D
Deleted member 55181
Guest
https://zaufanatrzeciastrona.pl/post/wyrafinowany-backdoor-uefi-obecny-takze-w-polskich-sieciach/
Imagine a malicious software that is experiencing not only the system reinstallation, but also the replacement of the hard disk. It was the first time that its use was discovered on a larger scale and everything indicates that some of the victims come from Poland.
Imagine a malicious software that is experiencing not only the system reinstallation, but also the replacement of the hard disk. It was the first time that its use was discovered on a larger scale and everything indicates that some of the victims come from Poland.
ESET has published an extremely interesting report on the technically advanced Trojan-modified UEFI, the successor to the BIOS. This makes the Trojan horse very difficult to detect and remove. According to ESET's report, the majority of victims are government institutions from Central and Eastern Europe, and traffic statistics to the addresses of criminals indicate that many infections take place in Poland. The Russian APT28 group (also known as Fancy Bear, Sednit or Pawn Storm) will be able to become a Russian.
An unusual type of attack
ESET today published an article about a new, unusual Trojan horse, named by the researchers of LoJax. The article is also accompanied by a comprehensive technical report . Why is LoJax so unusual?
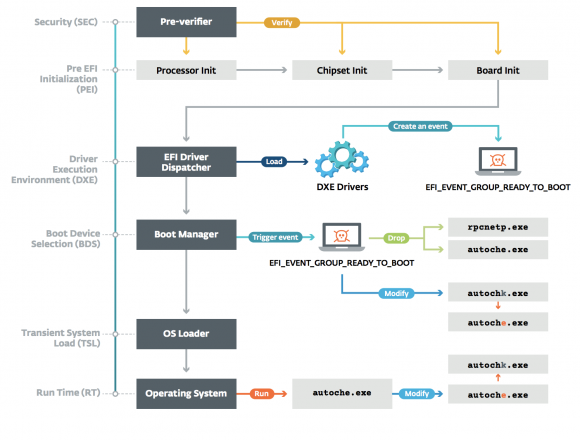
UEFI is software that is an interface between software embedded in computer hardware and the operating system. Previously, this role played the role of the BIOS, but was replaced by a younger and more flexible cousin. Although the concepts of the Trojan horse hidden in UEFI were present at conferences, no one has ever detected such an attack in the real world - until recently, when ESET analysts found their way to LoJax.
LoJax is hidden in the computer's Flash memory as a UEFI module. When the computer starts, it can infect the operating system by storing the appropriate malicious files in it. This means that neither reinstalling the operating system nor replacing the hard disk will not remove the infection. After the reinstallation, the fresh system will be infected the first time you start. Only UEFI re-installation can be removed, which is usually not done by administrators or ordinary users.
LoJax owes its name to the similarity to the LoJack software, pre-installed by many hardware manufacturers, enabling the recovery of the stolen laptop. LoJack is also installed at UEFI level to make it difficult for the thief to remove traces that may lead to the location of the equipment.
If LoJack is installed by the equipment manufacturer, LoJax must take care of itself. Its installation requires earlier taking over the control of the computer by burglars. Then they put on the infected equipment some tools necessary to carry out this process. One of them is the RwDrv.sys driver coming from legal software used to read low-level hardware parameters. Another tool allows you to gather information about the details of the victim's hardware configuration, the third saves the contents of UEFI memory to a file, the fourth modifies the software and updates UEFI with a modified version.
Updating UEFI software varies depending on the configuration of the particular computer. Burglars use configuration errors, default weak settings, or known vulnerabilities to bypass built-in write-protection.

How do you know that the Russians are behind this
ESET researchers point to several reasons why they are convinced that in this case we are dealing with the APT28 group, a well-known defender of Polish government networks. First of all, some C & C servers were previously used in attacks of this group. Secondly, computers infected with LoJax regularly found software such as SedUploader, XAgent and Xtunnel, whose exclusive users are representatives of APT28.
How do you know that the victims are in Poland
ESET states only that government institutions from the Balkans and Central and Eastern Europe dominate the list of victims. In turn, analysis of infection indicators, carried out by Kevin Beaumont using Cisco Umbrella tools (based on passive monitoring of DNS queries, among others to OpenDNS servers), indicates that the majority of traffic to control servers comes from Poland. Kevin also points out that the inquiries are thousands a day.
Just having a quick flick through the IoCs here in Cisco umbrella. A majority of the infected systems appear to be in Poland. There's a lot - thousands of DNS lookups each day. https://t.co/6RdpTZxKzv
- Kevin Beaumont (@GossiTheDog) September 27, 2018
How to defend yourself against an attack
The simplest (though not necessarily the easiest to implement everywhere) way is to activate in the UEFI settings the so-called Secure Boot. This function will allow only digitally signed components to be used - and LoJax does not currently have such a signature.
The second way is to use relatively new processors (equipped with Platform Controller Hub) and the current UEFI version. Such a combination should significantly impede unauthorized modifications of the software to criminals.
Unfortunately, removing the Trojan horse is also not a simple task. Uploading UEFI software is not a trivial task - it can often be easier to replace the motherboard. What's worse, buying a used motherboard may prove to be quite a risk - you can buy it already infected.
How to detect an attack
Undoubtedly, reviewing the connection logs is not a bad idea. ESET provides a list of IP addresses and domains associated with the attack. It is worth remembering that part of the infrastructure coincides with earlier APT28 attacks.
Code:
secao[.]org
ikmtrust[.]com
sysanalyticweb[.]com
lxwo[.]org
jflynci[.]com
remotepx[.]net
rdsnets[.]com
rpcnetconnect[.]com
webstp[.]com
elaxo[.]org
185.77.129[.]106
185.144.82[.]239
93.113.131[.]103
185.86.149[.]54
185.86.151[.]104
103.41.177[.]43
185.86.148[.]184
185.94.191[.]65
86.106.131[.]54
