to a Netflix phishing site, but this was hosted in a subdirectory on the site and has since been taken down. The parser.fish domain has been registered through Tucows, using its Contact Privacy domain privacy service to prevent the registrant's details being displayed publicly; but this could just be a red herring and doesn't necessarily mean it was registered with fraudulent intent. The fact that the phishing content has also already been removed from its homepage suggests that the site may simply have been compromised rather than having been created specifically for the porpoise of phishing.
The only other fishy phishes in history have been hosted on legitimate (but now defunct) websites that had also been compromised. Earlier this year, a subdirectory on www.vape.fish was found hosting an ANZ phishing site, while last year a different one was found on www.hot-spot.fishing, which used to sell Russian fishing supplies.
Continue reading...

Ripe for crappie puns: A single roe of malicious phishing content hosted on a .fish website.
While a few phishing sites have been found using the .fish and .fishing gTLDs before, parser.fish became the first to host malicious phishing content directly on its homepage. Fraudsters lured unsuspecting suckers to the fishy site, where a cheeky 99-char meta redirect sent them off to a separate phishing site hosted in Vietnam. This then attempted to steal online banking credentials by impersonating the French banking cooperative, BRED.

You didn't need to be a brain sturgeon to mullet over and decide this site smelt a bit fishy.
This is not the first time a fishy top-level domain has been used in a phishing attack, although it is pretty rare. Since the .fish and .fishing gTLDs were delegated to the internet back in 2014, there has been barely a whiff of phishing activity on them. In fact, there hasn't been much legitimate activity, either – Netcraft's top million websites contain only one .fish domain and just a sole .fishing domain, and the entire 1.8 billion site survey contains fewer than 6,000 websites that use a .fish or .fishing domain.
A week before blocking this attack, the parser.fish domain was also home to a Netflix phishing site, but this was hosted in a subdirectory on the site and has since been taken down. The parser.fish domain has been registered through Tucows, using its Contact Privacy domain privacy service to prevent the registrant's details being displayed publicly; but this could just be a red herring and doesn't necessarily mean it was registered with fraudulent intent. The fact that the phishing content has also already been removed from its homepage suggests that the site may simply have been compromised rather than having been created specifically for the porpoise of phishing.
The only other fishy phishes in history have been hosted on legitimate (but now defunct) websites that had also been compromised. Earlier this year, a subdirectory on www.vape.fish was found hosting an ANZ phishing site, while last year a different one was found on www.hot-spot.fishing, which used to sell Russian fishing supplies.
Continue reading...

