Hi everyone, I apologize for two questions in one post but I wanted to take advantage and try to clarify both things.
The reference to Firefox is just an example, I imagine it could be the same for other software.
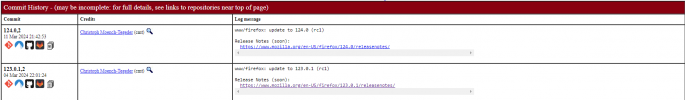
I noticed, while doing a search on the freshports web page, that the installable version of Firefox is one number ahead of the latest one released, that is, it is 124.0, while on Windows it gives me 123.0.1 as the latest one.
Why does this happen if a version has not yet been released by the manufacturer?
Then I see another thing that isn't clear to me: for example, that 123.0.1 is identified in the commit history as (rc1) but it wasn't definitive?
Also, what does the number after the comma mean?
I guess I'm getting confused so I ask you to please explain to me how releasing package versions works.
Finally I wanted to ask you: how safe is the freebsd package installation system? Couldn't a package be modified by inserting malicious code capable of intercepting what is being typed and perhaps even exfiltrating sensitive data such as that of a home banking system?
A browser in this case would be perfect.
Is integrity verification performed constantly by the security team? Can we be trusted?
These are probably silly questions but I would like an expert opinion on the matter if possible.
Thank you all
The reference to Firefox is just an example, I imagine it could be the same for other software.
I noticed, while doing a search on the freshports web page, that the installable version of Firefox is one number ahead of the latest one released, that is, it is 124.0, while on Windows it gives me 123.0.1 as the latest one.
Why does this happen if a version has not yet been released by the manufacturer?
Then I see another thing that isn't clear to me: for example, that 123.0.1 is identified in the commit history as (rc1) but it wasn't definitive?
Also, what does the number after the comma mean?
I guess I'm getting confused so I ask you to please explain to me how releasing package versions works.
Finally I wanted to ask you: how safe is the freebsd package installation system? Couldn't a package be modified by inserting malicious code capable of intercepting what is being typed and perhaps even exfiltrating sensitive data such as that of a home banking system?
A browser in this case would be perfect.
Is integrity verification performed constantly by the security team? Can we be trusted?
These are probably silly questions but I would like an expert opinion on the matter if possible.
Thank you all