The Financial Crimes Enforcement Network (FinCEN), a department of the US Treasury that combats financial crimes such as fraud and money laundering, recently released a report stating that "nearly $24 million in likely fraudulent activity" involved known Tor network nodes. The proportion of fraud that involves Tor is increasing rapidly: according to the report, October 2007 to March 2013 saw an increase of 50% in Tor-related fraud reports, whereas the most recent and much shorter period of March 2013 to July 2014 saw an increase of 100%. The report, which is not public, was obtained by computer security journalist Brian Krebs.
Tor is a piece of open-source software that attempts to provide online anonymity using a technique known as "onion routing". Messages sent by the user, such as HTTP requests from the user's web browser, are sent across the Tor network, instead of being sent directly to the destination server. Before a user sends a message, it is encrypted several times, along with information describing how the message should be routed through a virtual circuit across the Tor network. Circuits consist of a series of three randomly-selected Tor nodes: an entry node, a middle node and an exit node. The user's traffic enters the Tor network at the entry node. Each successive node is able to remove a single layer of encryption, which also reveals the next node to send the message to – akin to peeling the layers of an onion. When the message reaches the exit node, the final layer of encryption is removed and it is sent out across the Internet to its final destination. A similar procedure applies to messages travelling in the opposite direction back to the user, such as HTTP responses.
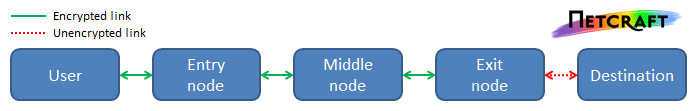
A diagram showing the nodes and the links between them in a Tor circuit. Although Tor does not encrypt the communication between the exit node and destination itself, it can be encrypted by the applications using Tor – for example, the user's web browser could use HTTPS instead of HTTP.
At no single point in the circuit are the source IP address, destination IP address and contents of the message all known to an eavesdropper simultaneously. To reduce the chance that users can be de-anonymized, Tor attempts to avoid picking nodes that share the same operator when creating circuits. This makes it difficult, but perhaps not impossible, for the identity of a particular user to be discovered. For example, an attacker who can observe a user's traffic as it both enters and leaves the Tor network can carry out a traffic confirmation attack, in which they correlate characteristics such as the timing or volume of the user's traffic, to link the user to the destination server.
Unsurprisingly, the anonymity provided by Tor makes it an attractive tool for fraudsters. For example, a phisher who has tricked users into handing over their online banking credentials might use Tor to log in to the bank's website with the compromised credentials. The bank's log files will show the IP address of the Tor exit node, rather than the phisher's own IP address, making it more difficult for the bank and law enforcement agencies to trace the fraud back to the phisher.
The report from FinCEN examined 6,048 suspicious activity reports (SARs) filed by banks and other financial companies between 2001 and 2014. Of those, 975 involved Tor, totalling $24 million of "likely fraudulent activity". The report goes on to state that "in the majority of the SAR filings, the underlying suspicious activity – most frequently account takeovers – might have been prevented if the filing institution had been aware that their network was being accessed via Tor IP addresses." Even if blocking Tor does not deter phishers from committing fraud entirely, it may cause them to switch to using services that are easier for the authorities to trace, such as open proxy servers or anonymous VPN services.
According to FinCEN's report, banks were only aware that Tor was involved in 3% of cases. Netcraft has visited the websites of the ten financial companies most targeted by phishing in the last six months, using a variety of Tor exit nodes located around the world, to check if any of the companies block Tor.
Position Company Blocks Tor traffic
1 PayPal No, but Tor users must solve a CAPTCHA
2 USAA No
3 AXA Banque No
4 SFR No
5 Wells Fargo No
6 Bank of America No
7 Chase No, but Tor users must use two-factor authentication
8 Lloyds Bank No
9 Banco do Brasil No
10 Cielo No
As shown in the table above, none of login pages we visited blocked Tor traffic outright. For example, the following screenshot shows the appearance of PayPal's login page fetched from a variety of Tor exit nodes:
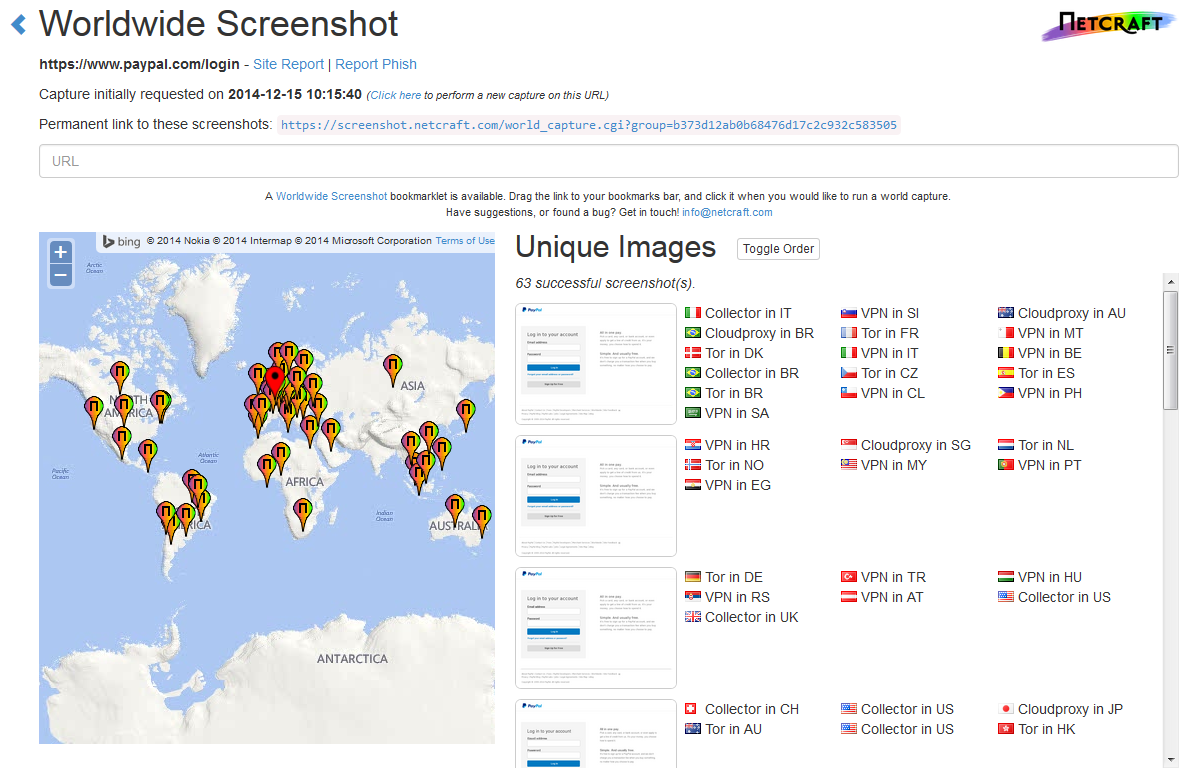
Screenshots of PayPal's login page fetched from several Tor exit nodes located across the world.
However, some of the websites we tested do treat Tor users differently during or after the login process – instead of blocking Tor users outright, they use Tor as an indicator for performing more stringent anti-fraud checks. (It is also possible that some companies perform additional checks that are not visible to end users.)
For example, Chase forces the use of two-factor authentication – by either email, text message or phone call – over Tor. PayPal requires Tor users to solve a CAPCTHA during the login process, which protects against automated attacks such as brute force login attempts, but would not prevent a phisher from manually logging into a victim's account. On the other hand, Lloyds Bank does not appear to visibly treat Tor users any differently to normal users.

A screenshot of the CAPTCHA that PayPal displays to users who attempt to log in over the Tor network.
The Tor Project considers services blanket blocking Tor traffic due to abusive and illegal behaviour by a proportion of its users to be a "threat to Tor's success". It advocates a range of other measures for sites to tackle abusive Tor traffic, including CAPTCHAs, two-factor authentication and establishing trust on a per-user rather than a per-IP basis. However, with the exception of two-factor authentication, most of these measures are targeted at abusive behaviour such as spam and are unlikely to prevent fraudsters from logging into compromised accounts.
Netcraft provides a wide range of countermeasures against phishing to many customers, including two of the world's top ten banks, as well as some smaller institutions at the sharp end of Internet crime – such as three of the largest Bitcoin exchanges and four Nigerian banks. For more information, please contact sales@netcraft.com.
Continue reading...
Tor is a piece of open-source software that attempts to provide online anonymity using a technique known as "onion routing". Messages sent by the user, such as HTTP requests from the user's web browser, are sent across the Tor network, instead of being sent directly to the destination server. Before a user sends a message, it is encrypted several times, along with information describing how the message should be routed through a virtual circuit across the Tor network. Circuits consist of a series of three randomly-selected Tor nodes: an entry node, a middle node and an exit node. The user's traffic enters the Tor network at the entry node. Each successive node is able to remove a single layer of encryption, which also reveals the next node to send the message to – akin to peeling the layers of an onion. When the message reaches the exit node, the final layer of encryption is removed and it is sent out across the Internet to its final destination. A similar procedure applies to messages travelling in the opposite direction back to the user, such as HTTP responses.

A diagram showing the nodes and the links between them in a Tor circuit. Although Tor does not encrypt the communication between the exit node and destination itself, it can be encrypted by the applications using Tor – for example, the user's web browser could use HTTPS instead of HTTP.
At no single point in the circuit are the source IP address, destination IP address and contents of the message all known to an eavesdropper simultaneously. To reduce the chance that users can be de-anonymized, Tor attempts to avoid picking nodes that share the same operator when creating circuits. This makes it difficult, but perhaps not impossible, for the identity of a particular user to be discovered. For example, an attacker who can observe a user's traffic as it both enters and leaves the Tor network can carry out a traffic confirmation attack, in which they correlate characteristics such as the timing or volume of the user's traffic, to link the user to the destination server.
Unsurprisingly, the anonymity provided by Tor makes it an attractive tool for fraudsters. For example, a phisher who has tricked users into handing over their online banking credentials might use Tor to log in to the bank's website with the compromised credentials. The bank's log files will show the IP address of the Tor exit node, rather than the phisher's own IP address, making it more difficult for the bank and law enforcement agencies to trace the fraud back to the phisher.
The report from FinCEN examined 6,048 suspicious activity reports (SARs) filed by banks and other financial companies between 2001 and 2014. Of those, 975 involved Tor, totalling $24 million of "likely fraudulent activity". The report goes on to state that "in the majority of the SAR filings, the underlying suspicious activity – most frequently account takeovers – might have been prevented if the filing institution had been aware that their network was being accessed via Tor IP addresses." Even if blocking Tor does not deter phishers from committing fraud entirely, it may cause them to switch to using services that are easier for the authorities to trace, such as open proxy servers or anonymous VPN services.
According to FinCEN's report, banks were only aware that Tor was involved in 3% of cases. Netcraft has visited the websites of the ten financial companies most targeted by phishing in the last six months, using a variety of Tor exit nodes located around the world, to check if any of the companies block Tor.
Position Company Blocks Tor traffic
1 PayPal No, but Tor users must solve a CAPTCHA
2 USAA No
3 AXA Banque No
4 SFR No
5 Wells Fargo No
6 Bank of America No
7 Chase No, but Tor users must use two-factor authentication
8 Lloyds Bank No
9 Banco do Brasil No
10 Cielo No
As shown in the table above, none of login pages we visited blocked Tor traffic outright. For example, the following screenshot shows the appearance of PayPal's login page fetched from a variety of Tor exit nodes:

Screenshots of PayPal's login page fetched from several Tor exit nodes located across the world.
However, some of the websites we tested do treat Tor users differently during or after the login process – instead of blocking Tor users outright, they use Tor as an indicator for performing more stringent anti-fraud checks. (It is also possible that some companies perform additional checks that are not visible to end users.)
For example, Chase forces the use of two-factor authentication – by either email, text message or phone call – over Tor. PayPal requires Tor users to solve a CAPCTHA during the login process, which protects against automated attacks such as brute force login attempts, but would not prevent a phisher from manually logging into a victim's account. On the other hand, Lloyds Bank does not appear to visibly treat Tor users any differently to normal users.

A screenshot of the CAPTCHA that PayPal displays to users who attempt to log in over the Tor network.
The Tor Project considers services blanket blocking Tor traffic due to abusive and illegal behaviour by a proportion of its users to be a "threat to Tor's success". It advocates a range of other measures for sites to tackle abusive Tor traffic, including CAPTCHAs, two-factor authentication and establishing trust on a per-user rather than a per-IP basis. However, with the exception of two-factor authentication, most of these measures are targeted at abusive behaviour such as spam and are unlikely to prevent fraudsters from logging into compromised accounts.
Netcraft provides a wide range of countermeasures against phishing to many customers, including two of the world's top ten banks, as well as some smaller institutions at the sharp end of Internet crime – such as three of the largest Bitcoin exchanges and four Nigerian banks. For more information, please contact sales@netcraft.com.
Continue reading...

