Popular news websites, hotels, pharmacies, gaming sites, and many online banking sites are among millions of websites that are now explicitly flagged as "not secure" by some of the most commonly used browsers.
Current stable versions of Google Chrome and Mozilla Firefox now display a "not secure" warning in the URL bar if a webpage served over an unencrypted HTTP connection requests a user's password – even if the password is usually submitted to a secure (HTTPS) site. This is because an attacker could modify the non-secure HTTP form and cause the user's credentials to be sent elsewhere.
This security feature was first introduced in Firefox 51, which was released on 24 January, and then in Chrome 56, which was rolled out in the weeks following 25 January. Chrome also displays the warning on pages that contain fields for entering credit card numbers.
Banks failing to protect their customers
Surprisingly many banks have failed to react to the new browser behaviour. For example, Santander's Chilean website at http://www.santander.cl can be accessed over an unencrypted HTTP connection, but it displays an online banking login form regardless.

Chrome 56 declares Santander's Chilean website as "not secure". Its login form is served over an unencrypted HTTP connection, which can expose customers' login details to man-in-the-middle attackers.
The contents of the login form are submitted to a secure URL on https://www.santander.cl/, which uses an SSL certificate issued by GeoTrust. This secure connection is therefore protected against man-in-the-middle attacks, but crucially, this security is undermined by www.santander.cl serving its login form over an unencrypted HTTP connection — a man-in-the-middle attacker can simply siphon the customer's credentials from this page before they are even submitted to the secure site.
A few other examples of banking websites that are now marked as "not secure" (and this is not an exhaustive list by any means) include Eagle Bank, Community Bank of Fitzgerald, Diamond Bank, Flora Bank & Trust and Bank of Hamilton.
Ironically, some of these examples display padlock icons on their online banking login forms, despite serving them over unencrypted HTTP connections. This gives a misleading impression of security, although the risks are now made apparent to any user of Firefox 52.
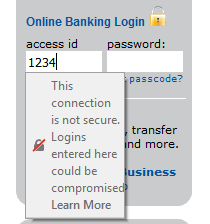
http://www.communitybankoffitz.com displays a padlock on its login form, but Firefox 52 reveals the true situation.
Pharmacy logins exposed
CVS pharmacy — the largest pharmacy chain in the United States, with a parent company that is #7 in the Fortune 500 — also displays its login form over an insecure connection. Interacting with this form in Firefox 52 will cause the "not secure" warning to be displayed much more prominently, beneath whichever field has focus. This is much harder to miss than just the crossed padlock icon in the address bar of Firefox 51.
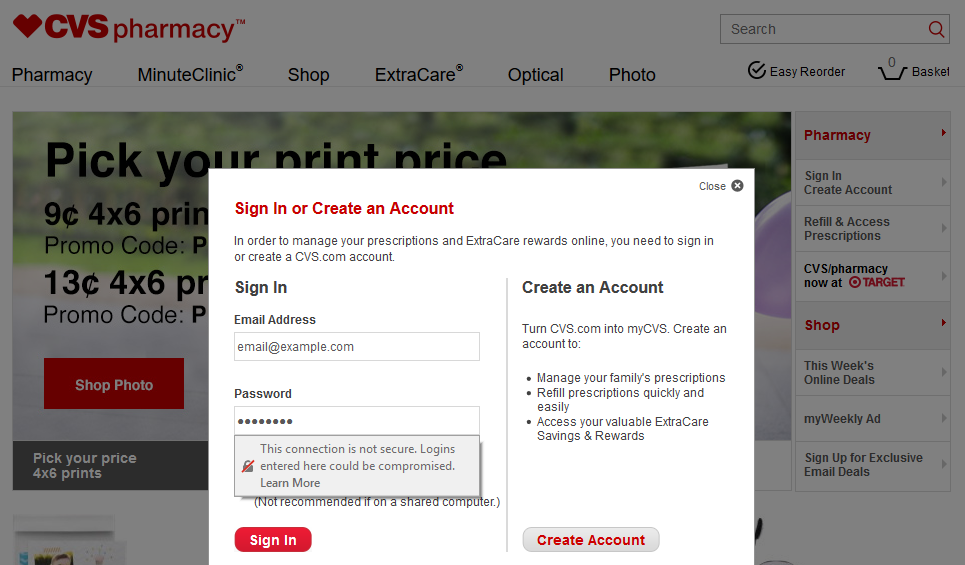
Firefox 52 also objects to the login form on cvs.com.
A customer who signs in to CVS can manage their family's prescriptions online, so any security weakness that potentially exposes their login credentials could raise some regulatory eyebrows. To maintain the privacy and security of Electronic Protected Health Information (EPHI), the HIPAA Security Rule lays out a set of administrative, physical and technical safeguards. The latter is intended to protect communications being intercepted by anyone other than the intended recipient.
Why are browser vendors doing this?
The new behaviour is designed to help users recognise the risk of man-in-the-middle attacks on unencrypted traffic. If an attacker is in a position to be able to change the content of the page when it is served over an unencrypted HTTP connection, then he can easily steal sensitive information from the user – for example, by changing the URL that the form is submitted to, or by injecting JavaScript that silently transmits a copy of the credentials to a server under his control.
Such attacks are entirely plausible, especially with the prevalence of mobile computing. The attacker does not need to infiltrate an ISP or be part of a spy agency in order to view a victim's network traffic – he can simply turn up to a coffee shop and use his phone or laptop to offer a free Wi-Fi network that other customers are likely to use. This would allow him to view and alter the contents of any HTTP form without detection.
The warning feature was previously made available in development releases of both browsers. When it was added to Firefox 46 Developer Edition in January 2016, Mozilla stated that there were no plans to add it to general releases, since developers were ultimately the ones who need to make logins more secure on the sites they build.
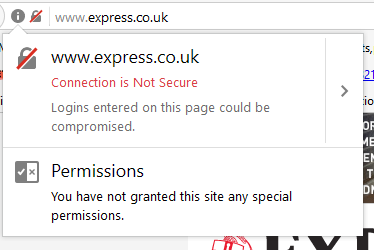
Firefox 51 and later flag the Express news website as not secure.
While the warnings are now displayed to all users of Firefox and Chrome, they are still intended to encourage web designers to update their sites to ensure that sensitive information is always requested over HTTPS. Although the warnings are only shown in a limited set of circumstances, Chrome's warnings represent a step towards Google's long-term plan to flag all HTTP sites as "not secure".
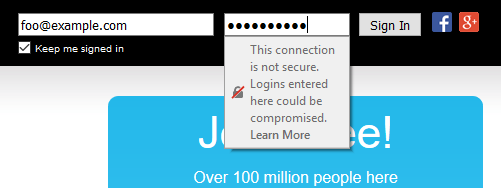
Firefox 52, which was released this week, makes its warnings much more obvious by displaying them inline whenever the user interacts with the offending form.
The new browser behaviour could encourage faster migration to HTTPS by naming and shaming offending websites to their own users. The warnings shown in Firefox 51 and Chrome 56 are rather subtle and could easily be overlooked or not understood by regular users, but the inline warnings now shown in Firefox 52 are easier to interpret and much harder to miss. Chrome 57 is expected to have a similar feature when it is released on March 14. Many websites are therefore expected to react to their "not secure" status in the coming days and weeks.
How many sites are now "not secure"?
Netcraft's Active Sites dataset contains millions of examples where websites serve password fields over unencrypted HTTP connections. All of these sites will be flagged as "not secure" in the latest stable versions of Firefox and Chrome.
Prior to the release of Firefox 51 and Chrome 56, the affected sites would not have caused any warnings to be shown in the URL bar, giving the impression that there were no problems. In contrast, an HTTPS website that uses an expired SSL certificate would display prominent, unmissable warnings, regardless of whether it serves any password fields – even though the connection would arguably be more secure than an unencrypted HTTP connection.
News sites
A wide variety of sites are affected by the new behaviour of Chrome and Firefox, including some of the most popular news websites. This is arguably a good thing, as being affected will encourage them to adopt better security measures.
Fox News visitors (foxnews.com) currently receive the warning when logging in. Although Fox News credentials are ordinarily submitted to a secure server at https://signin.foxnews.com, the login form itself is served over an unencrypted HTTP connection, and so there is an opportunity for a man-in-the-middle attacker to steal any credentials entered on this page:
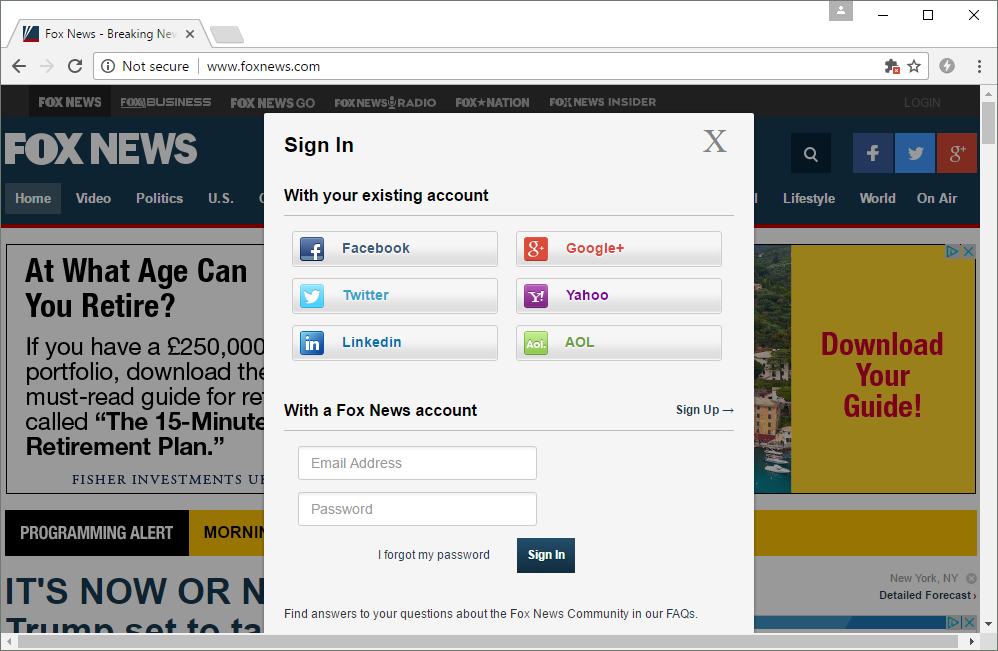
Fox News: One of the most popular news sites that has yet to resolve its "not secure" status.
Some of the news websites that make use of Gigya for customer identity management are also flagged as not secure. This includes the Irish Examiner, the Independent, and the Express. Again, although Gigya's service only accepts credentials via a secure login URL similar to https://accounts.us1.gigya.com/accounts.login, the pages that send these credentials are not secure.
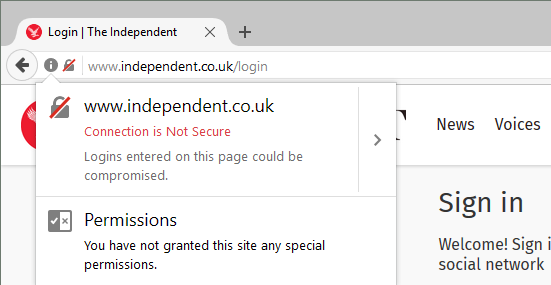
Gigya only accepts passwords over an HTTPS connection, but the Independent website serves its login form over HTTP. This is ripe for mischief.
Baidu
Chinese search engine Baidu is one of the most frequently visited HTTP sites that is now marked as "not secure" by Chrome and Firefox. Unlike Google, its homepage does not use HTTPS by default, and so a significant number of users are likely to see http://www.baidu.com/ flagged as being "not secure" when they try to log in.
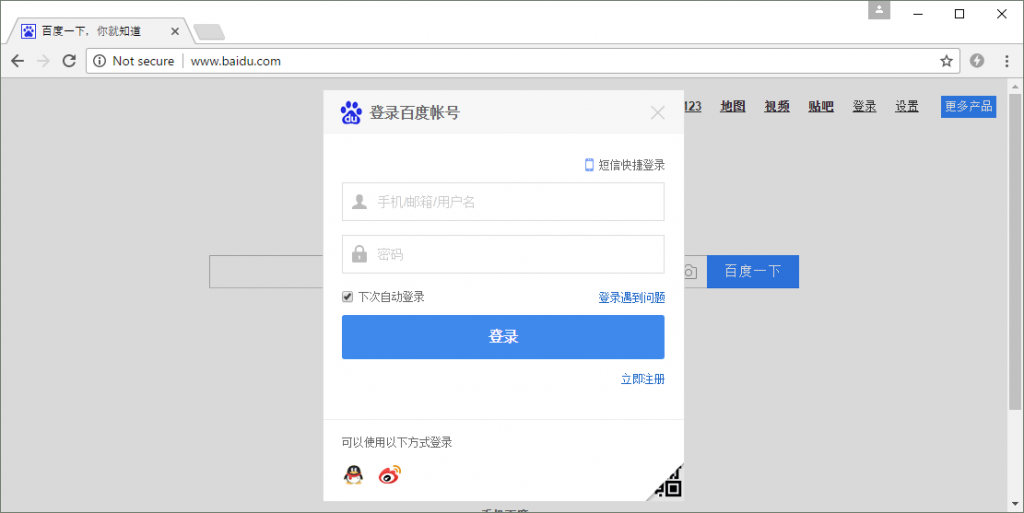
Baidu: Login credentials vulnerable to man-in-the-middle attacks.
Not all Baidu users will be vulnerable, however, as any visit to its HTTPS site at https://www.baidu.com/ will cause Baidu's HTTP Strict Transport Security policy to kick in. This will force the user's browser to use HTTPS for all subsequent visits for at least the next two days, thus ensuring that the login form will be served over a secure connection.
Unfortunately, Baidu's 2-day HSTS policy can only take effect after the user has visited the HTTPS site, rendering all new and infrequent users vulnerable to MITM attacks. This weakness could be resolved by adding baidu.com to Chromium's HSTS preloaded list, which would cause most modern browsers to always use HTTPS, even if the site has never been visited before.
Other high-profile sites that are currently "not secure"
The FIFA website at http://www.fifa.com is instantly flagged as being insecure, even before the login form is made visible to the user. Although this login form submits to a secure URL at https://secure.fifa.com/theclub/login.htmx, the form itself is of course vulnerable to man-in-the-middle attackers who could divert the user's credentials elsewhere.
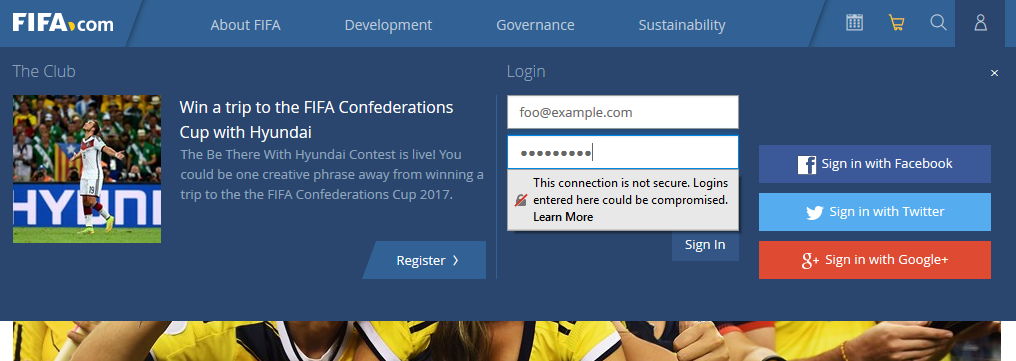
Firefox 52 points out the insecurity in FIFA's dropdown login form at http://www.fifa.com.
Tagged and hi5 are popular social networking sites that are flagged as insecure despite having login forms that are served over secure HTTPS connections. This is because each secure login form is displayed inside an iframe that is displayed by an HTTP site. If the HTTP site were to be man-in-the-middled, the attacker could instead cause this frame to show a spoof login form instead of the intended secure content.
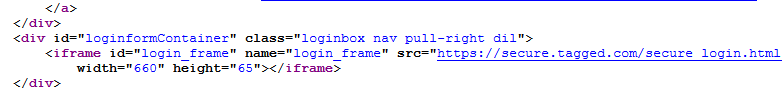
http://tagged.com is flagged as "not secure" because the parent of its secure login frame is served over HTTP.
A few other high profile sites also flagged as "not secure" include those operated by the global lodging company Marriott, Scandinavia's largest airliner SAS, parcel delivery companies Parcelforce and DPD, online gaming sites Miniclip and Bigpoint, and some sites that use Salesforce (e.g. avid.force.com).
What do the affected websites need to do?
Chrome and Firefox will only display the new warnings when they encounter password fields that are served over unencrypted HTTP connections, so the fix is quite straightforward: Make sure these pages are served over HTTPS (using a valid SSL certificate, of course).
While this course of action will make the warning messages disappear, it will not on its own eliminate all types of man-in-the-middle attacks. For instance, most HTTPS sites are vulnerable to trivial connection hijacking attacks that can be exploited whenever a user inadvertently tries to access the secure site over HTTP. This "SSL stripping" vulnerability can easily be resolved by implementing an appropriate HTTP Strict Transport Security (HSTS) policy, yet only a small percentage of HTTPS sites actually do this.
Further protection can be sought by using HSTS preloading, which ensures that a site's HSTS policy is distributed to supported browsers before the user's first visit. Going a step further, HTTP Public Key Pinning can prevent fraudsters using mis-issued SSL certificates to carry out man-in-the-middle attacks, but incredibly few sites have dared to use this feature – partly because it can backfire spectacularly if website administrators get it wrong.
It is also debatable whether the browsers' new warnings will help in all cases. A man-in-the-middle attacker who is able to change the contents of an HTTP login form may be able to prevent the warnings from being displayed, simply by using an ordinary text field instead, or perhaps by using Flash, JavaScript or a HTML5 Canvas to emulate the behaviour of a password field.
Users of Chrome 56 and Firefox 51 also might not notice the subtle "not secure" warnings displayed by these versions, and so an attacker who has man-in-the-middled a login form may still be able to carry out a viable attack as long as the login form continues to be served over HTTP.
However, Firefox 52 (and soon Chrome 57) will make the warnings much easier to notice, and this is likely to drive the security of the web in the right direction. Directly naming and shaming insecure websites to their own users is potentially one of most powerful ways of encouraging companies to make better use of HTTPS, which will ultimately make it harder for hackers to carry out man-in-the-middle attacks.
Continue reading...
Current stable versions of Google Chrome and Mozilla Firefox now display a "not secure" warning in the URL bar if a webpage served over an unencrypted HTTP connection requests a user's password – even if the password is usually submitted to a secure (HTTPS) site. This is because an attacker could modify the non-secure HTTP form and cause the user's credentials to be sent elsewhere.
This security feature was first introduced in Firefox 51, which was released on 24 January, and then in Chrome 56, which was rolled out in the weeks following 25 January. Chrome also displays the warning on pages that contain fields for entering credit card numbers.
Banks failing to protect their customers
Surprisingly many banks have failed to react to the new browser behaviour. For example, Santander's Chilean website at http://www.santander.cl can be accessed over an unencrypted HTTP connection, but it displays an online banking login form regardless.

Chrome 56 declares Santander's Chilean website as "not secure". Its login form is served over an unencrypted HTTP connection, which can expose customers' login details to man-in-the-middle attackers.
The contents of the login form are submitted to a secure URL on https://www.santander.cl/, which uses an SSL certificate issued by GeoTrust. This secure connection is therefore protected against man-in-the-middle attacks, but crucially, this security is undermined by www.santander.cl serving its login form over an unencrypted HTTP connection — a man-in-the-middle attacker can simply siphon the customer's credentials from this page before they are even submitted to the secure site.
A few other examples of banking websites that are now marked as "not secure" (and this is not an exhaustive list by any means) include Eagle Bank, Community Bank of Fitzgerald, Diamond Bank, Flora Bank & Trust and Bank of Hamilton.
Ironically, some of these examples display padlock icons on their online banking login forms, despite serving them over unencrypted HTTP connections. This gives a misleading impression of security, although the risks are now made apparent to any user of Firefox 52.

http://www.communitybankoffitz.com displays a padlock on its login form, but Firefox 52 reveals the true situation.
Pharmacy logins exposed
CVS pharmacy — the largest pharmacy chain in the United States, with a parent company that is #7 in the Fortune 500 — also displays its login form over an insecure connection. Interacting with this form in Firefox 52 will cause the "not secure" warning to be displayed much more prominently, beneath whichever field has focus. This is much harder to miss than just the crossed padlock icon in the address bar of Firefox 51.

Firefox 52 also objects to the login form on cvs.com.
A customer who signs in to CVS can manage their family's prescriptions online, so any security weakness that potentially exposes their login credentials could raise some regulatory eyebrows. To maintain the privacy and security of Electronic Protected Health Information (EPHI), the HIPAA Security Rule lays out a set of administrative, physical and technical safeguards. The latter is intended to protect communications being intercepted by anyone other than the intended recipient.
Why are browser vendors doing this?
The new behaviour is designed to help users recognise the risk of man-in-the-middle attacks on unencrypted traffic. If an attacker is in a position to be able to change the content of the page when it is served over an unencrypted HTTP connection, then he can easily steal sensitive information from the user – for example, by changing the URL that the form is submitted to, or by injecting JavaScript that silently transmits a copy of the credentials to a server under his control.
Such attacks are entirely plausible, especially with the prevalence of mobile computing. The attacker does not need to infiltrate an ISP or be part of a spy agency in order to view a victim's network traffic – he can simply turn up to a coffee shop and use his phone or laptop to offer a free Wi-Fi network that other customers are likely to use. This would allow him to view and alter the contents of any HTTP form without detection.
The warning feature was previously made available in development releases of both browsers. When it was added to Firefox 46 Developer Edition in January 2016, Mozilla stated that there were no plans to add it to general releases, since developers were ultimately the ones who need to make logins more secure on the sites they build.

Firefox 51 and later flag the Express news website as not secure.
While the warnings are now displayed to all users of Firefox and Chrome, they are still intended to encourage web designers to update their sites to ensure that sensitive information is always requested over HTTPS. Although the warnings are only shown in a limited set of circumstances, Chrome's warnings represent a step towards Google's long-term plan to flag all HTTP sites as "not secure".

Firefox 52, which was released this week, makes its warnings much more obvious by displaying them inline whenever the user interacts with the offending form.
The new browser behaviour could encourage faster migration to HTTPS by naming and shaming offending websites to their own users. The warnings shown in Firefox 51 and Chrome 56 are rather subtle and could easily be overlooked or not understood by regular users, but the inline warnings now shown in Firefox 52 are easier to interpret and much harder to miss. Chrome 57 is expected to have a similar feature when it is released on March 14. Many websites are therefore expected to react to their "not secure" status in the coming days and weeks.
How many sites are now "not secure"?
Netcraft's Active Sites dataset contains millions of examples where websites serve password fields over unencrypted HTTP connections. All of these sites will be flagged as "not secure" in the latest stable versions of Firefox and Chrome.
Prior to the release of Firefox 51 and Chrome 56, the affected sites would not have caused any warnings to be shown in the URL bar, giving the impression that there were no problems. In contrast, an HTTPS website that uses an expired SSL certificate would display prominent, unmissable warnings, regardless of whether it serves any password fields – even though the connection would arguably be more secure than an unencrypted HTTP connection.
News sites
A wide variety of sites are affected by the new behaviour of Chrome and Firefox, including some of the most popular news websites. This is arguably a good thing, as being affected will encourage them to adopt better security measures.
Fox News visitors (foxnews.com) currently receive the warning when logging in. Although Fox News credentials are ordinarily submitted to a secure server at https://signin.foxnews.com, the login form itself is served over an unencrypted HTTP connection, and so there is an opportunity for a man-in-the-middle attacker to steal any credentials entered on this page:

Fox News: One of the most popular news sites that has yet to resolve its "not secure" status.
Some of the news websites that make use of Gigya for customer identity management are also flagged as not secure. This includes the Irish Examiner, the Independent, and the Express. Again, although Gigya's service only accepts credentials via a secure login URL similar to https://accounts.us1.gigya.com/accounts.login, the pages that send these credentials are not secure.

Gigya only accepts passwords over an HTTPS connection, but the Independent website serves its login form over HTTP. This is ripe for mischief.
Baidu
Chinese search engine Baidu is one of the most frequently visited HTTP sites that is now marked as "not secure" by Chrome and Firefox. Unlike Google, its homepage does not use HTTPS by default, and so a significant number of users are likely to see http://www.baidu.com/ flagged as being "not secure" when they try to log in.

Baidu: Login credentials vulnerable to man-in-the-middle attacks.
Not all Baidu users will be vulnerable, however, as any visit to its HTTPS site at https://www.baidu.com/ will cause Baidu's HTTP Strict Transport Security policy to kick in. This will force the user's browser to use HTTPS for all subsequent visits for at least the next two days, thus ensuring that the login form will be served over a secure connection.
Unfortunately, Baidu's 2-day HSTS policy can only take effect after the user has visited the HTTPS site, rendering all new and infrequent users vulnerable to MITM attacks. This weakness could be resolved by adding baidu.com to Chromium's HSTS preloaded list, which would cause most modern browsers to always use HTTPS, even if the site has never been visited before.
Other high-profile sites that are currently "not secure"
The FIFA website at http://www.fifa.com is instantly flagged as being insecure, even before the login form is made visible to the user. Although this login form submits to a secure URL at https://secure.fifa.com/theclub/login.htmx, the form itself is of course vulnerable to man-in-the-middle attackers who could divert the user's credentials elsewhere.

Firefox 52 points out the insecurity in FIFA's dropdown login form at http://www.fifa.com.
Tagged and hi5 are popular social networking sites that are flagged as insecure despite having login forms that are served over secure HTTPS connections. This is because each secure login form is displayed inside an iframe that is displayed by an HTTP site. If the HTTP site were to be man-in-the-middled, the attacker could instead cause this frame to show a spoof login form instead of the intended secure content.

http://tagged.com is flagged as "not secure" because the parent of its secure login frame is served over HTTP.
A few other high profile sites also flagged as "not secure" include those operated by the global lodging company Marriott, Scandinavia's largest airliner SAS, parcel delivery companies Parcelforce and DPD, online gaming sites Miniclip and Bigpoint, and some sites that use Salesforce (e.g. avid.force.com).
What do the affected websites need to do?
Chrome and Firefox will only display the new warnings when they encounter password fields that are served over unencrypted HTTP connections, so the fix is quite straightforward: Make sure these pages are served over HTTPS (using a valid SSL certificate, of course).
While this course of action will make the warning messages disappear, it will not on its own eliminate all types of man-in-the-middle attacks. For instance, most HTTPS sites are vulnerable to trivial connection hijacking attacks that can be exploited whenever a user inadvertently tries to access the secure site over HTTP. This "SSL stripping" vulnerability can easily be resolved by implementing an appropriate HTTP Strict Transport Security (HSTS) policy, yet only a small percentage of HTTPS sites actually do this.
Further protection can be sought by using HSTS preloading, which ensures that a site's HSTS policy is distributed to supported browsers before the user's first visit. Going a step further, HTTP Public Key Pinning can prevent fraudsters using mis-issued SSL certificates to carry out man-in-the-middle attacks, but incredibly few sites have dared to use this feature – partly because it can backfire spectacularly if website administrators get it wrong.
It is also debatable whether the browsers' new warnings will help in all cases. A man-in-the-middle attacker who is able to change the contents of an HTTP login form may be able to prevent the warnings from being displayed, simply by using an ordinary text field instead, or perhaps by using Flash, JavaScript or a HTML5 Canvas to emulate the behaviour of a password field.
Users of Chrome 56 and Firefox 51 also might not notice the subtle "not secure" warnings displayed by these versions, and so an attacker who has man-in-the-middled a login form may still be able to carry out a viable attack as long as the login form continues to be served over HTTP.
However, Firefox 52 (and soon Chrome 57) will make the warnings much easier to notice, and this is likely to drive the security of the web in the right direction. Directly naming and shaming insecure websites to their own users is potentially one of most powerful ways of encouraging companies to make better use of HTTPS, which will ultimately make it harder for hackers to carry out man-in-the-middle attacks.
Continue reading...

