Hi all,
First of all, I would like to mention that I am not very familiar with the networking aspect of FreeBSD using vnet jails.
I already have read mwl's FreeBSD Mastery Jails, but as he mentions, these cases are beyond the scope of the book.
I've an old home i7 with 32GB of RAM that I would like to use to learn more about using
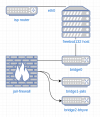
I would like to ask whether my first approach, as per the attached diagram, makes any sense and whether falls under the accepted good practices.
My idea would be to connect the FreeBSD host directly to my ISP router configured in a DMZ.
Force all traffic through a jail, working as a firewall, attached to bridge0.
And use bridge1 and bridge2 to segregate jails and virtualizations.
Anyone has seen a recent practical example of such a configuration?
In any case, I would be more than happy to review any books or articles that you might think would help me.
Thanks in advance
First of all, I would like to mention that I am not very familiar with the networking aspect of FreeBSD using vnet jails.
I already have read mwl's FreeBSD Mastery Jails, but as he mentions, these cases are beyond the scope of the book.
I've an old home i7 with 32GB of RAM that I would like to use to learn more about using
/etc/jail.conf, instead of using sysutils/iocage or sysutils/bastille.I would like to ask whether my first approach, as per the attached diagram, makes any sense and whether falls under the accepted good practices.
My idea would be to connect the FreeBSD host directly to my ISP router configured in a DMZ.
Force all traffic through a jail, working as a firewall, attached to bridge0.
And use bridge1 and bridge2 to segregate jails and virtualizations.
Anyone has seen a recent practical example of such a configuration?
In any case, I would be more than happy to review any books or articles that you might think would help me.
Thanks in advance