Hello.  Apparently I am unable to get PF to NAT anything across a wireguard interface. Whether this is an error in my understanding or current PF/Wireguard code is what I am trying to determine here.
Apparently I am unable to get PF to NAT anything across a wireguard interface. Whether this is an error in my understanding or current PF/Wireguard code is what I am trying to determine here.
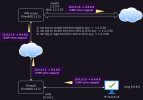
To explain in detail, consider the attached conceptual diagram of my firewall setup, which shows a single packet traversing all the links as culled from tcpdump. The overall idea is to provide VPN services through the firewall for the target machine (10.0.0.15) to the VPN IP target (1.2.3.50).
Both VPN server and firewall are using FreeBSD 13.2-STABLE (a very recent onewith all the errata handled). Both servers use PF and wireguard. On the VPN server, ipforwarding is set to 1 (gateway_enable="YES").
I have tried 3 different configurations of NAT in PF on the VPN server. For reference (in case this diagram turns out wonky) they are:
Tcpdump shows that none of these configuration lines work to change the source address of packets from 10.0.0.15 to 1.2.3.50. Apparently, NAT is not happening at all. Now if I replace the wireguard tunnel with an openvpn tunnel, this NAT configuration works fine:
which is effectively the 2nd example.
Can anyone shed any light on this situation? Thanks in advance.
To explain in detail, consider the attached conceptual diagram of my firewall setup, which shows a single packet traversing all the links as culled from tcpdump. The overall idea is to provide VPN services through the firewall for the target machine (10.0.0.15) to the VPN IP target (1.2.3.50).
Both VPN server and firewall are using FreeBSD 13.2-STABLE (a very recent onewith all the errata handled). Both servers use PF and wireguard. On the VPN server, ipforwarding is set to 1 (gateway_enable="YES").
I have tried 3 different configurations of NAT in PF on the VPN server. For reference (in case this diagram turns out wonky) they are:
Code:
nat log on vtnet0 inet from wg0 to any -> 1.2.3.50
nat log on vtnet0 inet from 10.0.0.15 to any -> 1.2.3.50
nat log on wg0 inet from 10.0.0.15 to any -> 1.2.3.50Tcpdump shows that none of these configuration lines work to change the source address of packets from 10.0.0.15 to 1.2.3.50. Apparently, NAT is not happening at all. Now if I replace the wireguard tunnel with an openvpn tunnel, this NAT configuration works fine:
Code:
nat log on vtnet0 inet from 10.0.0.15 to any -> 1.2.3.50which is effectively the 2nd example.
Can anyone shed any light on this situation? Thanks in advance.